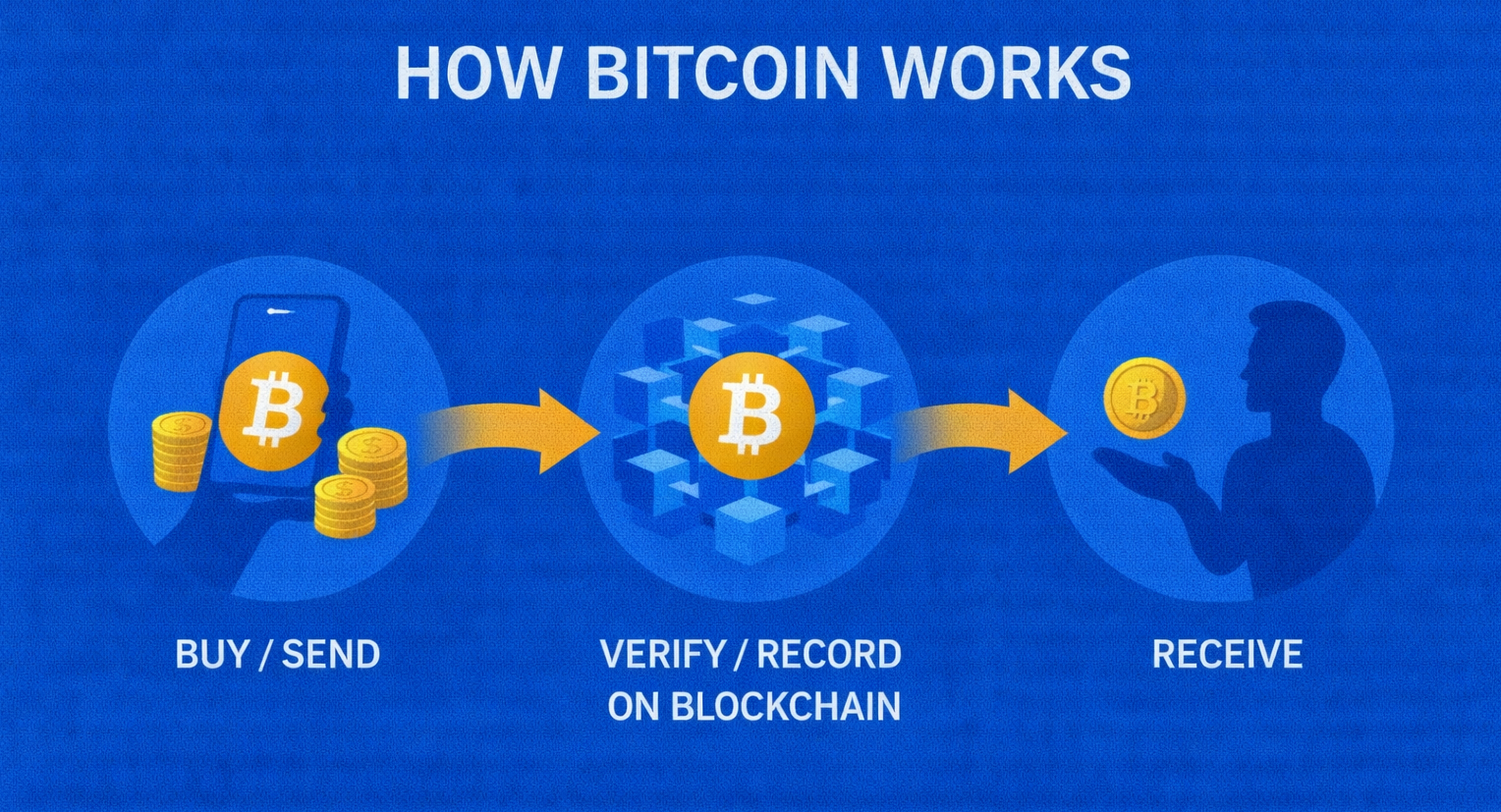
Web3 Security
Web3 security protects you from hacks and scams. Learn about wallet security, smart contract risks, and how to stay safe in crypto.

What Is Web3 Security?
Web3 security encompasses the protection of decentralized applications, users, and infrastructure across blockchain ecosystems. Where traditional security relies on centralized controls, Web3 shifts responsibility to users and code.
This means that malicious signatures or smart contract vulnerabilities can result in instant, irreversible asset loss through methods like wallet draining, flash loan attacks or social engineering like phishing and address poisoning. The attack surface includes smart contracts, wallets, private keys, governance systems, cross-chain protocols, and human behavior patterns.
The $625 million Ronin bridge hack in 2022 highlighted how a single compromised validator key could drain an entire ecosystem, emphasizing the critical importance of comprehensive security measures.
In order to better protect yourself, rigorously implement these 3 layers of Web3 security measures:
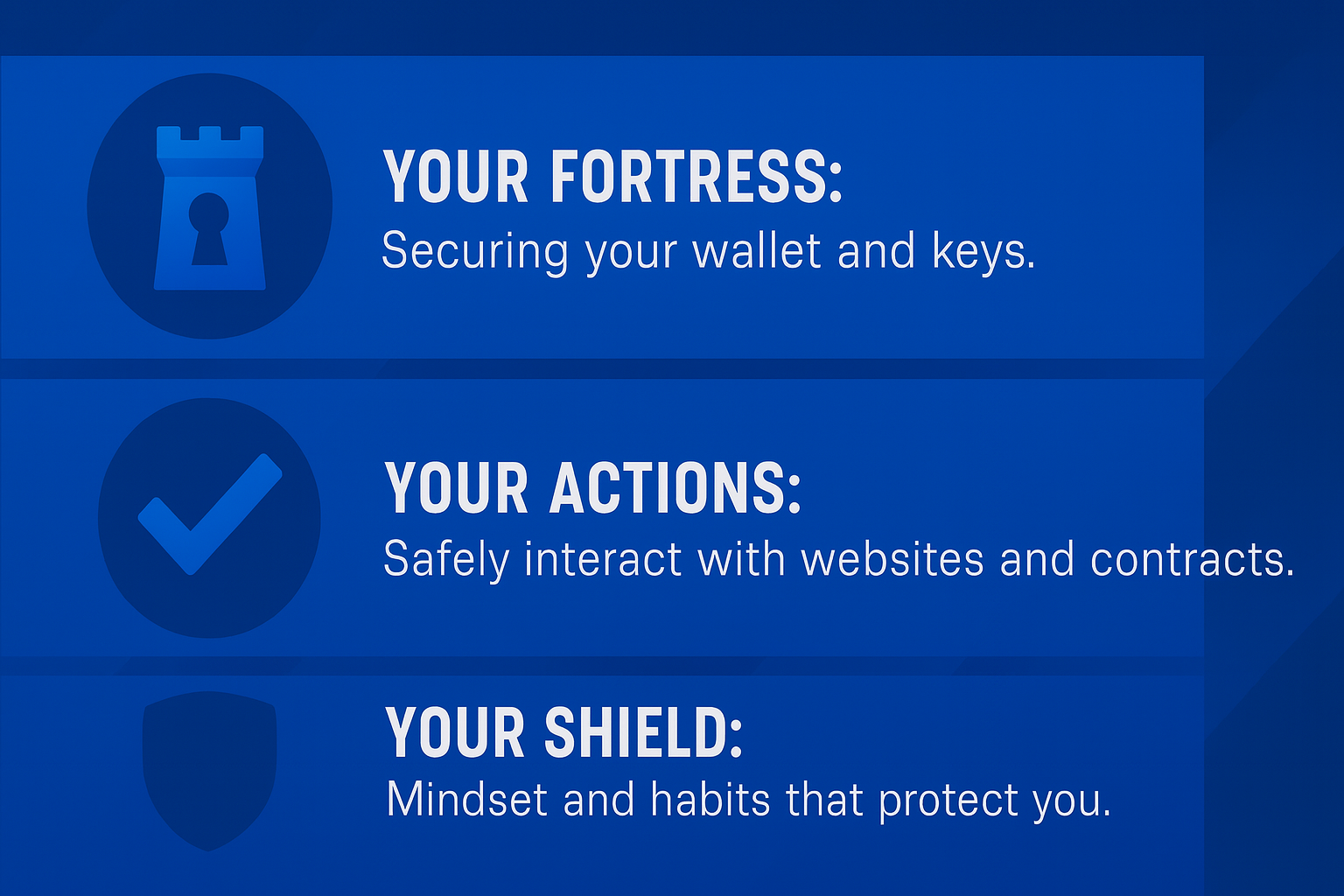
How Web3 Security Works
Security operates across multiple layers: user protection against phishing and wallet drainers, smart contract auditing and formal verification, protocol-level safeguards including multisigs and timelocks, and infrastructure security covering DNS protection and supply chain integrity.
Real-time monitoring systems like Kerberus detect anomalous behavior and potential threats before they execute. Modern Web3 security tools provide transaction simulation, approval management, and risk assessment to help users make informed decisions.

How to Reduce Risk
- Use transaction simulation tools to preview the effects of signatures before approval
- Regularly audit and revoke unnecessary token approvals and NFT operator permissions through trusted revocation tools
- Employ hardware (cold) wallets and maintain separate wallets for different risk levels
- Stay informed about current attack vectors and verify all website URLs before connecting wallets
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.