Social Engineering
Social engineering attacks manipulate you into revealing secrets. Learn to spot psychological tricks and protect your crypto assets.

What Is Social Engineering in Web3?
Social engineering is the manipulation of individuals to divulge sensitive information or perform actions that compromise their cryptocurrency assets, private keys, or digital security. Unlike traditional social engineering that targets passwords or personal data, Web3 attacks focus on stealing seed phrases, tricking users into signing malicious transactions that could drain their crypto wallets, or gaining access to wallet credentials. These psychological manipulation techniques exploit trust, urgency, authority, and fear to bypass technical security measures through human vulnerability.
Real-World Example: The high-profile Twitter hack in 2020, where verified accounts including Elon Musk and Barack Obama promoted fake Bitcoin giveaways and stole over $120,000, demonstrates how social engineering can exploit trust in authority figures and official platforms to execute large-scale cryptocurrency thefts
How Web3 Social Engineering Works
Web3 attackers pose as customer support representatives, project team members, or community moderators to gain victim trust through official-looking profiles and verified social media accounts. Common tactics include fake tech support offering to “help” with wallet issues, impersonation of influencers promoting exclusive investment opportunities, phishing messages claiming urgent security updates requiring immediate action, and romance scams building relationships before requesting cryptocurrency transfers.
Attackers often combine multiple channels including Discord, Telegram, Twitter, and email to create convincing scenarios that pressure victims into revealing sensitive information or authorizing harmful transactions.
A top Web3 security tool like Kerberus catches these attacks and alerts you in real-time:
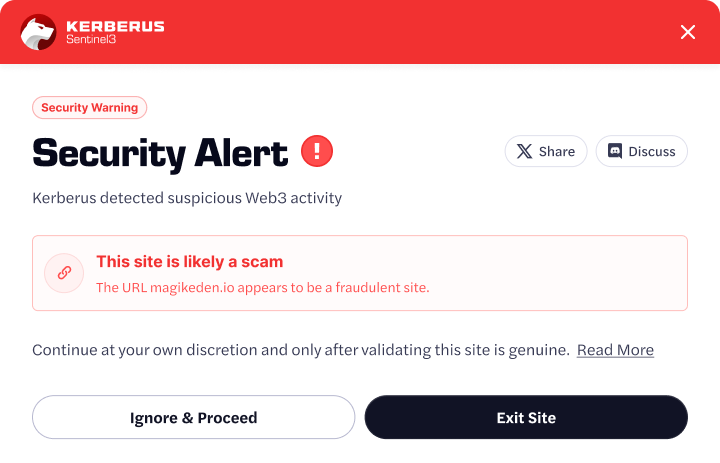
How to Reduce Risk
- Never share seed phrases, private keys, or wallet passwords with anyone claiming to provide support or assistance
- Use Web3 security tools and cold storage to protect yourself optimally
- Verify all communications through official channels and be suspicious of unsolicited contact from team members or support staff
- Enable two-factor authentication on all accounts and use official websites rather than links provided in messages
- Take time to research investment opportunities and verify claims through multiple independent sources before committing funds
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.