Web3 Wallet
A Web3 wallet stores your private keys and crypto. Learn how wallets work, different types, and how to secure them against hackers.

What Is a Web3 Wallet?
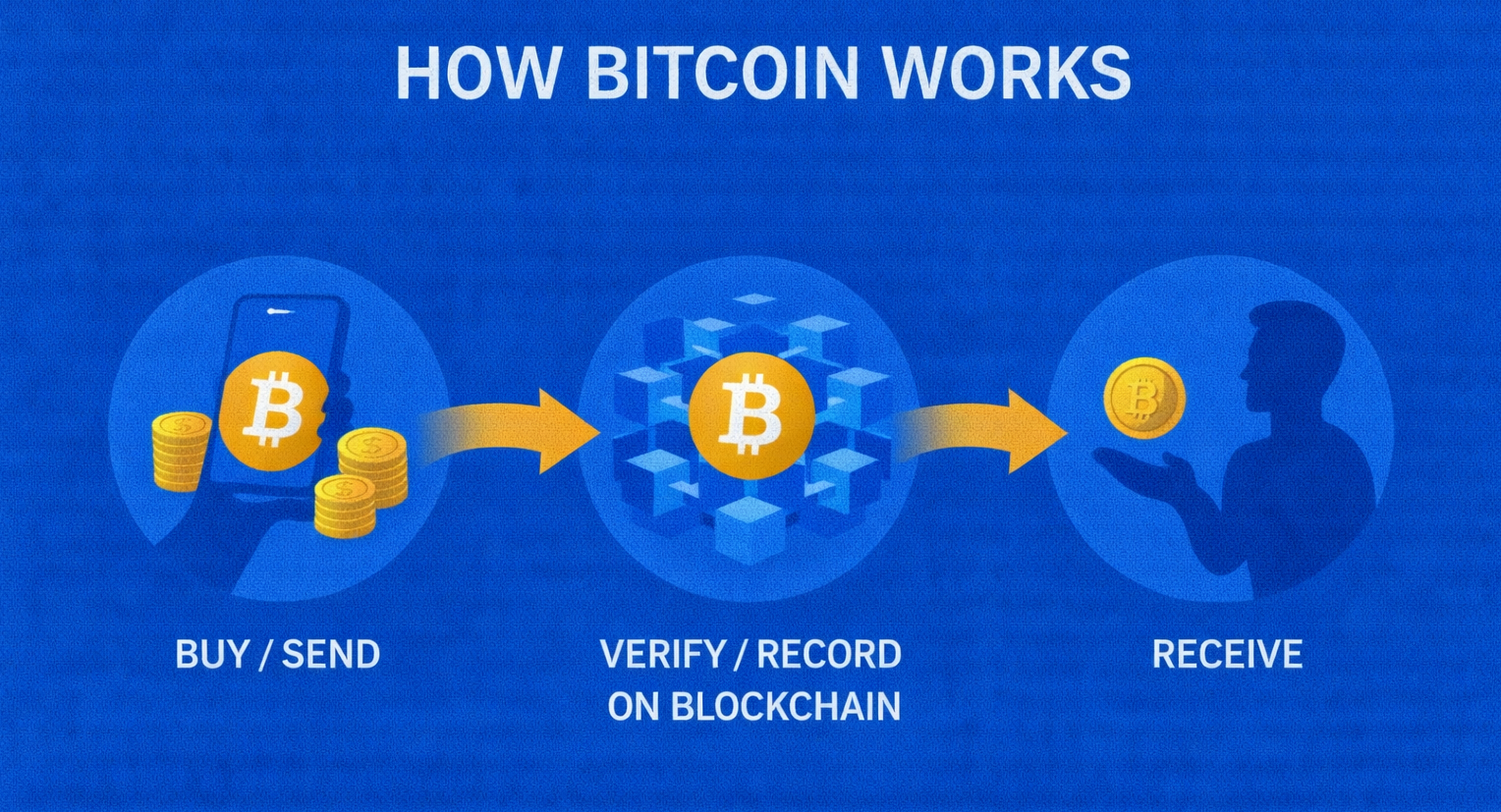
A Web3 wallet is a cryptographic tool that stores private keys, manages digital assets, and enables interaction with decentralized applications. Unlike Web2 accounts with usernames and passwords, Web3 wallets use public-private key cryptography where the private key or seed phrase controls complete ownership of assets. Wallets serve as the primary interface between users and blockchain networks, functioning as both a storage mechanism and an authentication system.
How Web3 Wallets Work
Wallets generate public addresses for receiving funds while keeping private keys secure for transaction signing. They connect to dApps through browser extensions, mobile apps, or hardware devices, enabling users to execute transactions, mint NFTs, participate in DeFi protocols, and engage in governance voting.
Popular implementations include MetaMask for software wallets, Ledger for hardware security, and emerging smart contract wallets that offer social recovery and enhanced security features. Each transaction requires cryptographic signatures that prove ownership without revealing private keys.
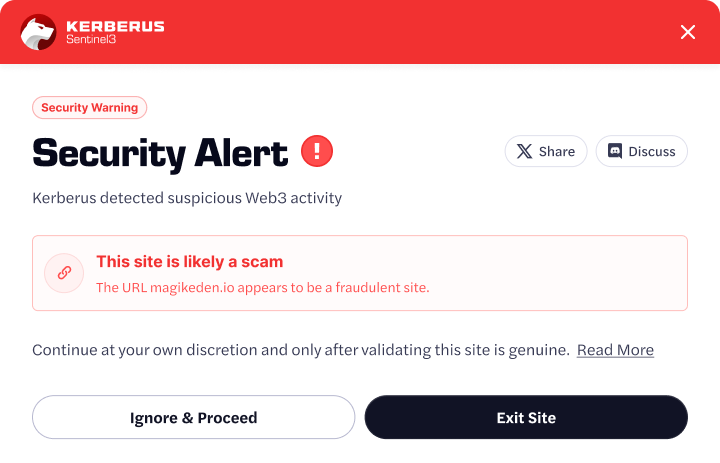
It’s crucial to note that sophisticated hackers, in some cases state-funded, are targeting your Web3 wallet to steal all your assets through techniques like phishing, wallet draining and more.
A top Web3 security tool like Kerberus catches these attacks and alerts you in real-time:
How to Reduce Risk
- Store seed phrases offline in multiple secure locations, never digitally or in cloud storage
- Always check your destination address when sending funds, in order to avoid tricks like address poisoning
- Use hardware wallets for significant holdings and verify all transaction details before signing
- Regularly review and revoke token approvals using trusted revocation tools to prevent unauthorized access
- Employ separate “burner” wallets with limited funds for testing new or unverified dApps
- The widespread wallet drainer attacks throughout 2023, which stole millions through malicious approvals disguised as legitimate interactions, show why careful transaction review and approval management are essential for wallet security
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.