Honeypot Crypto Scams: How to Detect and Avoid Them
Honeypot crypto scams trap your funds in tokens you can't sell. Learn how honeypot smart contracts work, the latest scam variants in 2026, and the best tools to detect them before you invest.
![Honeypot Crypto Scam: How to Detect & Avoid Them [2026 Guide]](/images/blog/Blog_Default_Banner.png)
Introduction

It’s early 2025 and you’re knee-deep in peak meme coin mania. A big crypto influencer just tweeted about a hot new meme coin that’s the absolute bee’s knees. He then shows some obscure screenshots as proof that Elon Musk/CZ/Barron Trump holds huge bags.
FOMO kicks in. You rush over to your favorite decentralized trading tools, find the contract address and insta-buy.
From the outside, everything looks legitimate. There seems to be ample liquidity, a big market cap, a chart that keeps going up, and a growing number of wallet holders.
Soon enough, you’re ready to take some profit. You try to sell, but your transaction fails or gets blocked. Nothing goes through. Horrifyingly, you see only one wallet can withdraw. Then comes the red line down. The entire market cap is gone in one fell swoop. Good game, well played. You’ve just gifted your crypto to a honeypot scam, Web3’s equivalent of quicksand or a venus fly trap.
Each year, billions of dollars of digital assets are stolen from crypto investors in brilliantly nefarious ways, such as address poisoning.
Honeypot scams are a significant and growing contributor to that figure, particularly among meme coin traders on decentralized exchanges (DEXs) like we explained in the scenario above.
This guide breaks down exactly how honeypot scams work, the different types you will encounter in 2026, how to detect them before you invest, and the tools that can keep you safe.
Crypto Honeypot Scams
Download the complete PDF guide covering honeypot smart contract mechanics, scam variants in 2026, detection tools, and how to protect your crypto from honeypot traps.
What Is a Honeypot in Crypto?
There’s an important distinction to draw between a Web3 and Web2 honeypot:
- In traditional cybersecurity, a honeypot is a decoy system designed to attract attackers and study their behavior. Security teams have used this concept since the 1990s to detect intrusions and improve defenses.
- In Web3 and cryptocurrency, the concept has been inverted. Instead of catching hackers, the bad guys are calling the shots, using crypto honeypot to trap overzealous investors.
A scammer deploys a smart contract that appears to function like any normal token. You can buy it. You can see other wallets buying it. The price chart shows momentum.
But the contract contains hidden logic that prevents anyone except the deployer from selling. The mechanism varies: some use blacklists, others use hidden sell taxes of up to 100%, and some manipulate internal balances so your tokens become worthless even if you hold them.
The key difference from cybersecurity honeypots is intent.
Security honeypots exist to defend systems. Crypto honeypots exist solely to steal funds.
Solana Meme Coin Honeypots
Bought low cap meme coins on Solana last year? Sorry for your loss.
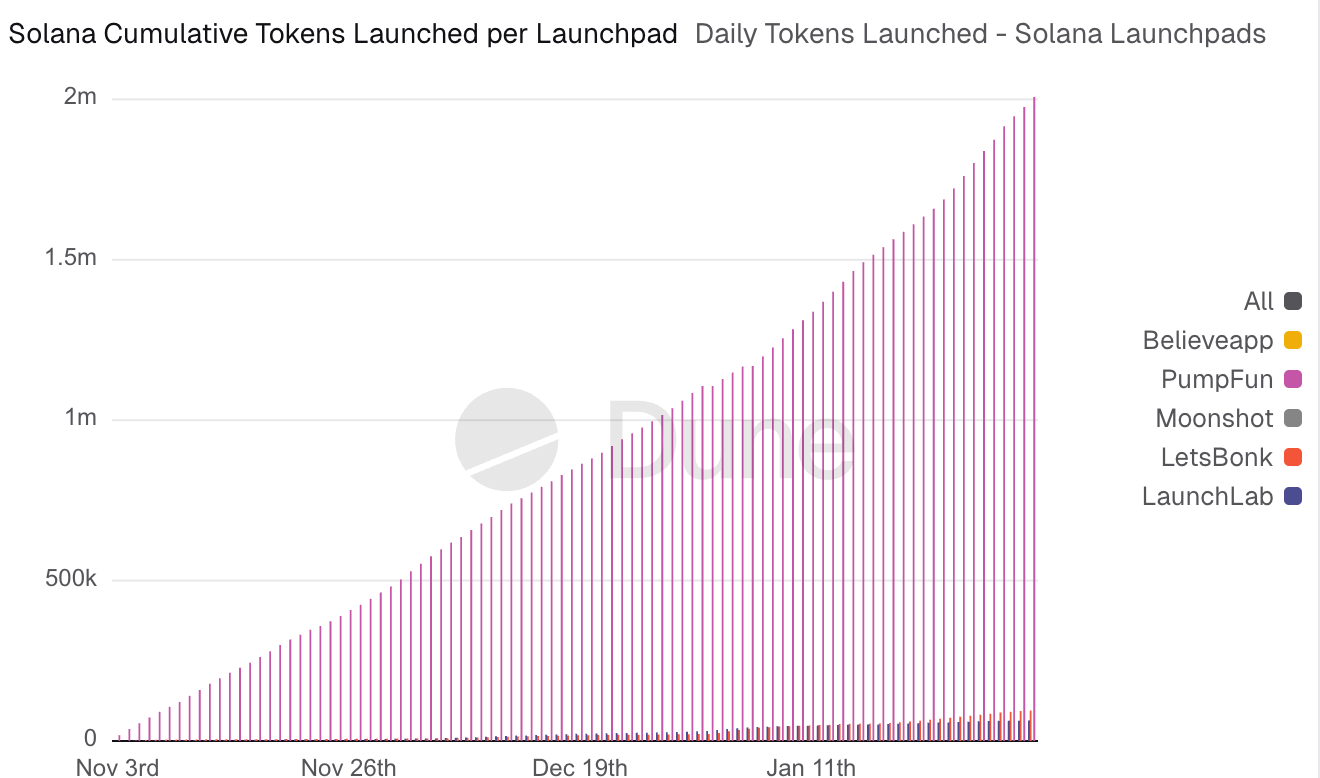
Source: Dune
The insane rise of Pump.fun and other launchpads in 2025 meant that even a non-technical person could launch a token in minutes. While its early days created insane greed which made a lot of overnight millionaires, this soon led to scammers trying to extract as much money from crypto traders as possible, employing every trick in the book.
Solidus Labs found 98.6% of over 7 million Pump.fun tokens were scams, rug pulls or pump-and-dumps, with only 97,000 (1.3%) holding over $1,000 liquidity; 93% of Raydium pools showed soft rug pulls. Solana’s high speed and low fees fueled this frenzy.
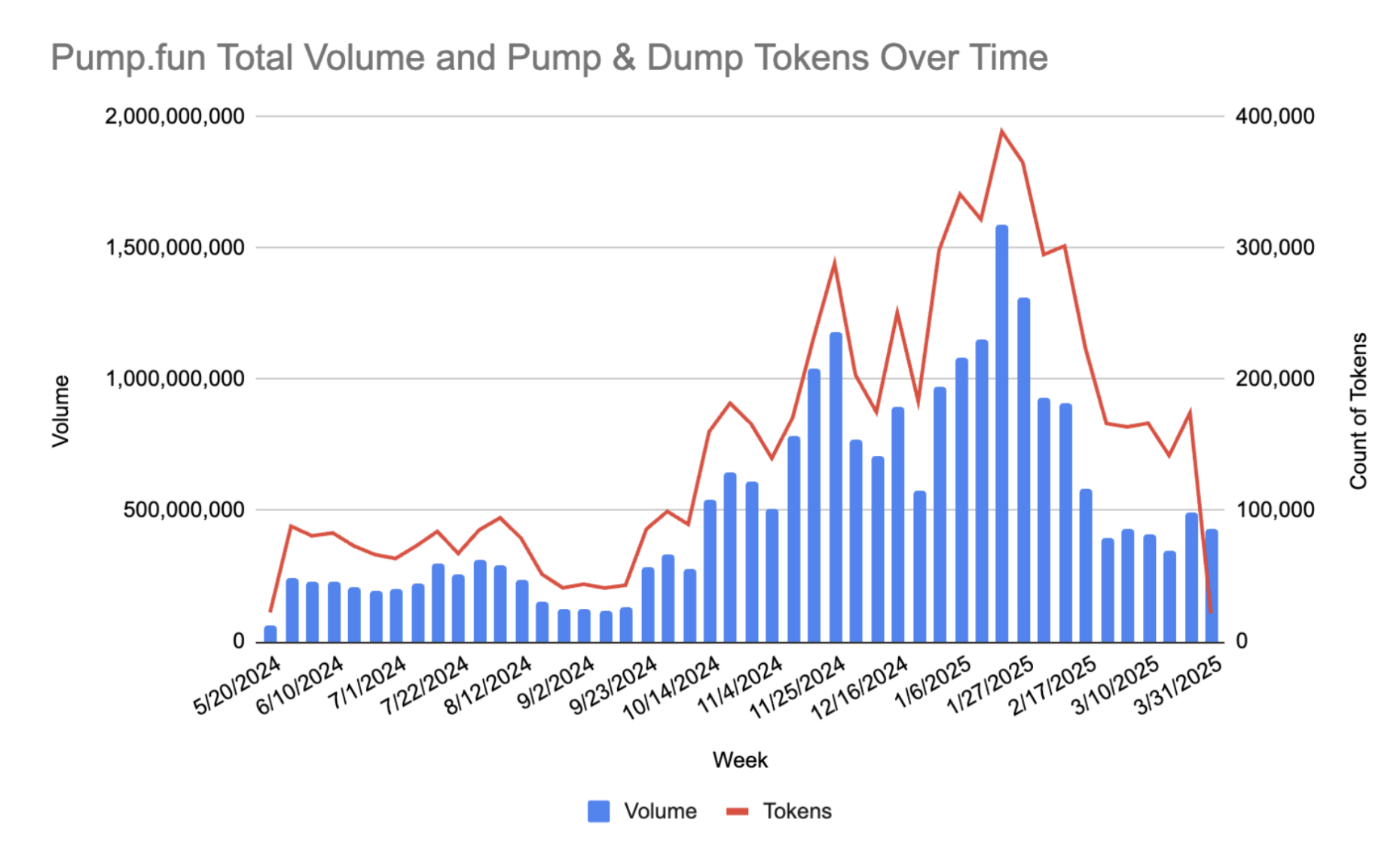
Source: Solidus
In this environment of “buy first, look later”, a barrage of Solana meme coin honeypot scams lured traders into too-good-to-be-true pumps where you can buy but cannot sell or only sell at a near-total loss. Scammers deploy a meme token, seed small liquidity, and push aggressive shills so the chart looks like an early rocket.
The contract restricts selling via dev-only permissions, blacklists, or extreme taxes, trapping victims.
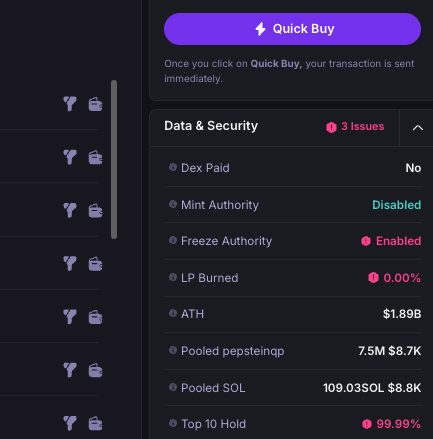
Next time you buy a meme coin on Solana, do this to reduce honeypot risk:
- Check Mint Authority and Freeze Authority — If the mint authority is enabled, more tokens can be created. If Freeze authority is enabled, that means it’s likely a honeypot and your tokens can be locked.
- Inspect the liquidity pool — Go for pools where the funds are “locked” (stuck for months) or “burned” (gone forever). If less than 100% of the LP is burned, you’re in trouble.
- Top Token Holders — Stay away from tokens where the top 10 hold more than 15% of total supply. However, keep in mind that some scammers spread their coins early to hundreds of bot wallets.
- Test it yourself first — Buy a tiny amount (like $5), then try selling it right away. If it fails, run—it’s likely a trap.
- Run scanner tools — Use free sites like RugCheck or Solana Tracker (this is not a recommendation) to spot red flags like “non-sellable” warnings.
- Skip pure hype plays — If there’s no full website, roadmap, or named team, just Telegram spam, it’s probably fake. Also, keep in mind that a website can now be vibecoded in minutes.
- Stay skeptical — Assume every new meme coin is a scam until you prove otherwise. Better safe than rugged.
How Crypto Honeypot Scams Work: Step by Step
While variations exist, honeypot scams follow a predictable lifecycle. Understanding each stage helps you recognize the trap before it closes.
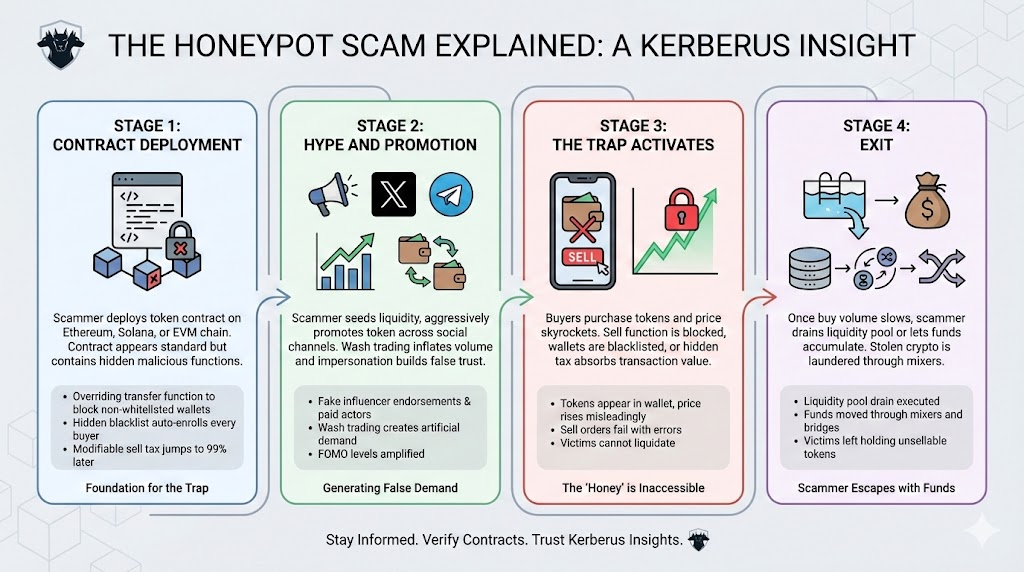
Stage 1: Contract deployment
The scammer, typically a shady developer with Solidity or Rust experience, deploys a token contract on Ethereum, Solana or an EVM-compatible blockchain such as BNB Smart Chain. The contract looks standard on the surface but contains malicious functions embedded in the sell or transfer logic.
Common techniques include:
- Overriding the transfer function to block non-whitelisted wallets
- Adding a hidden blacklist that auto-enrolls every buyer
- Setting a modifiable sell tax that starts at 0% and later jumps to 99%
Stage 2: Hype and promotion
- The scammer seeds initial liquidity to create a trading pair on a DEX.
- The token then gets promoted aggressively across Telegram groups, X (Twitter) threads, and crypto trading channels, till it reaches… well you.
- In many cases, impersonation attacks are used, with scammers posing as well-known influencers or project founders such as Binance co-founder Changpeng “CZ” Zhao to amplify trust and FOMO levels.
- Wash trading (the same wallets buying and selling aggressively) inflates volume to make the token appear active and in demand.
Paid actors or influencers can also be hired to promote the token. According to a Certik report, in Feb 2024, a single cybercriminal executed at least 9 separate honeypot scams using paid Telegram actors, stealing approximately $3.2 million.
Stage 3: The trap activates
As buyers pile in, the chart shows a skyrocketing price. This is misleading because there are few or no real sell orders. Every buyer’s wallet gets blacklisted, the sell function returns errors, or the hidden tax absorbs the entire transaction value.
From the victim’s perspective, the purchase looks successful. The tokens appear in the wallet. The price keeps rising. It is only when they attempt to sell that the trap reveals itself.
Stage 4: Exit
Once buy volume slows, the scammer executes a liquidity pool drain, or simply lets the trapped funds accumulate. Victims are left holding tokens they cannot sell, with no way out.
The scammer moves the stolen crypto through coin mixers or cross-chain bridges to launder the proceeds.
Types of Honeypot Crypto Scams in 2026
Honeypot scams have evolved well beyond simple smart contract tricks. Here are the variants active in 2026.
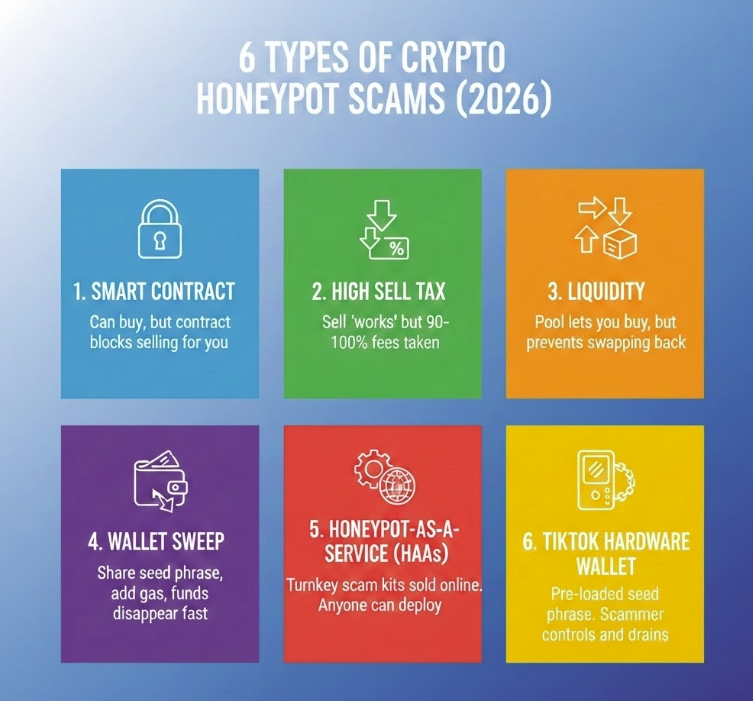
Types of Honeypots in Crypto
1. Smart Contract Honeypots
The classic form. The token’s contract contains a blacklist or whitelist function that silently blocks all wallets except the deployer from executing sell transactions. Some contracts use misleading function names like “ApprovalForAll” that actually add addresses to a hidden restriction list.
CertiK’s research found that a single wallet created 979 honeypot tokens between Aug and Oct 2023, deploying a new scam contract roughly every 30 minutes.
2. High Sell-Tax Honeypots
In this variant, selling is technically allowed, but a concealed tax of 90–100% is applied to every “sell” transaction. The victim sees the sale “succeed” but receives nothing or near-nothing in return. The tax is often modifiable by the contract owner, starting low to pass initial scanner checks before being cranked up once enough victims have bought in.
3. Liquidity Honeypots
Scammers create trading pairs on DEXs with manipulated liquidity pools, often exploiting automated market maker (AMM) mechanics. Buying is permitted, but the contract logic prevents swaps back to ETH, USDT, or other base tokens. The pool appears active with legitimate trading volume, but exits are blocked at the contract level.
4. Wallet Sweeper Honeypots
This is an oldie but goodie. The scammer contacts victims via social media, posing as a beginner who needs help with their non-custodial wallet. They share a seed phrase to a wallet that appears to contain valuable tokens, such as 6,000 USDT.
Here’s the catch: the tokens are on a network where the wallet has no native gas token. When the victim sends ETH or TRX to cover gas fees, an automated sweeper bot instantly drains the deposited funds to a third wallet.
5. Honeypot-as-a-Service (HaaS)
An alarming 2025 trend, rising with others like Drainer-as-a-service platforms. Turnkey scam kits are now sold on the dark web and Telegram, enabling anyone to deploy a honeypot with zero coding knowledge.
Honeypot-as-a-Service kits include pre-built contract templates, marketing materials, liquidity seeding instructions, and laundering guides. Some kits now integrate AI-powered scam tools to auto-generate convincing project websites and social media profiles.
6. TikTok Hardware Wallet Honeypots
Tampered cold wallets are sold on platforms like TikTok and eBay. These devices arrive pre-loaded with a seed phrase that the scammer already controls. The victim loads funds onto the wallet, believing it is secure. The scammer then drains the wallet remotely using the pre-loaded keys.
This variant is known as a supply chain attack, and effective because hardware wallets are supposed to be the most secure storage option in crypto. Always purchase cold wallets directly from the manufacturer.
Top Real-World Honeypot Cases
Squid Game Token (2021)
The most notorious crypto honeypot in crypto history. Capitalizing on the popularity of the Netflix series, SQUID was an early meme coin that rode the wave of popularity that the first season of Squid Game enjoyed during the 2021 bull run.
The token surged to approximately $2,861 before the developers pulled all liquidity on Nov 1, 2021. Investors lost approximately $3.38 million in minutes, with some claiming to have lost “everything”.

Warning signs were present throughout:
- No affiliation with Netflix
- Anonymous developers
- A website riddled with grammatical errors
- Early user reports of being unable to sell
Watchdogs flagged the token as suspicious, but hype and FOMO overrode caution, as they do with all the most successful crypto scams.
Dechat Incident (Feb 2024)
In an unusual case, the DeFi protocol Dechat accidentally posted a honeypot smart contract link on its official social media channels on Feb 26, 2024. Users who interacted with the contract were exposed to financial loss. The team rectified the error quickly, but the incident demonstrated how even legitimate projects can inadvertently expose users to honeypot risks.
Source: https://x.com/zachxbt/status/1762064972966986150
Crypto sleuth ZachBTC soon called the team “clowns” in an online tirade.
Serial Honeypotter (Feb 2024)
Certik found in 2024 that a single threat actor executed at least 9 interconnected honeypot scams via 5 Telegram channels, using paid actors to promote each token. Total losses ran up to approximately $3.2 million and revealed the industrial scale at which honeypot scams now operate.
How to Detect a Crypto Honeypot Token Before You Buy
Unfortunately, no detection method is foolproof. A token can pass every scanner today and become a honeypot tomorrow if the contract is upgradeable. That said, combining multiple checks significantly reduces your risk.
Step 1: Inspect the Smart Contract
Use a block explorer like Etherscan or BscScan to review the token’s contract code. Look for functions that restrict selling, freeze balances, or allow the deployer to modify trading rules after launch. If the contract code is unverified or uses proxy patterns that obscure the logic, treat it as a red flag.
Step 2: Run a Honeypot Checker Tool
Several free tools simulate buy and sell transactions to test whether a token is a honeypot. These checkers support major chains including Ethereum, BNB Smart Chain, and Solana. We compare the most popular options below.
Disclaimer: Kerberus is not affiliated nor endorses any of these software tools. User caution and discretion is advised when interacting with them.
These tools can only detect honeypots that are currently active. A token with clean scan results today can become a honeypot later if the contract owner retains upgrade privileges or modifiable parameters. Use scanner results as one input, not as a green light.
| Tool | Chains Supported | Key Feature | Free? | Limitations |
|---|---|---|---|---|
| Honeypot.is | ETH, BSC, Solana | Buy/sell simulation with tax detection | Yes | Cannot detect post-launch activation |
| TokenSniffer | 40+ EVM chains | Comprehensive audit score, industry gold standard | Yes | 15-min cache delay on updates |
| De.Fi Scanner | Multiple EVM chains | Health score with honeypot detection | Yes | May flag burned liquidity as no liquidity |
| RugDoc | Multiple EVM chains | Risk rating system (color coded) | Yes | Slower update cycle |
| QuillCheck | Multiple EVM chains | 25+ parameter analysis, Telegram bot | Yes | Newer tool, smaller database |
| DetectHoneypot.com | ETH, BSC | Simple single-purpose checker | Yes | Cannot detect upgradeable contracts |
Step 3: Analyze Trading Patterns
Check the token’s transaction history on a block explorer or terminal like DEX Screener. If you see a chart that is entirely green with zero or minimal sell transactions, that is a strong indicator of a honeypot. Legitimate tokens always have a mix of buys and sells.
Step 4: Test-Sell With a Small Amount
If the contract passes scanner checks and the chart looks organic, consider buying a small amount and immediately attempting to sell. If the sell transaction fails, returns significantly less than expected, or requires unusually high slippage, exit immediately.
Step 5: Verify Liquidity Lock Status
Legitimate projects lock their liquidity pool (LP) tokens using services like Unicrypt or Team Finance. If liquidity is not locked, the deployer can remove it at any time, effectively performing a rug pull on top of the honeypot. Check LP lock status before committing funds.
Step 6: Research the Team and Community
Anonymous developers, newly created social media accounts, purchased followers, and no third-party audit are consistent red flags. Legitimate crypto projects provide verifiable team information, publish audits from firms like CertiK or SlowMist, and maintain active community channels with organic engagement.
Honeypot vs. Rug Pull: What Is the Difference?
These two scams are frequently confused, but they operate differently. In practice, there is overlap. Some scammers deploy contracts with both honeypot mechanics and rug pull capabilities, using whichever exit strategy maximizes their take.
| Factor | Honeypot | Rug Pull |
|---|---|---|
| Mechanism | Sell function blocked via contract code | Liquidity removed by developers |
| Timing | Trap is present from deployment or activated early | Occurs after a growth phase, often sudden |
| Detection | Difficult: requires contract analysis or scanner tools | Moderate: check if liquidity is locked |
| Victim experience | Sell transactions silently fail or return nothing | Price crashes to near zero as liquidity disappears |
| Recovery | Extremely rare | Extremely rare |
What to Do if You Have Been Caught in a Honeypot
There’s not much you can do to reverse a honeypot scam, due to the irreversible nature of blockchain transactions. However, taking immediate action can limit further damage and help protect others.
Here are a few things you can do straight away:
-
Revoke token approvals — Use a tool like Revoke.cash to inspect and revoke any permissions you granted to the malicious contract. This prevents the contract from accessing other assets in your wallet.
-
Report the token — Flag the contract on platforms like Etherscan, BscScan, CoinMarketCap, and CoinGecko. Getting a token delisted or flagged helps prevent further victims.
-
File a report with authorities — Depending on your jurisdiction, report the scam to cybercrime agencies such as the FBI’s IC3 (United States) or Europol’s Cybercrime Centre (Europe). While recovery through law enforcement is difficult, official records contribute to broader investigations.
-
Warn the community — Post about the scam in crypto forums, Reddit, and Discord channels. Other traders checking the token may find your warning and avoid the same trap.
-
Consider moving assets to a new wallet — If your wallet interacted with a suspicious dApp or signed unexpected transactions beyond the token purchase, your remaining assets may be at risk. Some honeypot operations are bundled with malware or keyloggers that target browser-based wallets. Transferring funds to a fresh wallet is a precautionary measure.
How Kerberus Protects You From Honeypot Scams

Kerberus provides real-time Web3 security that catches crypto threats before they reach your wallet. Unlike passive scanner tools that require you to manually check each token, Kerberus operates as an active defense layer.
| Feature | Description |
|---|---|
| Transaction simulation | Kerberus simulates every transaction before you sign it, showing you exactly what will happen to your assets. If a token’s contract contains sell restrictions, hidden taxes, or blacklist functions, the simulation flags it before you commit funds. |
| Smart contract risk analysis | The platform analyzes contract code and behavior patterns to identify malicious logic, including the proxy contracts and delayed-activation mechanisms that basic scanner tools miss. |
| Real-time threat detection | Kerberus monitors emerging threats across Web3 and updates its protection continuously. With a perfect 3-year track record and $30,000 coverage, it provides a level of security that manual checking cannot match. |
Install the Kerberus Chrome extension or access its API for enterprise-grade protection.
Frequently Asked Questions
What Is a honeypot crypto scam?
A honeypot crypto scam is a malicious smart contract that allows investors to buy a token but blocks them from selling. The contract contains hidden restrictions, such as blacklists, hidden taxes, or disabled transfer functions that trap funds permanently. Only the scammer’s wallet can withdraw.
How do I check if a token Is a honeypot?
Use a combination of honeypot checker tools (such as Honeypot.is, TokenSniffer, or De.Fi Scanner), manual contract inspection on block explorers, trading pattern analysis, and a small test-sell transaction. No single method is 100% reliable, so layer multiple checks.
Can I Recover Funds Lost in a Honeypot?
In most cases, no. Blockchain transactions are irreversible by design, which is precisely why scammers target crypto users. Whether your funds were in ETH, Bitcoin, or stablecoins, the outcome is the same. Revoke any remaining contract permissions, report the scam, and warn others to prevent further losses.
What Is the Difference Between a Honeypot and a Rug Pull?
A honeypot blocks selling at the smart contract level. A rug pull involves developers executing a liquidity pool drain, crashing the token’s price. Both result in total loss for investors, and some scams combine both techniques.
Are Honeypot Checker Tools Reliable?
They are useful but not infallible. Scanner tools can detect currently active honeypots, but they cannot predict future contract changes. If a token uses an upgradeable proxy contract, the owner can activate honeypot mechanics after the initial scan passes. Always treat scanner results as one data point within a broader due diligence process.
Written by:
Werner Vermaak
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users. His Kerberus articles help readers understand modern Web3 threats, real-world attack patterns, and practical safety practices in an accessible, research-backed way.
Read more about the authorRelated Guides
See more guides
Crypto and Web3's 12 Biggest Narratives in 2026
Feb 20, 2026 • 4 minutes read

How to Use Phantom Wallet Safely: A Beginner’s Guide
Feb 12, 2026 • 4 minutes read

Wake Up! WEF 2026 Cybersecurity Report Sounds Alarm For Crypto Sector
Feb 11, 2026 • 4 minutes read

What is Self-Custody in Crypto? A Complete Beginner's Guide
Feb 9, 2026 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
