Glossary Terms
Browse our comprehensive Web3 security glossary

AI Crypto Scam
An AI crypto scam uses artificial intelligence to create sophisticated cryptocurrency fraud including deepfakes, cloned voices, and personalized phishing.
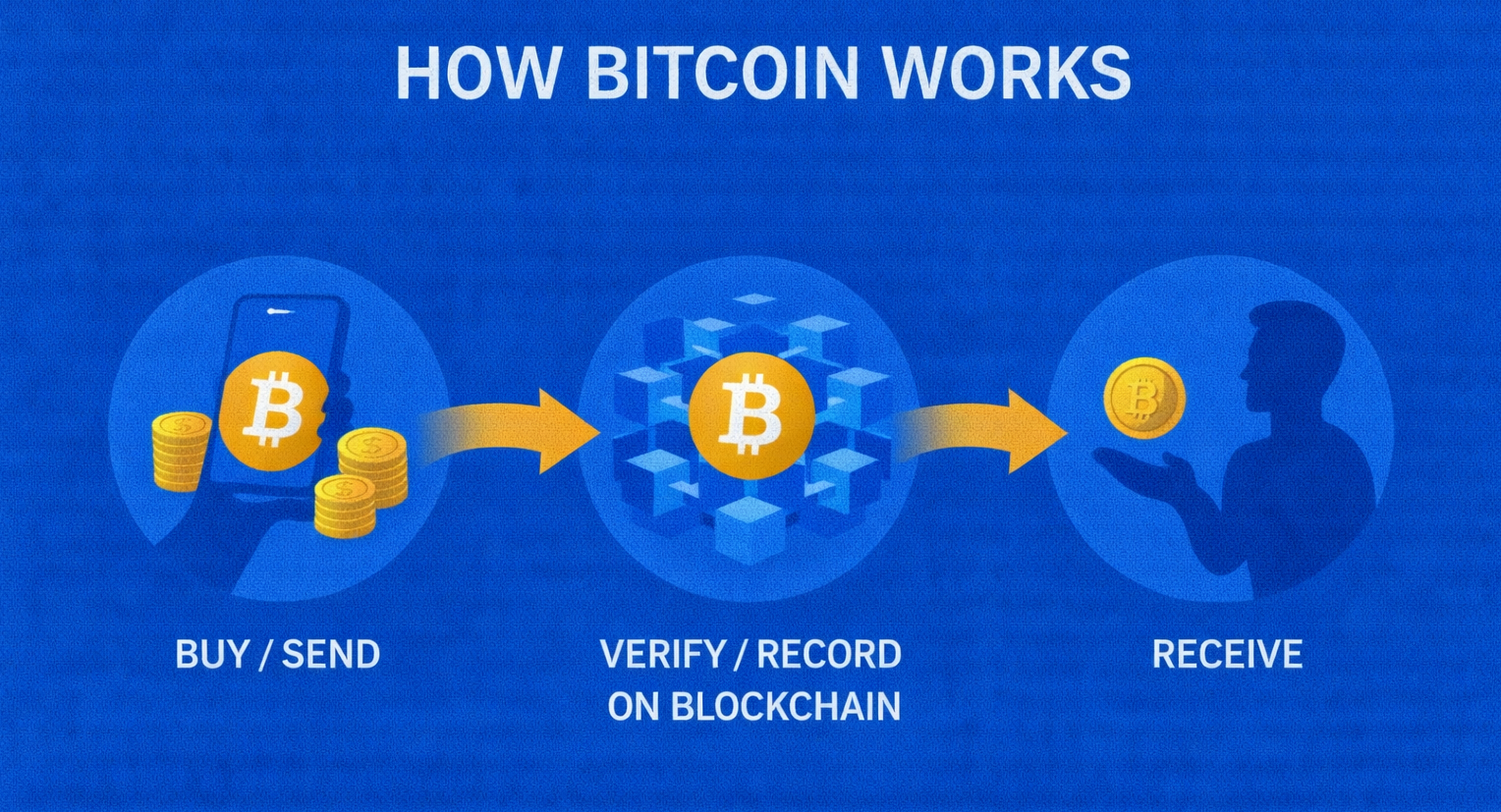
Bitcoin
Bitcoin is the world's first decentralized digital currency, created in 2009 by Satoshi Nakamoto enabling peer-to-peer transactions without intermediaries.
Decentralized Exchange (DEX)
A DEX is a cryptocurrency trading platform that operates through smart contracts, allowing users to trade without centralized intermediaries.
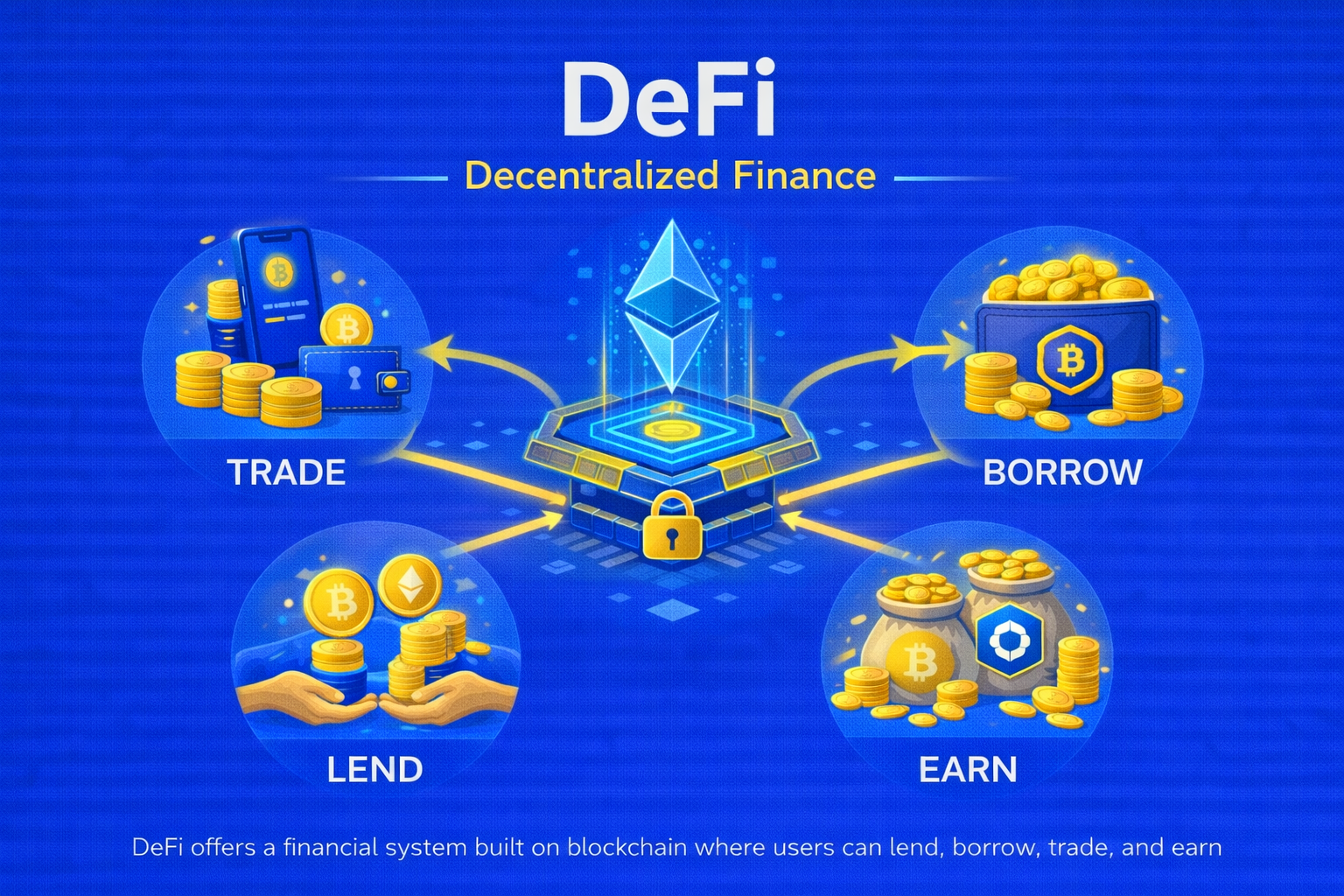
DeFi (Decentralized Finance)
DeFi is a blockchain-based financial ecosystem that recreates traditional banking through smart contracts without intermediaries.

Ethereum Virtual Machine (EVM)
The EVM is a decentralized computing environment that executes smart contracts on the Ethereum blockchain.
Ethereum
Ethereum is a decentralized blockchain platform that enables smart contracts and dApps through its programmable virtual machine.
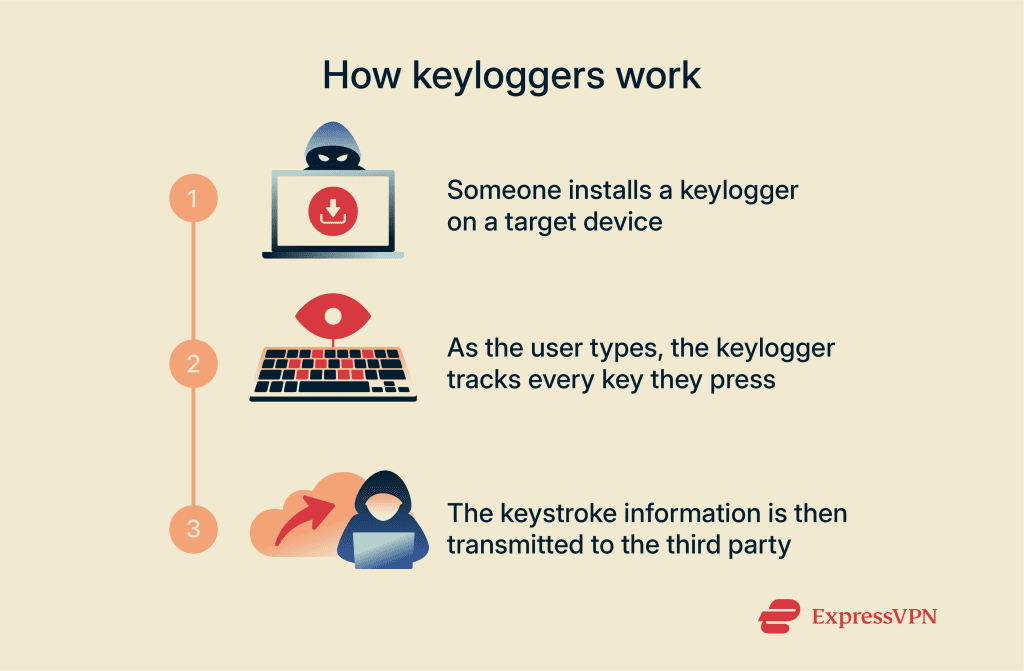
Keylogger
A keylogger is malicious software or hardware that secretly records keystrokes to capture private keys, seed phrases, and passwords.
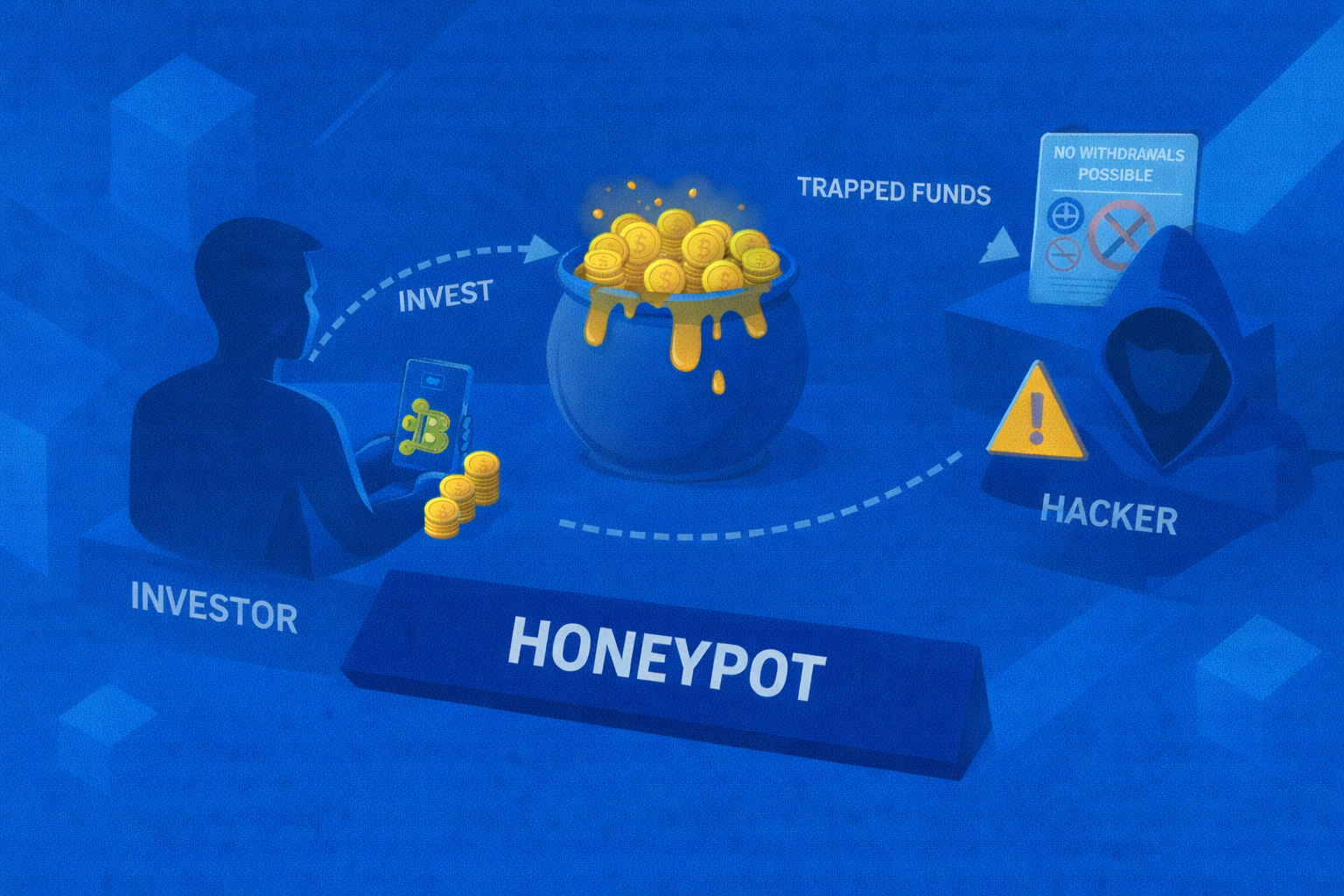
Honeypot
Learn what a honeypot smart contract is and how these crypto traps work to steal funds.

Malware
Malware is malicious software designed to infiltrate devices, steal data, or gain unauthorized control. In crypto, malware often targets private keys and wallets.
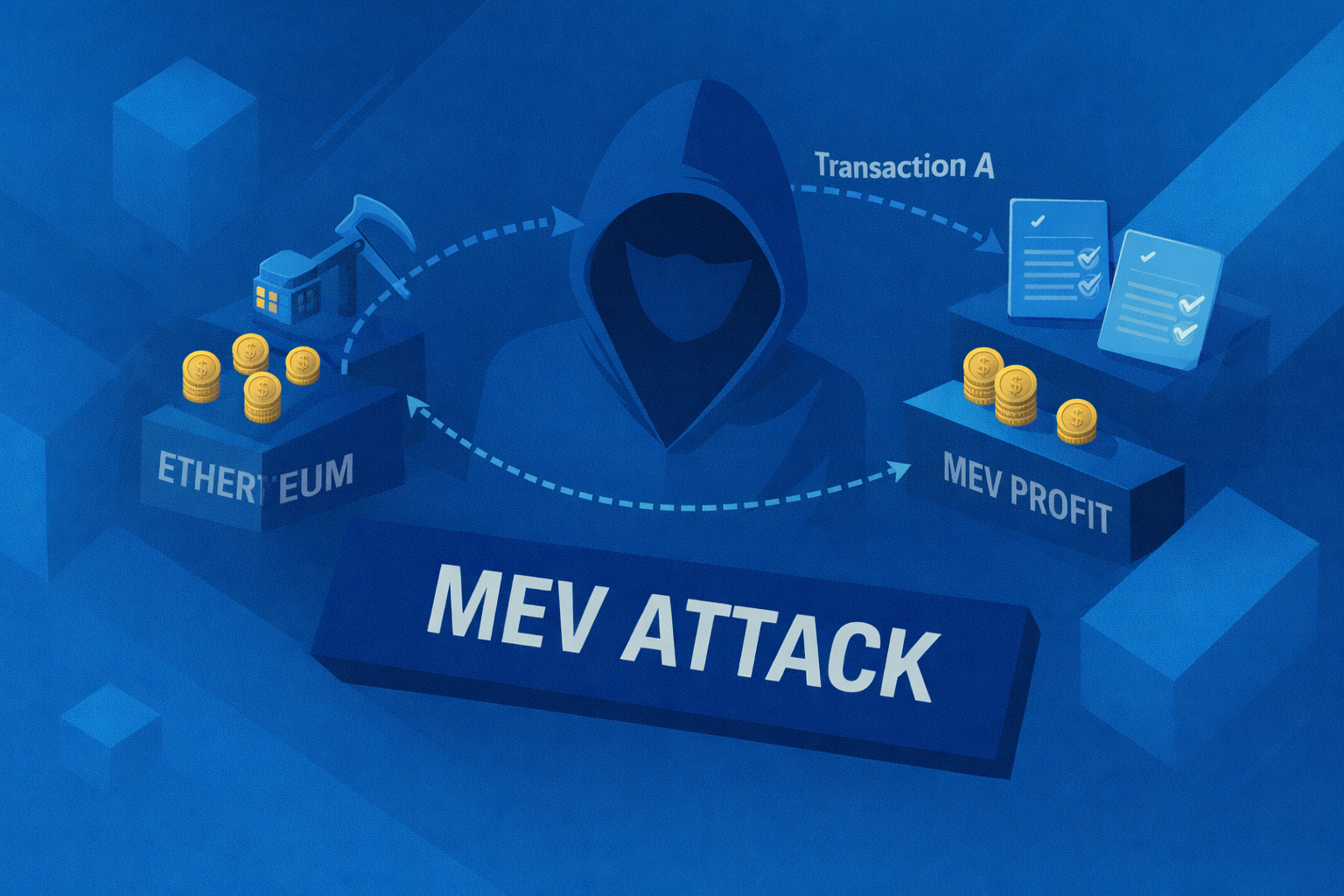
MEV Attack
Learn what an MEV attack is, how it works, and how users can reduce risk in Web3.

Non-Custodial Wallet
A non-custodial wallet gives users complete control over private keys and funds without third-party custody.
Quantum Computing
Quantum computing leverages quantum mechanical phenomena to process information exponentially faster than classical computers for certain problems.
Reentrancy Attack
Learn what a reentrancy attack is and why it remains a critical smart contract risk.

Solana
Solana is a Top 10 ranked high-performance layer-1 blockchain designed for fast, low-cost transactions using Proof of Stake and Proof of History.

Sybil Attack
A Sybil attack is when a single entity creates multiple fake identities to gain disproportionate influence over a decentralized network.

Web3
Web3 is the decentralized internet owned by users. Learn how blockchain, crypto, and dApps work, and the security challenges you face.

Web3 Wallet
A Web3 wallet stores your private keys and crypto. Learn how wallets work, different types, and how to secure them against hackers.

Social Engineering
Social engineering attacks manipulate you into revealing secrets. Learn to spot psychological tricks and protect your crypto assets.

Web3 Security
Web3 security protects you from hacks and scams. Learn about wallet security, smart contract risks, and how to stay safe in crypto.

Phishing
Web3 phishing attacks impersonate trusted sites to steal your keys. Learn to spot fake websites and protect your wallet with Kerberus.

Transaction Poisoning
Transaction poisoning tricks you into copying fake addresses. Learn how this scam works and how to verify recipients with Kerberus.

Smart Contract Vulnerability
Smart contract bugs can cause massive crypto losses. Learn about common vulnerabilities and how to check contracts before investing.

ApprovalForAll Exploit
The setApprovalForAll exploit lets scammers steal all your NFTs. Learn how this attack works and how to manage permissions safely.

Rugpull
Rugpulls happen when developers steal investor funds. Learn to spot exit scams and protect your investments with our guide.

Private Key
Your private key controls your crypto. Learn how it works, why it's crucial for security, and how to keep it safe from theft.

Non-Fungible Tokens (NFT)
NFTs are unique digital assets on the blockchain. Learn how NFTs work, their use cases, and how to protect your collection from theft.

Multisig Wallet
Multisig wallets require multiple keys for transactions, offering better security. Learn how they work and when to use them for your crypto assets.

Malicious Approvals
Malicious approvals let scammers drain your wallet. Learn to spot dangerous permissions and revoke them to secure your crypto.

Front-End Compromise
Attackers hack dApp front-ends to steal your crypto. Learn how front-end compromises happen and how to verify websites with Kerberus.

Flash-Loan Attack
Flash-loan attacks exploit DeFi protocols for risk-free profit. Learn how these complex attacks work and how to protect your assets.

Fake Airdrop Scam
Fake airdrops promise free tokens to steal your crypto. Learn to spot scam campaigns and protect your wallet from malicious claims.

DaaS (Drainer-as-a-Service)
Drainer-as-a-Service (DaaS) platforms empower criminals to steal crypto. Understand the threat and protect your wallet from organized scams.

Crypto Wallet Drainer
Wallet drainers steal crypto by tricking you into approving transactions. Learn how they work and how to block them with Kerberus.

Cross-Chain Bridge Vulnerability
Cross-chain bridge hacks cause massive crypto losses. Learn how bridge exploits work and how to protect your assets when moving funds.

Address Poisoning
Address poisoning attacks trick you into sending crypto to scammers. Learn how to spot fake addresses and secure your wallet with Kerberus.