The Psychology of Crypto Scams: How And Why They Still Work
Learn how crypto scammers exploit human psychology to steal funds. Understand why even experienced users fall for scams and how to protect yourself from social engineering attacks.

Introduction
By the end of 2025, most crypto scams no longer look suspicious on the surface. They look like routine actions: a wallet connection, a support message, a mint page, or a signature request that feels familiar. The technology behind blockchains has not suddenly become easier to exploit. Instead, scammers have become far better at exploiting human behavior.
Today’s most damaging crypto scams succeed not because users lack intelligence or experience, but because they are pushed into making decisions under pressure, urgency, or misplaced trust. Understanding how these scams work psychologically is now a core part of staying safe in crypto.
This article explains
- how modern crypto scams operate
- why they work so consistently
- what practical steps users can take to reduce their risk.
It’s based on real-world patterns observed throughout 2025. Our cybersecurity research finds that between 44% and 60% of breaches involve human error such as private key mismanagement.
The findings, published in Kerberus’s report “The Human Factor: Real-Time Protection Is the Unsung Layer of Web3 Cybersecurity”, show a disconnect between where the industry invests in security and the points at which users actually lose funds.
What Social Engineering Means in Crypto

Social engineering in crypto refers to the manipulation of users into authorizing actions themselves that lead to asset loss. Rather than hacking wallets or stealing private keys, scammers focus on influencing decisions.
If a user signs a transaction, approves a token, or connects a wallet under false assumptions, the blockchain will still execute that action exactly as instructed.
This is a crucial distinction to understand. In many crypto scams, nothing is technically “wrong” with the transaction. The transaction is valid, the signature is real, and the wallet behaves as designed. Deception occurs before the transaction, at the level of context and trust.
Because blockchain transactions are irreversible, a single moment of misplaced trust can have permanent consequences.
Why Do Crypto Users Fall for Scams?
“The Web3 ecosystem sets users up to fail. Social engineering drives the majority of real losses because we expect people to identify threats they have no way to detect. Users face these attacks during distracted moments or high-stress situations when cognitive capacity fails. Audits and monitoring can’t prevent what happens in those seconds. We need security that protects people during transactions, not just protocols before deployment.”

Alex Katz, Kerberus CEO
Crypto places responsibility directly on the user. There are no chargebacks, no account recovery departments, and no centralized fraud teams monitoring activity. When users self-custody assets, they also inherit the full burden of security decisions that come with being your own bank.
Public blockchain data makes this problem worse. Web3 wallet balances, NFTs, DeFi activity, and interaction history are visible to anyone. Scammers use this information. to identify targets and craft messages that feel personally relevant. A user who recently minted NFTs may receive a fake staking message while a DeFi trader may receive a fake governance alert.
At the same time, crypto culture rewards speed. Users are conditioned to act quickly to avoid missing opportunities. This constant pressure to move fast creates ideal conditions for manipulation.
How Crypto Scams Exploit Human Psychology

Crypto scams succeed because they exploit predictable patterns in human decision-making. When people feel urgency, they stop verifying details. When a message appears to come from an authority figure, they are more likely to comply. When something looks familiar, skepticism drops.
Wallet interactions reinforce these habits. Signing messages, approving tokens, and connecting wallets become routine.
Over time, users rely on pattern recognition rather than active analysis. Scammers design attacks to fit seamlessly into these routines, making malicious actions feel normal.
By the time a wallet prompt appears, the scam has often already done its psychological work.
The Crypto Scam Process: Step-by-Step
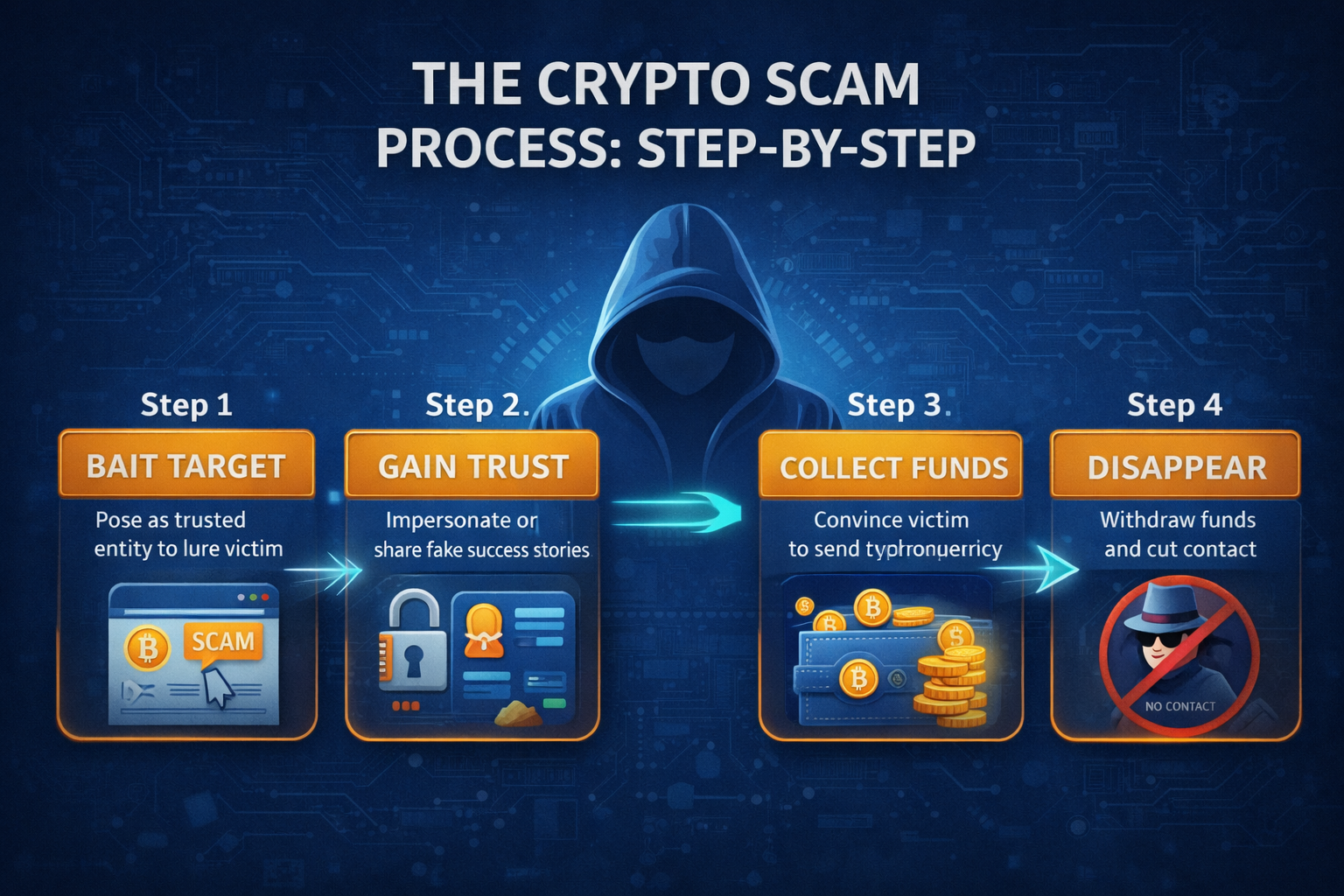
While crypto scams come in many forms, most follow the same behavioral structure in 4 to 6 steps:
Step 1: Victim Profiling and Targeting
Attackers analyze wallet data and social activity to decide who to target and what narrative is most likely to succeed. This might involve impersonating support, promoting a fake airdrop, or announcing an urgent security issue.
Step 2: Initiating Contact
Next, scammers reach out to their victims in environments where users already expect interaction, such as X replies, Discord channels, or Telegram groups. Public engagement helps build credibility before moving the conversation into private messages.
Step 3: Building False Trust
Once contact is established, the user’s trust is quickly gained and reinforced using familiar branding, cloned websites, or compromised accounts. Screenshots, transaction hashes, and technical language are often used to create a sense of legitimacy.
Step 4: Creating Urgency
With trust established, creating a sense of urgency now becomes the central tool, driven by artificial creation of fake FOMO or FUD. Users are told they must act quickly to avoid losing funds, missing rewards, or securing access. This time pressure discourages independent verification, forcing the victim into making a mistake.
For example, a ticking countdown clock might show that there are 3 minutes left to send funds to an ICO round, or 60 seconds left to mint a free NFT. The user clicks on a link and gets drained or sends funds to the scammer’s wallet address. In both cases, funds are irretrievably lost.
Step 5: Prompt Wallet Action
The critical moment occurs when the user is asked to interact with their wallet. The request itself usually looks ordinary: connect a wallet, sign a message, or approve a transaction. Technically, the action may even be valid. The danger lies in why it is being requested.
Step 6: Stealing Assets and Disengaging
After approval, assets are transferred or permissions are abused. The scammer disengages, communication stops, and funds are moved through multiple addresses to obscure recovery. In some cases, victims are later targeted again with fake recovery services.
How Phishing Got Its PhD in Crypto Psychology
By 2025, Web3 phishing had largely moved away from email and embedded itself in the fast-paced world of social platforms, where the crypto zeitgeist lives and breathes. Attackers actively monitored public conversations, answering user questions faster than legitimate teams.
Coindesk reported multiple cases in 2025 where user wallets were drained after clicking links shared by impersonated support accounts replying directly to their posts on X.
READ OUR CRYPTO WALLET DRAINER GUIDE
These attacks work because they feel contextual and timely. Users do not perceive them as cold outreach, but as helpful responses to real problems.
Fake Support Scams Remain a Leading Threat
Fake support scams continue to account for a significant share of crypto losses. Users experiencing failed transactions, wallet errors, or network issues are emotionally primed for assistance.

Security firms such as CertiK and SlowMist highlighted throughout 2025 that support impersonation remains one of the most reliable scam methods, especially during periods of high market activity.
The losses they wreak on crypto users are all too real.
- In August 2025, ZachXBT found that one user lost a mindblowing 783 BTC worth $91 million at the time in a social engineering hack where a scammer impersonated a hardware wallet support person.
- In the same month, a British police impersonator fleeced a crypto investor out of 2.1 million pounds, by duping them with a bogus security breach story into entering their password on a fraudulent site.
- In December 2025, a 23-year old American male impersonating a Coinbase customer care staff member was charged with the theft of $15 million, stolen from 100 exchange users who he tricked into revealing their crypto passwords.
The success of these scams has very little to do with user ignorance. It has everything to do with timing, stress, and trust. Apply enough pressure under the right conditions, and any crypto owner could crack.
Wallet Drainers and Approval Abuse in Practice
Wallet drainers exploit how normal approvals work. Many legitimate applications require token or NFT approvals, conditioning users to accept them without hesitation.
In 2025, Kerberus documented numerous cases of wallet draining where users approved malicious contracts on fake mint or staking sites. In many of these incidents, assets were not drained immediately, but hours or days later, making it harder for users to connect cause and effect.
The transaction itself looked legitimate. However, the context was not.
Fake Airdrops Still Work Because “Free” Works

Despite widespread awareness, fake airdrops remain effective because they exploit reward anticipation. The promise of free tokens lowers skepticism and increases urgency.
Chainalysis noted in its 2025 Crypto Crime Report that fake airdrops and reward-based scams continued to target retail users during major ecosystem announcements
When users expect rewards, they are more likely to overlook warning signs.
Why Do Even Experienced Users Get Scammed?
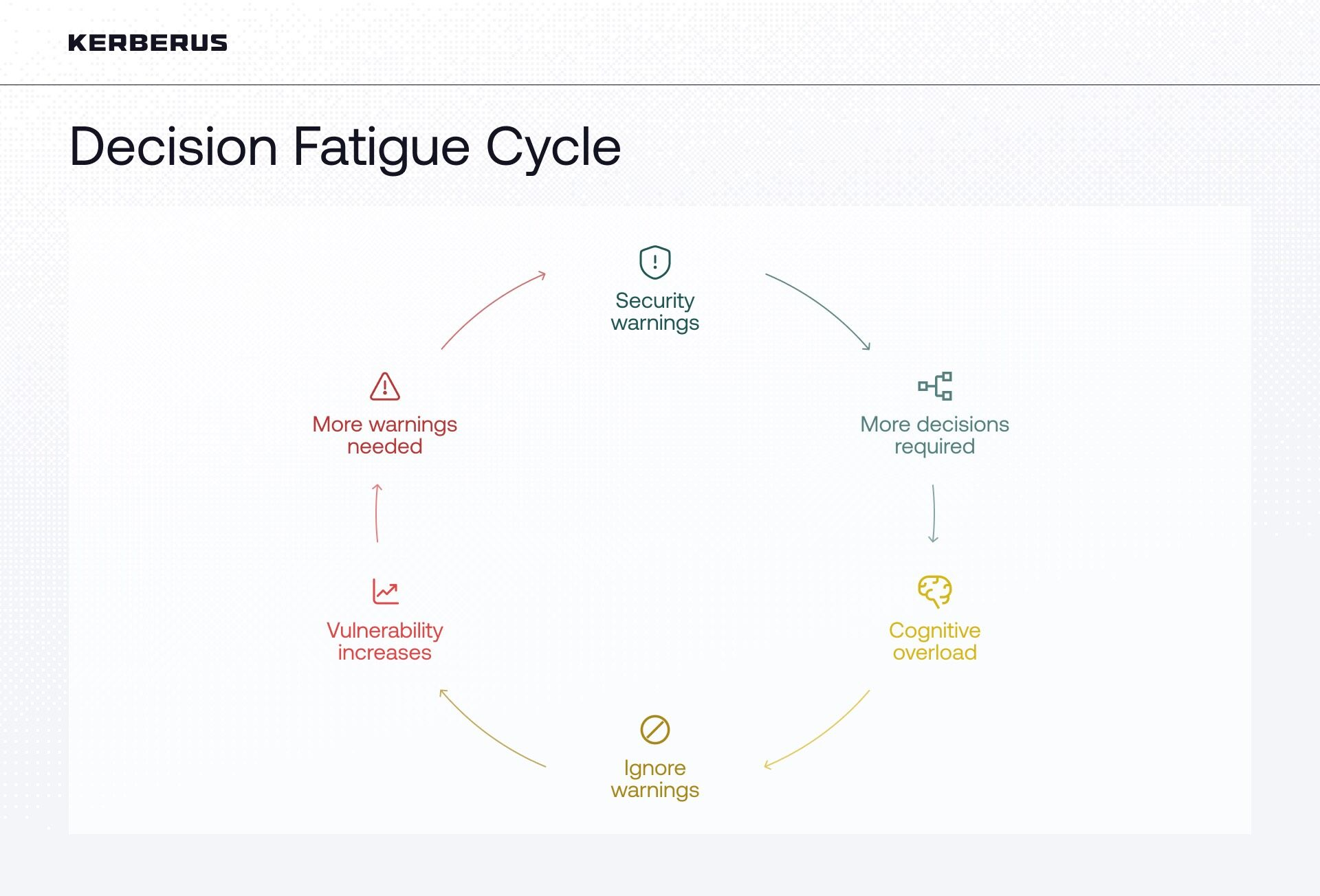
Experience does not eliminate risk. More often than not, it increases it. Familiarity leads to automation, confidence reduces verification, and repeated exposure creates alert and decision fatigue.
Scammers take advantage of these habits. They do not try to surprise users. They try to blend in. Education helps users recognize scams, but it does not protect them when decisions must be made quickly. Stress, urgency, and cognitive overload undermine even good security habits.
Expecting users to perfectly interpret every wallet prompt under pressure is unrealistic.
_“Social engineering works because the transaction often looks legitimate on-chain. Traditional Web3 security tools aren’t able to distinguish between what a user wants to do and what an attacker manipulates them into.
Real-time solutions require systems that interpret behavioral signals and analyze transactions in real time at the wallet level. Only 13% of Web3 security providers actively block malicious transactions in real time at the wallet level — the kind of protection needed to prevent social engineering attacks before funds leave a user’s wallet.”_
Danor Cohen, CTO of Kerberus
How Kerberus Helps Reduce Scam Risk
This is where preventive security becomes critical. Rather than relying entirely on user interpretation, modern Web3 security tools like Kerberus Sentinel3 focus on detecting malicious behavior before transactions are executed.
Kerberus approaches crypto security by analyzing the context around wallet interactions, not just the transaction itself. By identifying scam patterns, malicious websites, and suspicious behavior in real time, its browser extension aims to stop users from interacting with threats before irreversible actions occur.
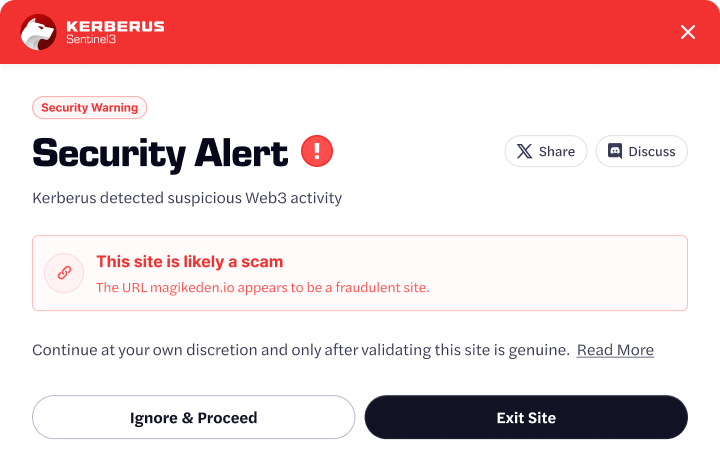
This approach reduces reliance on perfect human judgment at the most vulnerable moment: when a user is being rushed to act.
What Crypto Scams Will Look Like in 2026
In 2026, the crypto psyops are going to get even worse.
Unsurprisingly if you’ve been tracking the scary advances in LLM abilities in 2025, Web3 scams will become more personalized, automated, and difficult to distinguish from legitimate interactions.
AI-generated messages, deepfake impersonation, and coordinated social engineering attacks are expected to increase exponentially, as the barriers to creating these attacks disappear.
As these techniques scale, individual vigilance alone will not be sufficient. Security models must account for human limitations, not assume flawless behavior.
Wrapping Up
Crypto scams succeed because they exploit how people think under pressure, not because blockchains are broken.
If you use crypto, assume that messages can be fake, support can be impersonated, and wallet prompts can be misleading. Slow down, verify context, and rely on protections that reduce the need for split-second decisions.
In a decentralized world, protecting assets increasingly means protecting users from manipulation—not just malicious code.
About Kerberus
Kerberus is a trusted Web3 cybersecurity company protecting users across 1000+ chains with real‑time scam detection and MEV defense. Its team has led and advised security work across top crypto ecosystems since 2023, with zero losses and 99.99% safety for its 250,000 users. It also offers up to $30,000 in coverage on user funds.

Kerberus Sentinel3 is a real-time Web3 security engine which users can install as a browser extension in seconds. It helps users stay safe by automatically detecting phishing, wallet drainers, and social engineering threats across chains, helping crypto users identify and block scam attempts before irreversible losses occur.
Written by:
Werner Vermaak
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users. His Kerberus articles help readers understand modern Web3 threats, real-world attack patterns, and practical safety practices in an accessible, research-backed way.
Read more about the authorRelated Guides
See more guides
Top 26 Web3 Security Threats In 2026
Jan 15, 2026 • 4 minutes read

The Ultimate Web3 Security Beginner Guide For 2026
Dec 23, 2025 • 4 minutes read

Address Poisoning Attacks: How They Scam Web3 Users
Dec 11, 2025 • 4 minutes read

Web3 Security Tools: How to Protect Your Assets in 2026
Nov 19, 2025 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
