Address Poisoning Attacks: How They Scam Web3 Users
Learn how address poisoning attacks work, how to detect them, and protect yourself from losing crypto to lookalike wallet addresses. Complete guide with real case studies.

Introduction
In late December 2025, a very unlucky crypto trader lost a staggering $50 million in USDT due to an address poisoning attack, a simple social engineering scam which is easy to avoid with a Web3 security tool like Kerberus Sentinel3.
Crypto investors lost $3.1 billion in H1 2025 alone in various cryptocurrency hacks and scams ($250m on Solana alone according to a Kerberus report). Most of them rely on the oldest of human weaknesses: deceit and human error.
Most Web3 scam losses involve phishing and social engineering tricks that activate wallet drainer malware, however there’s another very simple crypto deception trick that gets especially profitable when FOMO in bull markets make crypto users less diligent.
Address poisoning (also referred to in crypto as transaction poisoning) exploits Web3 user habits and a sense of familiarity when copying and pasting addresses. While other Web3 attack vectors try and exploit smart contract vulnerabilities, address poisoners deliberately plant lookalike wallet addresses to fool their victims into sending funds to a scam address.

Web3 security researchers over 2 years identified more than 270 million address poisoning attack attempts targeting over 17 million wallets, resulting in at least $83.8 million in losses across Ethereum and Binance Smart Chain (BSC).
In one of the biggest scams of 2024, a whale lost $68 million in wrapped Bitcoin (WBTC) to an address poisoning attack. Fortunately, the scammer returned the money, but not everyone gets lucky!
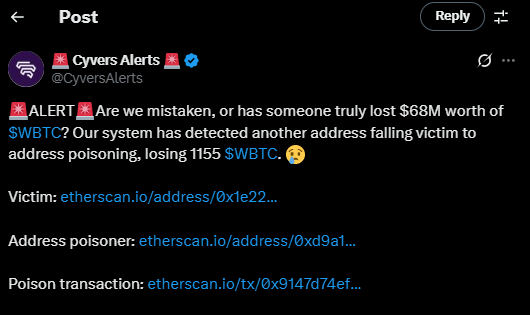
Source: X
Address Poisoning: How It Works (Step by Step)
At its core, this type of attack is a matter of wallet address manipulation. How does this happen? It follows a series of steps that can be identified and mitigated.
Source: Nano Banana
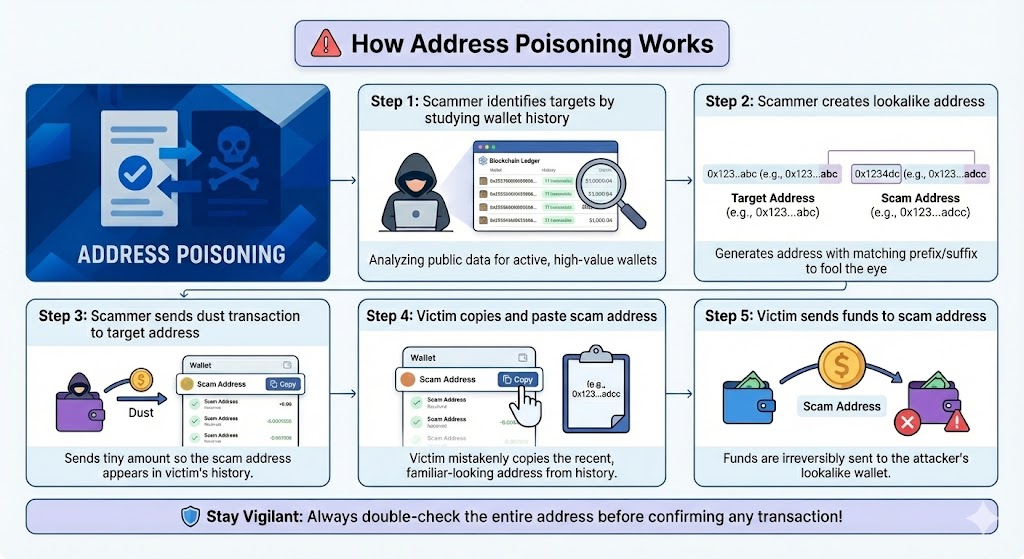
Step 1: Target Acquired
Attackers start by studying a victim’s transaction history and find the address(es) to target. Let’s use an example:
Original Ethereum Address:
0x742d35Cc6634C0532925a3b844Bc454e4638f44e
Step 2: Lookalike address created
The poisoner next creates similar-looking crypto addresses with specialized software called vanity address generators. The fake address will usually have the same first few and last few characters, since many interfaces truncate addresses to those parts.
Scam Ethereum Address:
0x742d353D0000003002000003400003004438f44e
Step 3: Dust to target address
Once the attacker has a fake but lookalike address, they “poison” the transaction history by making tiny or dust transfers from that address to the victim’s wallet.

The transaction leaves a permanent trace on the blockchain and appears in the victim’s transaction history. It then blends in easily in the target’s activity history, especially when displayed in mobile wallets or browser extensions.
Step 4: Victim reuses the scam address
The final parts of the scam relies on simple human error. People make mistakes, and bad actors count on that. Later, the victim checks their transaction history, and copies and pastes what they think is their trusted address. They look the same, but they’re not.

Step 5: Victim sends funds to scam address
Finally, the victim completes the rest of the transaction and unknowingly sends real funds to the attacker.
Cold facts: There is no wallet signature trickery involved. The transaction is fully valid and irreversible.
Why is Crypto Address Poisoning so Successful?
These attacks are not just random; they are systematic and large-scale. They are also very successful for many reasons. In short, address poisoning succeeds because it exploits normal user behavior like below, not technical vulnerabilities.
1. People trust their transaction history
Most users assume that addresses in their transaction history are safe because they were “used before.” Attackers exploit this trust. Especially for high frequency transactions,users who make several transfers are prone to taking shortcuts, increasing their risk of relying on recent transaction history.
2. Users love to copy and paste
Let’s face it, hexadecimal wallet addresses are very long, and nearly impossible to remember or manually type for the average Joe or Jane. For simplicity, users prefer to copy and paste from their transaction history. This creates a loophole that allows attackers to embed a recently created fake wallet address for their own gain.
3. Most wallet interfaces hide the full addresses
Most wallets truncate addresses, only displaying the beginning and ending numbers and letters. If those parts match, users rarely check the full 42-character string.
4. Blockchain transparency helps scammers
While transparency is a core tenet of blockchain, this also has its downside. All wallet activity is viewable on a public blockchain ledger such as Etherscan or Solscan.
This allows address poisoners to:
- Identify very active wallets
- See repeating transfer patterns
- Target users with high balances
5. Bot automation makes address poisoning scalable
Tech-savvy bad actors use sophisticated bots to poison thousands of wallets per hour across multiple blockchains at near-zero cost.
Case Study: How One Address Copy-Paste Cost $50 Million (December 2025)
What happened
On December 20, 2025, a crypto trader lost nearly $50 million in USDT after falling victim to an address poisoning attack, a scam where hackers trick victims into sending funds to a fake wallet address that looks almost identical to the real one.
How the victim was tricked
The attacker first sent a tiny test transaction to the victim, inserting a fake address into the victim’s transaction history. This address matched the first and last few characters of the legitimate address, making it easy to confuse when copying and pasting.
When the trader later transferred the USDT, they accidentally used the poisoned address from their history, sending the funds directly to the scammer. The stolen money was quickly swapped for ETH and laundered through privacy tools like Tornado Cash, making recovery almost impossible, despite the victim’s $1m bounty.
Why the poisoning worked
The attacker used automation to exploit how most wallets display addresses:
-
Spoofed address generation: An automated script created a wallet address that matched the victim’s real destination address in the first five and last four characters.
-
History poisoning: The attacker sent small transactions from this spoofed address to the victim’s wallet, planting it into the victim’s transaction history.
-
The trap: When the trader later copied an address from their history for the big transfer, they likely selected the poisoned look-alike address because many interfaces hide the middle characters with ellipses
How to protect yourself:
Always carefully check wallet addresses before every transaction. Scammers hope that you won’t.
Other Recent Address Poisoning Cases
- In May 2024, a crypto whale lost $68 million worth of Wrapped Bitcoin (WBTC) in a single transaction after being tricked by an address poisoning scam. The attacker mimicked the victim’s transaction history with a lookalike address, leading to a massive loss. All funds were eventually returned after bounty negotiations.
- In August 2025, a wave of address poisoning attacks caused over $1.6 million in losses within a week
- One campaign exposed more than 82,000 crypto wallets to address poisoning, with one user losing $57,000
- Multiple reports show thousands of smaller incidents occur regularly, with losses ranging from thousands to hundreds of thousands of dollars per case
- A Reddit thread detailed how one user lost $700k to address poisoning
Which Chains Are Most Affected By Poisoning?
It makes sense that popular chains with a lot of stablecoin transfers will be the most prized targets since they are the most profitable for attackers. Crypto is a numbers game, and so are their scams.
Address poisoning works on any chain with a transparent transaction history, but it is most common on:
- Ethereum & Layer 2s (Base, Arbitrum, Optimism)
- Solana (increasing rapidly)
- BNB Chain
- Polygon
- Avalanche
- Tron (USDT transfers)
How to Detect Address Poisoning Attempts
The best way to mitigate poisoning attempts is to shut the door that attackers can use to compromise your security.
You’ll need to be vigilant (friendly reminder: this is crypto!) and do your checks and balances to ensure that a compromised address is not lurking in your transaction history and taking that wallet balance down to zero.
Here are some address poisoning red flags to watch out for:

-
Unexpected dust transactions - When a small and unknown transaction is sent to your wallet, always try to verify its origins. It may be a test transaction from someone you know, or the attacker may be injecting this fake address into your history to lay a future trap.
-
Lookalike addresses: Watch out for addresses that look similar. Scammers generate addresses that mimic legitimate wallet addresses.
5 DIY Steps to Avoid Falling Victim
Here is what you can do to improve your Web3 security and save yourself the pain of being an address poisoning victim.
-
Don’t Trust, Verify
- Users need to develop full-address verification habits, not just the first and last characters.
- Instead of pasting addresses from transaction history, whitelist ones you trust.
- Treat each new or unknown address as a potential threat until proven otherwise.
-
Use Automated, Real-Time Web3 Security Monitoring
Web3 threat detection requires state-of-the-art monitoring and blockchain analysis tools that can spot threats from miles away.
A top Web3 security tool like Kerberus provides 24/7 monitoring to detect malicious addresses and thwart poisoning attacks. Users can choose between a browser extension and API for protection.
-
Improve Your Web3 Wallet Hygiene
Web3 security requires users to be active, and not passive. Regularly update your Web3 wallet’s software and protect your private keys and seed phrases.
Use secure cold storage and multisig wallets. Enable all security features, such as biometric logins. You can never be too careful when it comes to your crypto asset protection.
-
Do a Test Run
Send a minimum amount of crypto to an address before committing a larger amount. This test allows you to prevent a fake address attack.
-
Use ENS or SNS Domains
You can use an Ethereum Name Service (ENS) domain or Solana Name Service as a readable name for your wallet address, such as AliceBob.ETH. It can be memorized and makes it easier to pick out potential address poisoning threats. Of course, be aware that lookalike ENS addresses can also be created.
How Kerberus Active Protection Stops Web3 Address Poisoning
Kerberus’ Sentinel3 extension is an automated, on-chain Web3 protection service that monitors and flags malicious transaction attempts. It has a 99.9% Web3 user protection record since 2023, and provides up to $30,000 in coverage for Web3 transactions, unlike any of its competitors.
Sentinel3’s Active Protection is an autonomous Web3 security system by Kerberus that protects you while you browse Web3 sites with peace of mind.
What to know about Active Protection:
- It operates independently from Kerberus Sentinel3’s core detection services
- It vigilantly monitors your protected wallet addresses on 7 of the most popular chains.
- It actively searches for any attack signs and uses cutting-edge mitigation techniques to keep you safe.
How Kerberus Stops Address Poisoning with Active Protection (3 steps)
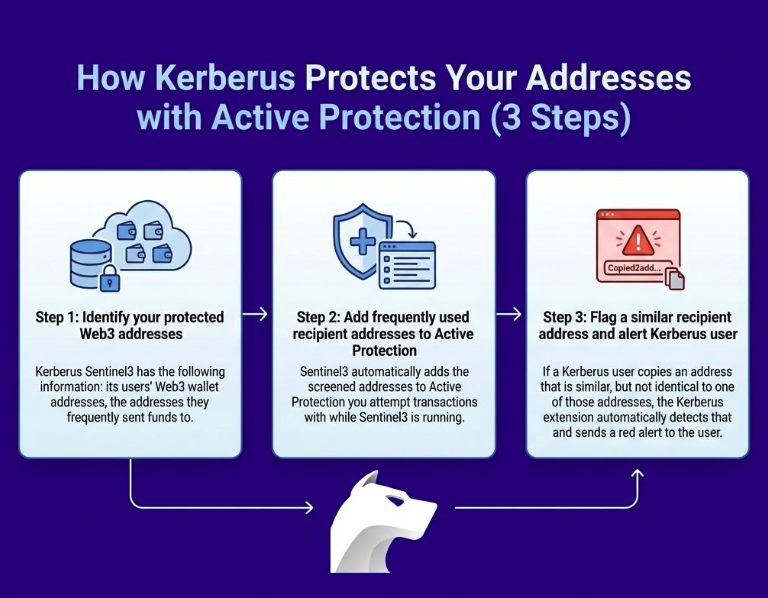
Step 1: Identifies your protected Web3 addresses
Kerberus Sentinel3 has the following information:
- its users’ Web3 wallet addresses
- the addresses they frequently sent funds to
Step 2: Adds frequently used recipient addresses to Active Protection database
Sentinel3 automatically adds the screened addresses to Active Protection you attempt transactions with while Sentinel3 is running.
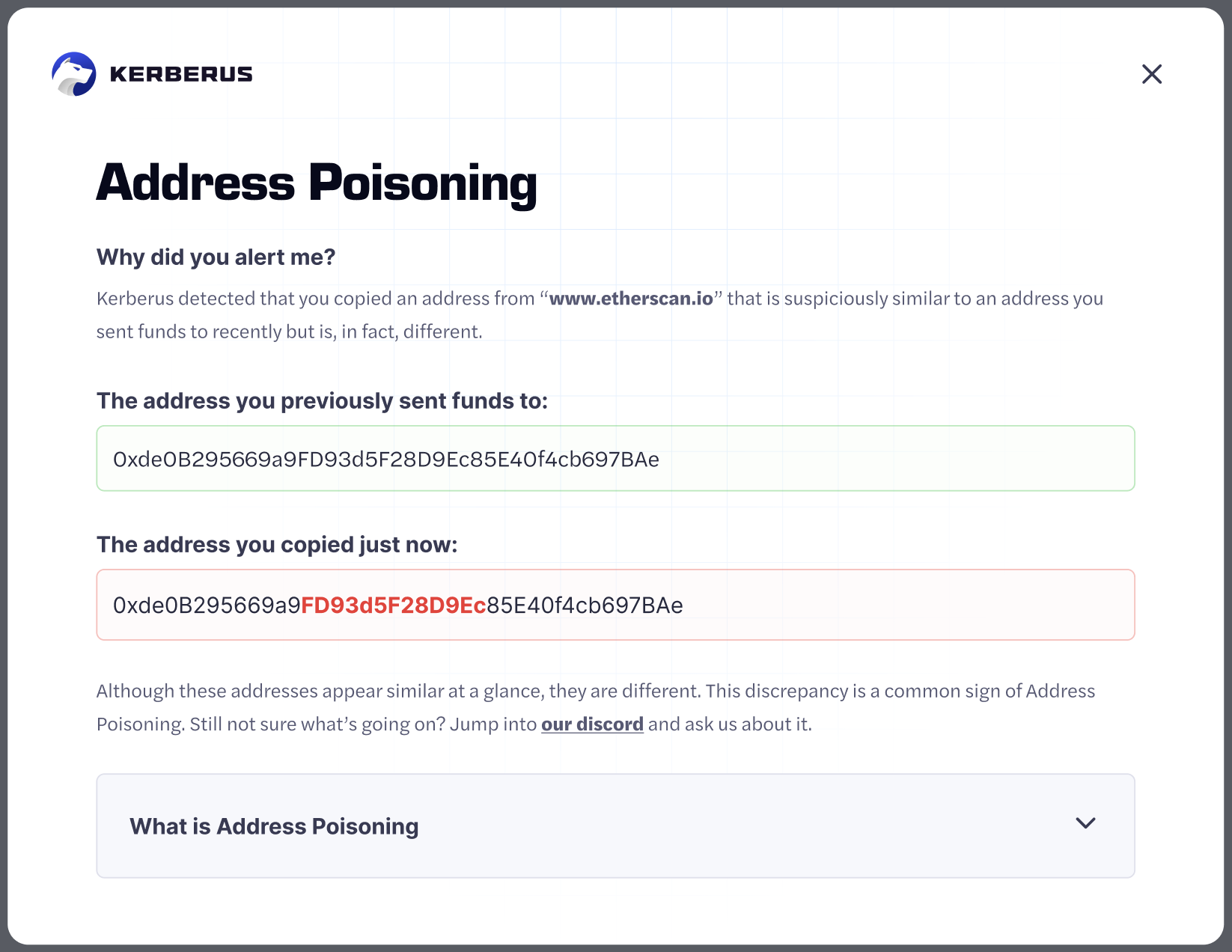
Step 3: Flags very similar recipient addresses and alerts Kerberus user
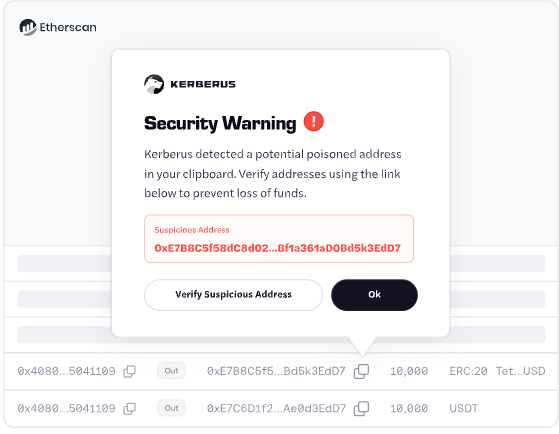
If a Kerberus user copies an address that is similar, but not identical to one of those addresses, the Kerberus extension automatically detects that and sends a red alert to the user, who cancels the transaction.
And just like that, you’ve warded off an address poisoning attack!
Recap
Address poisoning is deceptively simple, but it can cost you a big chunk of your portfolio if you’re not careful.
Follow the best practice tips in this guide to stay safe, by
- verifying your addresses before making transactions
- monitoring your wallet history for scam addresses
- using Web3 security tools like Kerberus to proactively protect you
And here’s an important rule of thumb to heed well: while tools like Kerberus can flag malicious intent, a blockchain cannot. It does what users instruct it to do, and there is no recourse or rollback if someone is tricked into routing their hard-earned cash straight into the pockets of scammers.
Immutability is a feature, not a bug. You are your own bank, and the responsibility in crypto starts and ends with you.
Address Poisoning Knowledge Quiz
Test your knowledge and see how well you understand address poisoning attacks and how to protect yourself
1. What primary vulnerability do address poisoning attacks exploit?
Hint: Think about why a user might accidentally send money to the wrong person without a technical hack occurring.
2. What is the purpose of a 'vanity address generator' in this specific scam?
Hint: Consider how wallet interfaces usually display long hexadecimal strings and what parts remain visible.
3. Why do attackers send 'dust' (tiny amounts of crypto) to the victim's wallet?
Hint: The goal is to trick the user when they go to make a future transaction and look for a past recipient.
4. Which of the following is the most effective way to verify a destination address and avoid poisoning?
Hint: Because attackers can mimic the start and end of an address, where should you look to find the discrepancy?
5. How does the Kerberus 'Transaction Translation' feature assist users?
Hint: This feature acts as a 'preview' of what the transaction will actually do to your assets.
6. True or False: Once a user sends funds to a poisoned address, the blockchain can easily reverse the transaction.
Hint: Consider one of the core characteristics of blockchain technology regarding transaction finality.
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Guides
See more guides
Crypto and Web3's 12 Biggest Narratives in 2026
Feb 20, 2026 • 4 minutes read
![Honeypot Crypto Scam: How to Detect & Avoid Them [2026 Guide]](/images/blog/Blog_Default_Banner.png)
Honeypot Crypto Scams: How to Detect and Avoid Them
Feb 18, 2026 • 4 minutes read

How to Use Phantom Wallet Safely: A Beginner’s Guide
Feb 12, 2026 • 4 minutes read

Wake Up! WEF 2026 Cybersecurity Report Sounds Alarm For Crypto Sector
Feb 11, 2026 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
