Top 26 Web3 Security Threats In 2026
Comprehensive guide to all 26 Web3 security threats in 2026. Learn about social engineering, phishing attacks, private key compromise, malicious smart contracts, wallet drainers, DeFi exploits, and how to protect yourself from these critical risks.

Introduction
The first half of 2025 saw over $3.1 billion stolen across Web3, with access control exploits accounting for $1.83 billion and phishing schemes spiking to $600 million. According to a Kerberus report, over $250 million was lost on Solana alone.
Want to stay safe and hold on to your crypto in 2026? Then understanding the different types of Web3 security threats you’ll be facing in an online environment that seems to be reinventing itself on a daily basis is essential for protecting your assets.
From wallet drainers to honeypots, malicious approvals to AI deepfakes and fake airdrops, social engineering to quantum computing, the road to crypto riches is riddled with dangers lying in wait to trip you up and steal your coins or NFTs.
Why is this though?
Whether markets are up and down, hackers and scammers understand the value of crypto better than most retail investors, and it’s not just monetary. They know in the long run, price usually goes up, and also that they send value to anyone, anywhere in the world, without a centralized intermediary stopping them.
While in some cases, blockchains and stablecoin providers have frozen bad actor accounts and rolled back transactions, any intermediary interference is deemed a big no-no in crypto, and therefore avoided at all cost.
As a result, crypto wallets are fair game and top targets for highly sophisticated, often state-sponsored hacker groups, who will try to trick you with various types of cybersecurity attacks to get your credentials, private key or worse, drain your Web3 wallet with one click.
Using an active real-time Web3 security defense layer like Kerberus in 2026 is a no-brainer to keep you safe.
Kerberus has a perfect 3 year record with no losses, $30,000 coverage, and will actively protect you against threats you don’t even know about. Individuals simply need to install its popular Chrome extension, while businesses can access its API.
Here are various types of Web3 security threats that will be coming for your wallet in 2026. There is some crossover between certain threats as they’ve evolved over time to attack from multiple vectors. Buckle up and dial in!
Threat Type 1: Social Engineering & Phishing

Social engineering is probably the biggest security Threat Type to casual Web3 users today, because they’re often so simple by nature and rely on you doing all the hard work. These attacks have evolved far beyond simple fake emails and use complex techniques to trick their victims.
Bad actors are incredibly resourceful, well-funded and continue to create new attack vectors to stay ahead of security firms and regulators. They often strike where protection is lowest, such as social media accounts or email services.
They’ll use tricks involving fake sites, impersonations, romance, airdrops in the process.
Phishing and social engineering may appear to be indistinguishable from each other. However, phishing is in fact a subset of social engineering. Most of the latter’s instances require phishing of some kind though, and you’ll find phishing DNA in the biggest crypto hacks of all time.
How Phishing Attacks Have Changed Since 2020
Phishing-as-a-Service Platforms
Professional phishing operations now offer turnkey solutions sold directly on the internet or Dark Web. These tools enable armies of hackers to launch mass campaigns with minimal technical knowledge.
These platforms provide:
- Pre-built phishing site templates
- Automated victim targeting
- Cryptocurrency laundering services
- Technical support for scammers

1. Cloned Websites or Dapps
Racing to your laptop to search for a hot new token or project that just dropped? Scammers are banking on you doing so and not paying attention.
They create and publish:
- Perfect replicas of legitimate decentralized applications (Dapps)
- Nearly identical URLs with minor character differences or cyrillic lettering
These Dapps and websites are often professionally designed, and now with the rise of sophisticated vibe coding tools like Lovable and Cursor, they can clone a site and have it up and running within minutes.
Always check that the URL is correct. Bookmark trusted domain URLs where you can and use some of the incredible resources in our Web3 security tools guide to keep yourself safe.
Here’s an example of scammers using cyrillic characters to dupe traders.
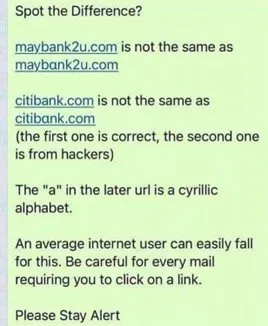
2. Address Poisoning
Address poisoning is a growing DeFi security threat where scammers trick you into sending crypto to the wrong address. Attackers generate wallet addresses that look almost identical to ones you regularly use, then “poison” your transaction history with tiny or zero-value transfers from their fake address. When you later copy an address from your history, you might accidentally paste the scam address instead of the correct one, sending funds permanently to the attacker.

This scam recently made headlines when a trader lost nearly $50 million after copying a poisoned address from their transaction history and sending a large USDT transfer to the scammer’s wallet. To defend against address poisoning, always verify the full address string, avoid copying addresses from your history, and save trusted addresses in a secure address book rather than relying on recent activity lists.
Read our full Address Poisoning Guide to avoid becoming another statistic.
3. Pretexting and Impersonation on Social Channels
Pretexting scams work by creating a convincing and urgent false scenario. Attackers pose as customer support agents, security team members, or platform administrators and claim they need sensitive information to resolve a problem.
In crypto, pretexting commonly involves requests for seed phrases, private keys, or transaction approvals under the excuse of account verification or recovery. Legitimate services never ask for seed phrases. Any request for them, regardless of the explanation, signals an immediate security threat.
The playbook: Fake Discord and Telegram support accounts are created. Victims are then targeted and contacted by project team members who pretend to be from a big exchange like Coinbase, or a wallet brand like Ledger.
These scammers are ultra-convincing, and use official-looking emails and social media accounts (often with 1000s of bought fake followers) on platforms like X, Instagram and Linkedin who try to redirect them to join a private channel or support account on TG or Discord.
They often employ urgent messages to create artificial time pressure which leads to the user making a mistake.
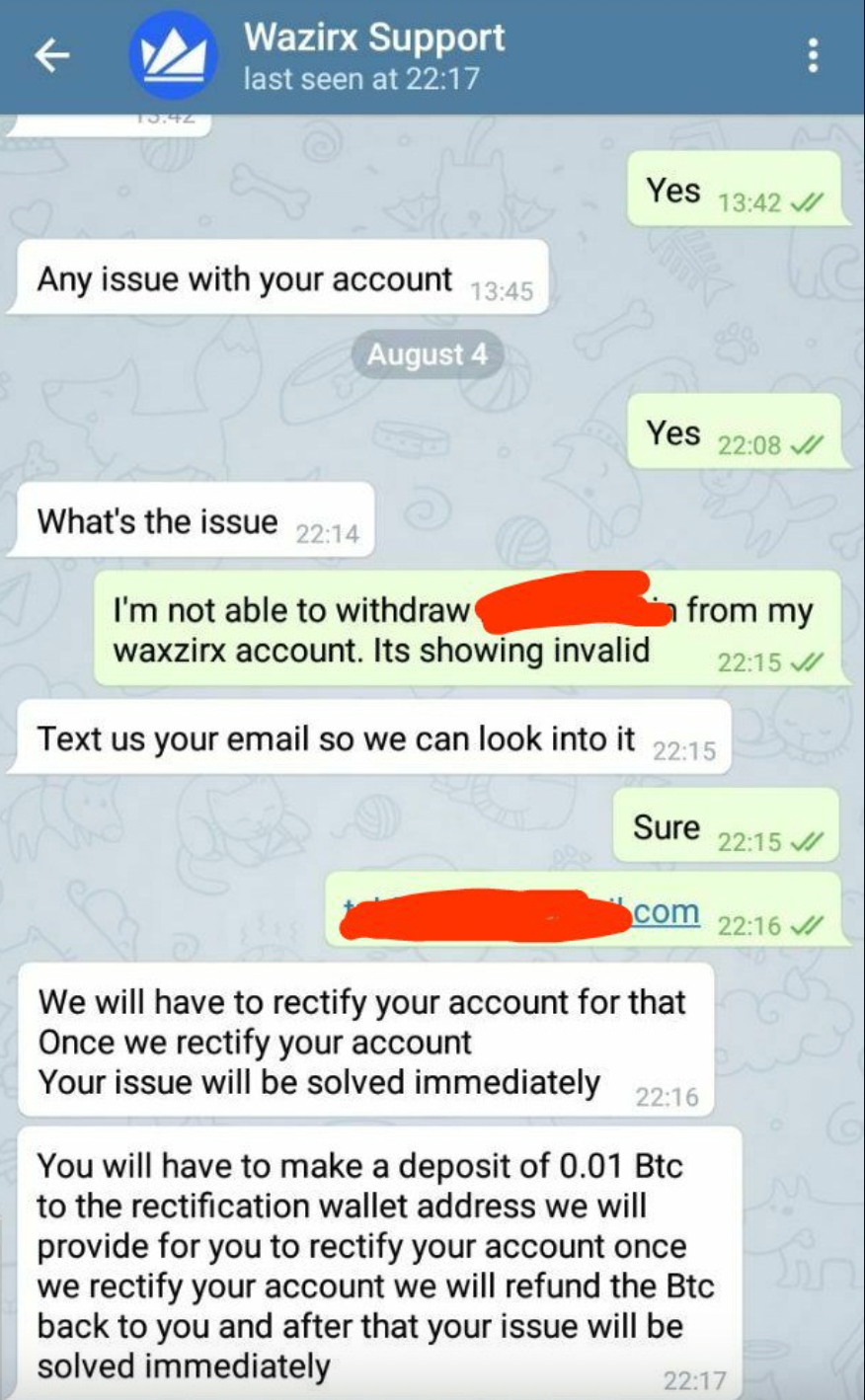
4. Malicious Browser Extensions
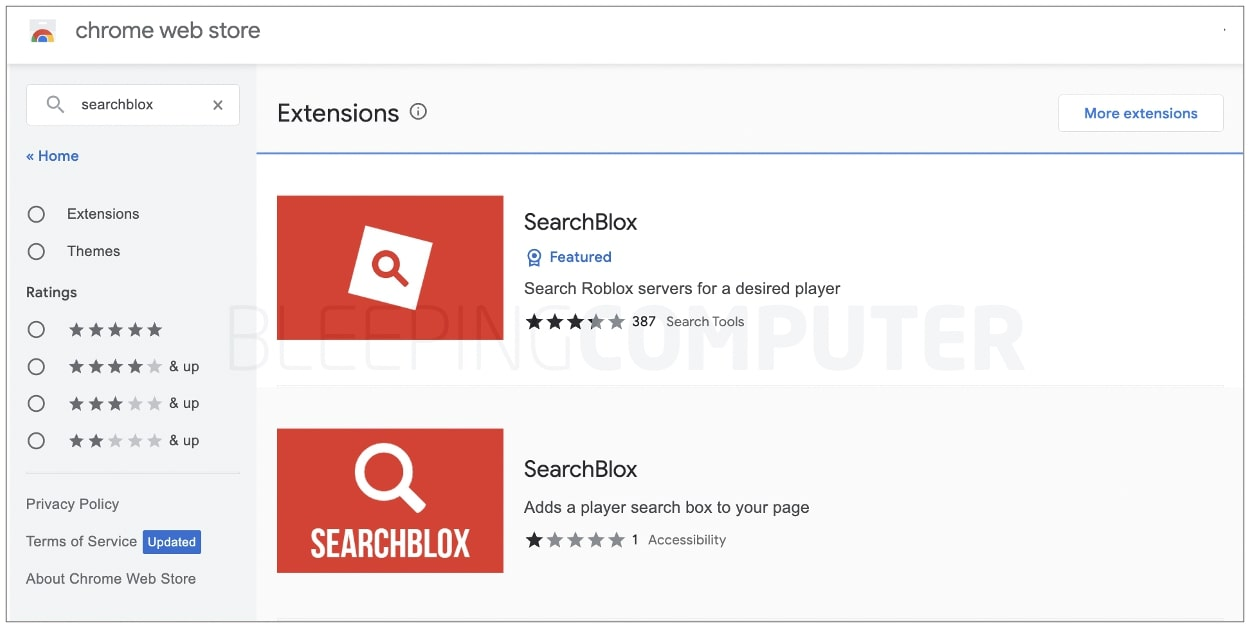
How they work:
- People are tricked into installing browser extensions that steal credentials and private keys
- These fake security tools create the very vulnerabilities they’re supposed to protect against
- They work in most cases as wallet drainers (see our complete wallet drainer protection guide here) disguised as helpful utilities.
5. Fake Airdrops and Giveaway Scams
Fake airdrops are a simple but effective way to trick Web3 users into giving instead of receiving new crypto assets
- “Free token” schemes such as airdrop scams or fake faucets will require you to connect your wallet
- Malicious smart contracts hidden in mint functions wait for you to approve it, then drain your wallet
- Another method is to ask you to send funds to an “official” address.
These airdrops often use AI on social media to make it appear like they’re endorsed by celebrities like Elon Musk or Donald Trump. The most high-profile incident was in 2020 when multiple Twitter attacks got hacked and thousands of users were duped into sending crypto to a fake address.

6. AI Agent & Deepfake Scams at Scale

AI-generated scams are operating at scale never seen before, with the potential for fully autonomous scam AI agents in 2026.
Capabilities of AI Scam Agents
- They generate highly convincing phishing messages in real time.
- AI agents hold personalized conversations that feel human and responsive.
- Messaging adapts instantly based on how each victim responds.
- Scams run simultaneously across email, social media, and messaging platforms.
- Successful attacks are analyzed to continuously improve future scams.
How this affects Web3 security
Human awareness alone is no longer enough to stop advanced scams. Traditional security tools struggle to keep up with adaptive AI attacks. This is because the scale of scam campaigns grows far beyond manual operations.
As a result, personalized scams significantly increase the chances of user deception.
It’s now super easy to write, code and create visual content for anyone, and this year will likely show AI-generated crime on an unprecedented scale.
Much of it will be in the form of nearly undetectable deepfake video or audio from people we love or admire, such as celebrities, families and friends.
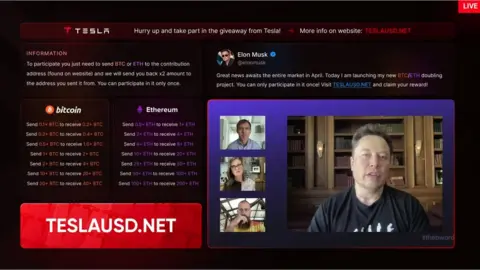
Source: BBC
Elon Musk deepfakes in 2024 were claimed by CBS to contribute in billions of dollars of crypto scam losses.
https://www.youtube.com/watch?v=-kILAg5EBrs
Watch this heartbreaking report of a woman getting scammed out of $1.7m by an AI deepfake and fake phone operators.
https://www.youtube.com/watch?v=_eAjCx8-45c
7. “Pig Butchering” Romance Scams
Got a smoking hot match on a dating app like Tinder that seems to be good to be true? And he or she is also into crypto and trading and investing? Sorry, but you’re about to lose more than your heart.
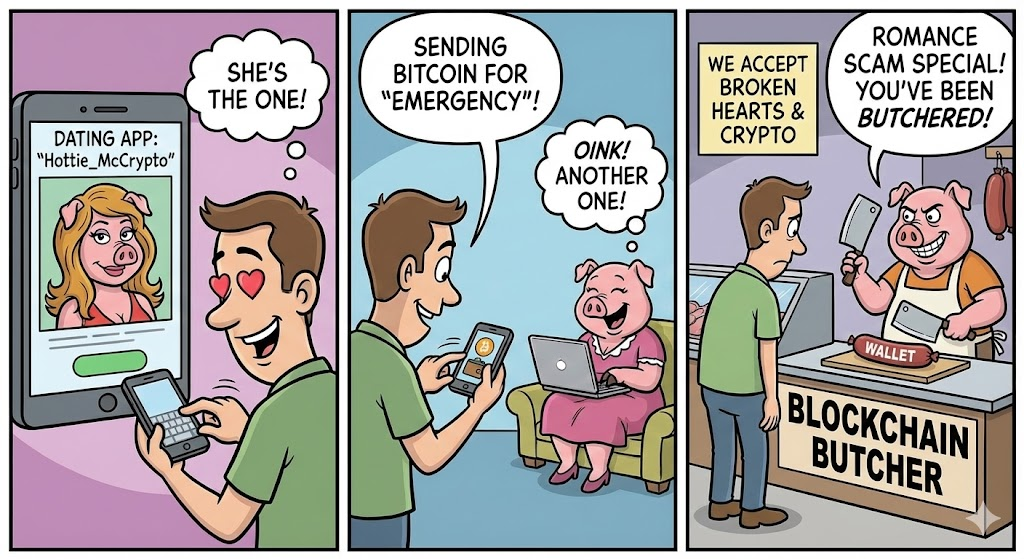
How Pig Butchering in crypto works (Source: Nano Banana)
Romance scams, often referred to as “pig butchering” rely on long-term emotional manipulation rather than quick deception.
The Playbook:
- Attackers spend weeks or even months building trust through friendship, flirtation, or mentorship before introducing crypto as a shared interest or investment opportunity.
- After establishing trust, the scammer presents a fake trading platform or investment strategy that appears professional and profitable.
- They encourage victims to deposit increasingly large amounts over time, until withdrawals suddenly fail and all funds are lost.
These scams eventually succeed because emotional attachment overrides financial caution.
8. Scareware
Scareware uses fear and urgency to push users into hasty decisions. Victims see alarming messages warning that their wallet has been compromised, malware has been detected, or funds are in immediate danger. The goal is to trigger panic and force action without verification.
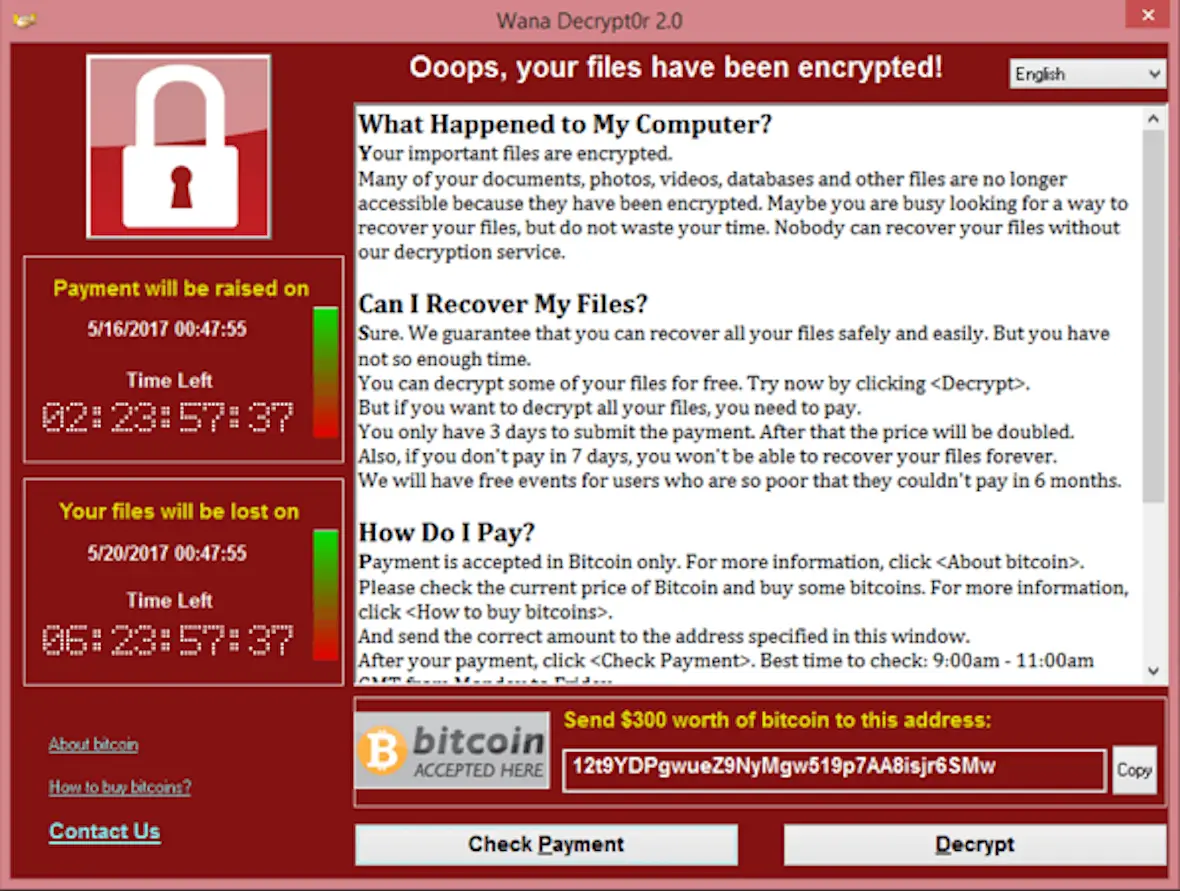
These messages often redirect users to malicious downloads or fake support pages where attackers request credentials or wallet access. In reality, browsers and wallets do not issue emergency pop-ups demanding immediate action. Scareware succeeds because fear disrupts rational decision-making.
9. Baiting
Phishing doesn’t always rely on scaring people, but also using greed and FOMO to great effect.
Baiting scams lure victims with the promise of something appealing, such as free software, exclusive access, early features, or large discounts. The offer feels like an opportunity rather than a risk, which lowers skepticism.
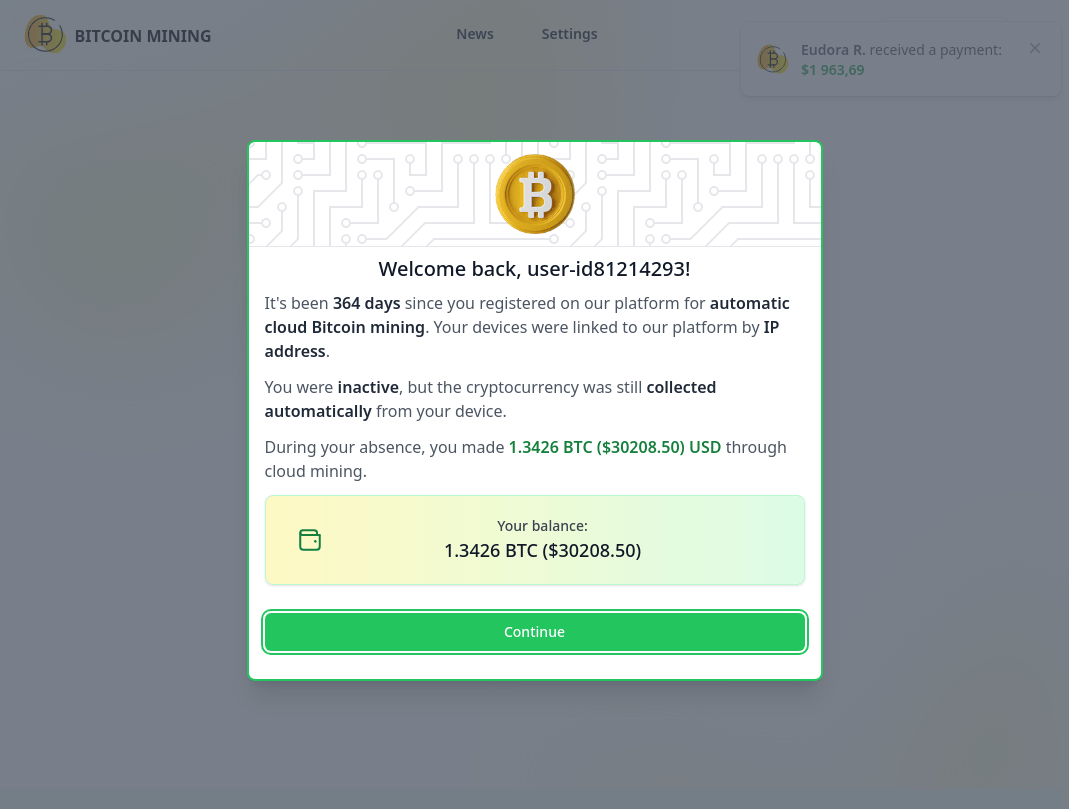
Source: Kaspersky
Once victims engage, attackers prompt them to download malware, connect a wallet, or share sensitive information. The promised reward never exists. Instead, the bait encourages voluntary interaction that leads directly to compromise.
10. Developer Targeting
In crypto, not even the smartest people that actually build the blockchain are spared. Attackers such as North Korea’s Lazarus group increasingly target Web3 developers through fake AI platforms and job interview scams, recognizing that compromising a single developer can provide access to entire project treasuries.
North Korea’s Lazarus Group first phished a SafeWallet developer, infecting their machine and modifying the wallet’s front-end code. The altered interface showed normal transactions while secretly swapping the multisig implementation during a cold-to-hot transfer, so signers unknowingly approved a draining transaction that redirected Bybit’s funds, resulting in a $1.5 billion hack.

Source: NKNews.org
Phishing Example: GMGN Platform
In an effective GMGN platform attack, 107 users approved fake transactions after visiting a cloned site, resulting in losses exceeding $700,000.
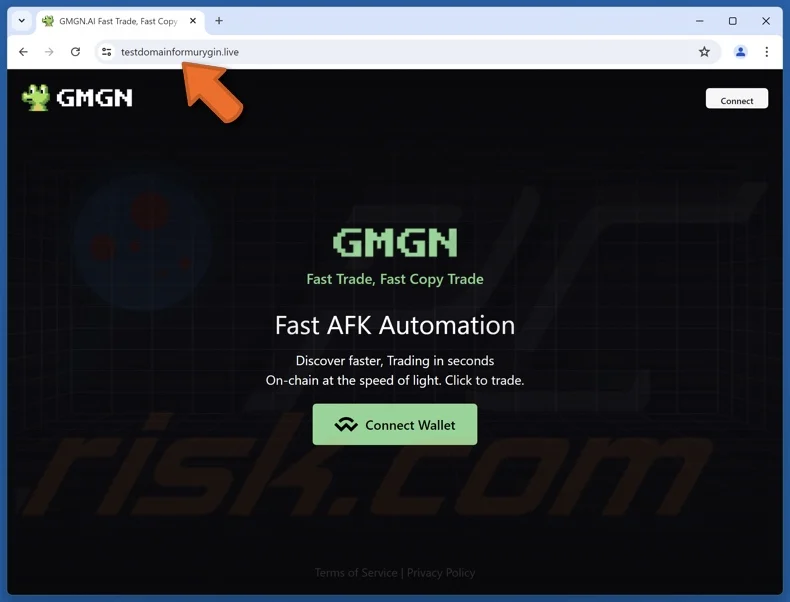
The attack succeeded because:
- The fake site was nearly identical to the legitimate platform
- Users failed to verify the URL before connecting wallets
- Malicious contract requests appeared normal
- Victims signed transactions under time pressure
Threat Type 2: Private Key and Seed Phrase Compromise

Your private key and seed phrase are the ultimate targets for attackers. Once compromised, your funds are gone—permanently and irreversibly.
Here are the biggest attack vectors targeting private keys:
11. Keyloggers & Trojan malware
Malware should be called “everyware” because they’re damn near everywhere on the web. Here are some of the more nefarious ways they can take your digital assets from you.
- Keyloggers secretly record seed phrases as users type them during wallet setup.
- Screen-capture malware snaps images while wallets display sensitive recovery phrases.
- Memory-scraping malware extracts private keys directly from active system memory.
- Trojan apps pose as legitimate software while quietly stealing wallet credentials.
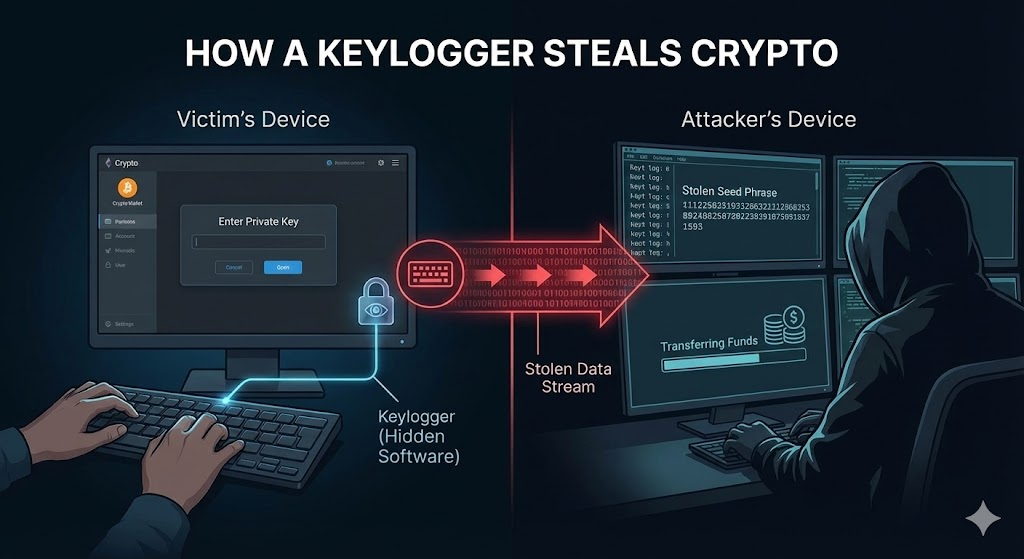
How a keylogger program steals crypto (source: Nano Banana)
12. Clipboard Hijackers
Clipboard hijackers are malware that run quietly in the background to avoid user detection.
- These programs replace copied crypto addresses with attacker-controlled wallet addresses.
- Transactions are silently redirected without the user noticing any visible changes.
- These attacks are hard to detect without dedicated security monitoring tools.
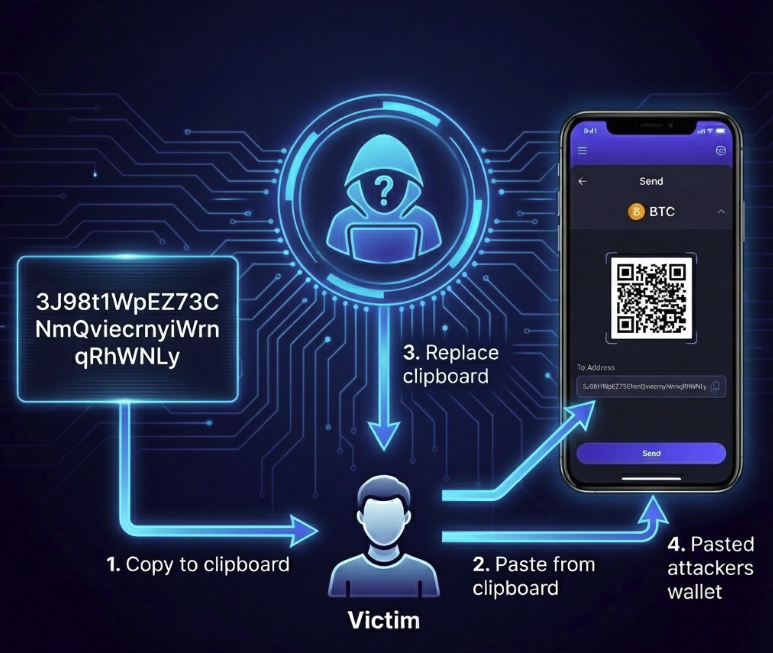
How Clipboard hijacking works step by step (source: nano banana)
13. Fake Wallet Apps
- Malicious wallet apps sometimes appear inside official mobile app stores.
- Attackers publish near-identical clones of trusted wallet applications.
- Fake wallets request seed phrases during a seemingly normal setup process.
Entered credentials are immediately sent to attackers for asset theft.
Real-World Impact
Stolen cryptographic keys were responsible for the $73 million Bitfinex breach, demonstrating that even sophisticated cryptocurrency exchanges can fall victim to this fundamental attack vector. For individual users without enterprise security resources, the risk is exponentially higher.
And of course, what happens if your keys are lost?
Just read the controversial tales of Quadriga’s Gerald Cotton and James Howell to find out.
Threat Type 3: Malicious Smart Contracts


Smart contracts introduce unique security risks that don’t exist in traditional applications. Once you interact with a malicious contract and give it certain transaction approvals, the damage is often immediate and irreversible.
Examples of Malicious Smart Contracts
14. Unlimited Token Approval Contracts
These contracts are often disguised inside otherwise legitimate-looking dApp interactions.
Their methodology is simple but deadly:
- They request permission to access all tokens of a specific asset type.
- Once approved, attackers can drain the entire balance at any later time.
- The approval remains active until the user manually revokes permissions.
15. Hidden Drain Functions
Some NFT minting contracts secretly include mechanisms designed to steal assets. These malicious functions may only activate when specific on-chain conditions are met.
The hackers delay certain functions to avoid immediate suspicion after interaction and can lie in wait for their victims, ready to pounce when funds come in. Drain functions are often triggered through secondary or linked contract calls.
16. Honeypot Tokens
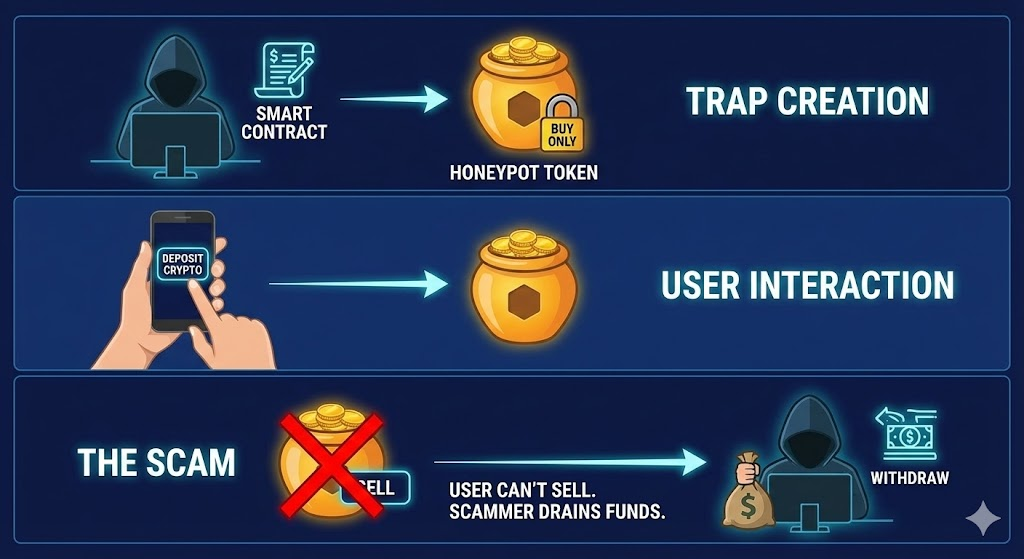
Honeypot tokens have been the scourge of millions of meme coin traders in 2025. Traders quickly jump on a new token, seeing its market cap skyrocket in a short time as more buyers pile in. What they don’t know is that what goes in, cannot come out.
- These tokens allow users to buy but block all selling transactions.
- Funds become permanently locked inside the smart contract.
- Early price movements create a misleading sense of potential profit.
- Liquidity is destroyed or blocked when users attempt to sell.
17. Rug Pulls
If you trade new cryptocurrencies such as meme coins on decentralized exchanges, chances are high that you will have been “rugpulled” in the past. We will cover crypto rug pulls in more detail in 2026.

Here’s how it works in short:
- Developers retain hidden admin controls within the smart contract.
- These controls allow full withdrawal of project liquidity at will, pulling the rug from under the investors and dropping liquidity to close to zero, so that no one can withdraw their tokens.
- Trading may be disabled shortly after initial hype builds.
- The project is abandoned once funds are successfully extracted.
Current Vulnerability Landscape
According to the OWASP Smart Contract Top 10 for 2025, access control vulnerabilities sit at the top spot as the most critical threat. Logic errors have jumped to number three due to an increasing number of successful attacks exploiting flawed contract logic.
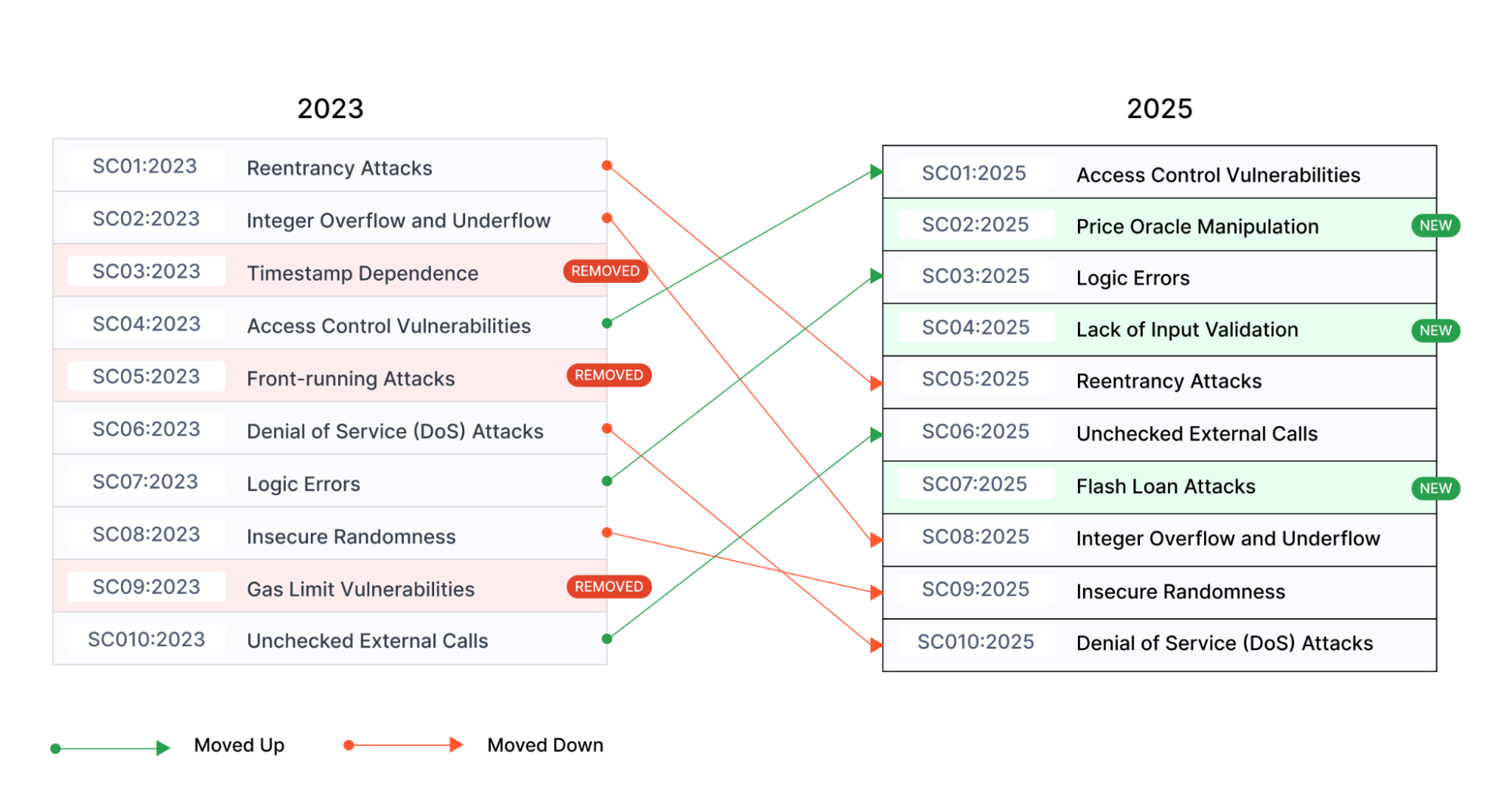
Source: OWASP
Threat Type 4: Wallet Drainers and Approval Exploits


Wallet drainers represent an increasingly automated and scalable Threat Type to Web3 users.
Read our Kerberus Crypto Wallet drainer guide for a full breakdown.
18. Wallet Drainer Attacks
Crypto wallet drainer attacks can be devastating, and work as follows.
Step 1: Victim Attraction
- Fake websites promoted through social media
- Fraudulent NFT mints advertised to collectors
- Compromised legitimate websites
- Malicious advertisements on crypto platforms
Step 2: Wallet Connection
- User connects wallet to malicious dApp
- Contract requests token approvals
- Request appears normal to inexperienced users
- Multiple approvals requested simultaneously
Step 3: Signature and Approval
- User signs transaction approving contract
- Unlimited access granted to specified tokens
- Approval remains active indefinitely
- Multiple tokens compromised in single interaction
Step 4: Automated Theft
- Drainer scripts monitor approved wallets
- Funds extracted immediately or strategically timed
- Multiple victims processed simultaneously
- Stolen assets quickly laundered through mixers
Threat Type 5: Centralized Exchange Risks

Using centralized exchanges contradicts the fundamental Web3 philosophy of “not your keys, not your crypto,” yet many users still rely on these platforms for convenience.
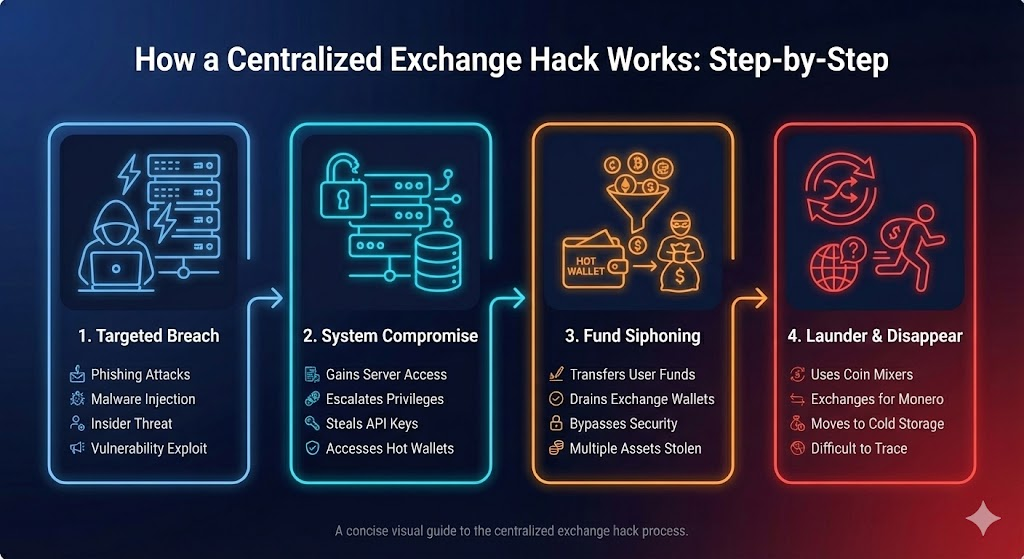
19. CEX Wallet Hacks
Major centralized finance platforms suffered catastrophic losses in 2025:
- Bybit: $1.46 billion hack due to access control failures
- Phemex: $85 million loss from compromised signers
- Both incidents involved exchange-controlled wallets, not user mistakes.
- Neither breach was caused by smart contract bugs.
Why Centralized Exchanges Remain Vulnerable to Hacks
They have single points of failure
- Exchanges hold and control all user funds on their platforms.
- Centralized key systems create large, attractive targets for hackers.
- Weak internal controls can expose millions of users at once.
- One security failure can quickly lead to massive losses.
They face constant insider risks
- Some employees have high-level access to sensitive systems.
- Attackers often trick staff through phishing or impersonation.
- Admin accounts can be taken over without users knowing.
- In rare cases, insiders may abuse access to steal funds (see FTX).
In December 2025, Binance suspended an employee for insider trading and offered a $5m bounty against fake token listing parties.
They’re subject to regulatory and legal risks
- Governments can freeze or seize exchange-held funds.
- Bankrupt exchanges may lock or lose user deposits.
Accounts can be frozen with little warning or explanation.
- Different country laws can delay or block fund recovery.
Here are 10 historic examples of how authorities have seized or shutdown exchanges on short notice.
Threat Type 6: Decentralized Finance (DeFi) Exploits

20. Cross-Chain Bridges: High-Value Targets

Cross-chain bridge exploits remain one of the most destructive attack types in Web3, responsible for over $2.8 billion stolen historically. These bridges, which allow assets to move between different blockchain networks, present complex security challenges.
Cross-chain bridges lock huge amounts of crypto in one place, making them prime targets for attackers. A single flaw can drain hundreds of millions across multiple blockchains. These systems are complex, rely on validators, and use smart contracts on both sides, creating many ways for hackers to exploit bugs, steal keys, manipulate proofs, or bypass verification.
Risk Level: HIGH
DeFi has been a breeding ground for various crypto ills, such as governance attacks, sybil campaigns and flash loan exploits to name a few.
21. DeFi Governance Attacks

Flash loan attacks have enabled attackers to gain temporary control of decentralized autonomous organization (DAO) voting systems.
How Governance Attacks Work
- Attackers borrow large amounts of governance tokens using flash loans.
- Temporary token ownership grants majority voting power.
- Malicious proposals are approved within a single transaction.
Protocol treasuries or core settings are altered or drained.
- The borrowed tokens are repaid before the transaction completes.
Recent Attack Examples:
- Compound governance manipulation attempts
- Beanstalk Protocol governance exploit
- Tornado Cash governance token attack
- Multiple smaller DAO exploits
22. Flash Loan Attacks
Flash loan attacks exploit a unique feature of DeFi lending protocols that allows users to borrow large amounts of crypto without collateral, as long as the loan is repaid within the same transaction.

- Attackers use these instant loans to temporarily gain massive capital, which they then use to manipulate markets, governance votes, or protocol logic before returning the funds seconds later.
- Because everything happens in one transaction, these attacks are difficult to stop in real time. Flash loans have been used to drain treasuries, manipulate token prices, and exploit poorly designed governance systems.
- The risk is not the loan itself, but how protocols fail to account for sudden, artificial liquidity spikes in their security assumptions.
23. Oracle Manipulation

Oracle manipulation attacks target the price feeds that DeFi protocols rely on to make decisions, such as liquidations, collateral values, and trade pricing. If an attacker can influence or temporarily distort an oracle’s data, they can trick a protocol into making incorrect calculations that benefit the attacker.
This often happens in low-liquidity markets, where attackers use large trades or flash loans to move prices on a single exchange that feeds oracle data. When protocols rely on weak or slow-updating oracles, attackers can drain funds, force liquidations, or mint assets at unfair prices before the system corrects itself.
24. Sybil Attacks
A Sybil attack occurs when a single attacker creates many fake identities to gain disproportionate influence over a DeFi or Web3 system. These fake accounts can be used to manipulate governance votes, farm airdrops, skew reputation systems, or abuse incentive programs designed for real users.
Sybil attacks are especially dangerous because they are hard to detect on permissionless networks. Without strong identity or behavior-based protections, attackers can quietly influence outcomes at scale. This undermines fair participation, distorts governance decisions, and weakens trust in decentralized systems meant to reward genuine users.
25. Quantum Computing
Quantum computing poses a long-term risk to modern encryption systems used across crypto and Web3. If mature, quantum computers could undermine the cryptography securing cryptocurrencies, financial systems, and blockchain infrastructure.
We’ll dive deeper into the quantum threat in 2026.
Here’s the good news, at the moment though there’s enough time:
- Quantum computing is not considered an immediate security threat in 2026.
- Researchers are actively developing post-quantum cryptography standards.
- Major blockchain projects are already planning future cryptographic upgrades.
- Most experts estimate a five to ten year timeline for practical quantum attacks.
What Users Should Know
- Users should follow project announcements related to quantum-resistant upgrades.
- It is important to understand which blockchains have clear upgrade roadmaps.
- There is no need for panic, but staying informed is essential.
- Tracking progress in quantum-resistant algorithms helps users prepare long term.
Threat Type 7: Physical Coercion and Exposure

26. The Wrench Attack
When all else fails, some bad actors revert to a last resort: physical violence, also known $5 wrench attacks.
Wrench attacks are the most extreme form of crypto theft because they target people, not technology. Instead of exploiting wallets or software, attackers use threats or violence to force victims to unlock devices, reveal seed phrases, or sign transactions. Once access is granted, funds can be moved immediately and permanently.
These attacks are rare, but they are real. In January 2025, David Balland, a senior executive at Ledger, was kidnapped in France and held for ransom. The incident drew global attention because it showed that even experienced crypto professionals can become targets, simply because of their perceived access to digital assets.
It’s also ironic because a few years earlier, Ledger accused Trezor of not being safe enough, since it didn’t have a secure element. Trezor’s reply was that Ledger holders were not immune to a wrench attack.
What makes wrench attacks different is that no digital safeguard can stop them. Hardware wallets, strong passwords, and secure devices offer little protection if someone is forced to comply in person. The risk increases when crypto ownership becomes visible through social media, public appearances, or on-chain activity.
For most users, the best defense is discretion. Avoid advertising holdings, limit public exposure, and treat personal safety as part of your overall crypto security.
Closing: Staying Safe in Web3
Web3 security in 2026 is more complex, faster moving, and more human-focused than ever before. Attackers are professional, well-funded, and increasingly automated, but that does not mean users are powerless. Most major losses still come down to avoidable mistakes: clicking rushed links, signing unclear transactions, granting unlimited approvals, or trusting the wrong interface.
The good news is that strong habits dramatically reduce risk. Verifying URLs, limiting token approvals, using hardware wallets, and separating daily wallets from long-term storage already put users ahead of most attackers. Adding a real-time Web3 security layer further closes the gap by catching threats before damage occurs.
Use an automated, real-time Web3 security tool like Kerberus Sentinel3 to get peace of mind around the clock.

FAQ: Web3 Security Threats in 2026
Q: What are the biggest Web3 security threats in 2026?
A: The two most critical threat types are social engineering/phishing attacks and private key/seed phrase compromise. These account for billions in losses, with phishing schemes alone reaching $600 million in early 2025. However, malicious smart contracts, wallet drainers, DeFi exploits, and centralized exchange risks also pose significant dangers.
Q: What is phishing-as-a-service?
A: Professional phishing operations that sell turnkey solutions on the internet or Dark Web, providing pre-built templates, automated targeting, and even technical support for scammers with minimal technical knowledge.
Q: How can I identify a cloned website or dApp?
A: Check URLs carefully for minor character differences or Cyrillic letters. Bookmark trusted domain URLs and always verify you’re on the legitimate site before connecting your wallet.
Q: Will legitimate crypto services ever ask for my seed phrase?
A: Never. No legitimate service, support team, or platform will ever request your seed phrase or private keys under any circumstances. Any such request is a scam.
Q: What is “pig butchering”?
A: A romance scam where attackers build trust over weeks or months through dating apps or social media, eventually convincing victims to invest in fake crypto platforms before disappearing with their funds.
Q: How do AI deepfakes threaten Web3 users?
A: Scammers use AI to create realistic video and audio impersonations of celebrities, project founders, friends, or family members to promote fake investment opportunities or trick users into revealing wallet credentials.
Q: What is clipboard hijacking?
A: Malware that secretly replaces copied crypto addresses with attacker-controlled addresses, redirecting transactions without visible changes. Always verify addresses before sending funds.
Q: How do fake airdrops work?
A: Scammers create “free token” schemes requiring wallet connection. Malicious smart contracts hidden in mint functions drain wallets once approved, or victims are tricked into sending funds to “official” addresses.
Q: What should I do if I see a security warning pop-up?
A: This is likely scareware. Legitimate browsers and wallets don’t issue emergency pop-ups demanding immediate action. Close the pop-up and verify your wallet security through official channels.
Q: What are malicious smart contracts and how do they work?
A: These contracts trick users into granting harmful permissions or interacting with hidden theft mechanisms. Examples include unlimited token approval contracts, hidden drain functions, honeypot tokens, and rug-pull-enabled admin functions.
Q: How do wallet drainer attacks work?
A: Wallet drainers attract victims to fake sites, request wallet connections, obtain unlimited token approvals, and then automatically drain assets using pre-programmed scripts that monitor approved wallets.
Q: Why are cross-chain bridges frequent attack targets?
A: They hold large pools of locked assets and rely on complex, multi-chain validation systems. Vulnerabilities in smart contracts, proof verification, or validator keys can result in massive losses.
Q: Why are centralized exchanges still risky in 2026?
A: They represent single points of failure. Hacks frequently occur due to compromised multisig signers, internal access control failures, operational mistakes, and insider threats.
Q: What new threats will emerge in 2026?
A: AI-powered autonomous scam agents capable of adapting in real time, conducting personalized social engineering, and executing large-scale attacks across multiple platforms.
Q: What are DeFi governance attacks?
A: Attackers use flash loans to temporarily acquire majority voting control in DAOs, pass malicious proposals, drain treasuries, or change key protocol parameters—all within a single transaction.
Q: How can I protect myself from these threats?
A: Use real-time Web3 security tools like Kerberus, never share seed phrases or private keys, verify URLs before connecting wallets, be skeptical of urgent requests, bookmark trusted sites, limit token approvals, use hardware wallets, and separate daily wallets from long-term storage.
Web3 Security Threats Knowledge Quiz
Test your knowledge and see how well you understand Web3 security threats and how to protect yourself
1. Which of the following is NOT a phishing attack vector?
Hint: Think about what phishing attacks use to trick users versus what is a normal, legitimate Web3 interaction.
2. Which does NOT contribute to seed phrase compromise?
Hint: Consider which method actually protects your seed phrase rather than exposing it.
3. Which is NOT a malicious smart contract type?
Hint: Think about which option is actually a legitimate infrastructure component used by DeFi protocols.
4. Which is NOT a risk associated with centralized exchanges (CEXs)?
Hint: Consider what makes centralized exchanges risky versus what is actually a feature of decentralized systems.
5. Which is NOT a technology that enhances phishing attacks?
Hint: Think about what technologies attackers use to improve their scams versus what is a blockchain optimization feature.
6. Which is NOT malware used to steal crypto?
Hint: Consider what is actually a security feature versus what is malicious software designed to steal.
Written by:
Werner Vermaak
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users. His Kerberus articles help readers understand modern Web3 threats, real-world attack patterns, and practical safety practices in an accessible, research-backed way.
Read more about the authorRelated Guides
See more guides
The Psychology of Crypto Scams: How And Why They Still Work
Jan 16, 2026 • 4 minutes read

The Ultimate Web3 Security Beginner Guide For 2026
Dec 23, 2025 • 4 minutes read

Address Poisoning Attacks: How They Scam Web3 Users
Dec 11, 2025 • 4 minutes read

Web3 Security Tools: How to Protect Your Assets in 2026
Nov 19, 2025 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
