Phishing
Web3 phishing attacks impersonate trusted sites to steal your keys. Learn to spot fake websites and protect your wallet with Kerberus.

What Is Phishing?
Phishing is a deceptive technique where attackers impersonate real Web2 or Web3 entities like Telegram, Gmail or MetaMask to trick users into revealing sensitive information such as private keys, seed phrases, passwords, or personal data. In the crypto space, phishing attacks typically involve social engineering that deploy fake websites, fake airdrops, emails, social media messages, or direct messages that appear to be from trusted platforms, wallets, or projects but are designed to steal wallet credentials or trick users into signing malicious transactions.
The widespread Twitter hack in 2020, where verified accounts promoted fake Bitcoin giveaways, demonstrates how even official-looking sources can be compromised and used for phishing attacks
How Phishing Works
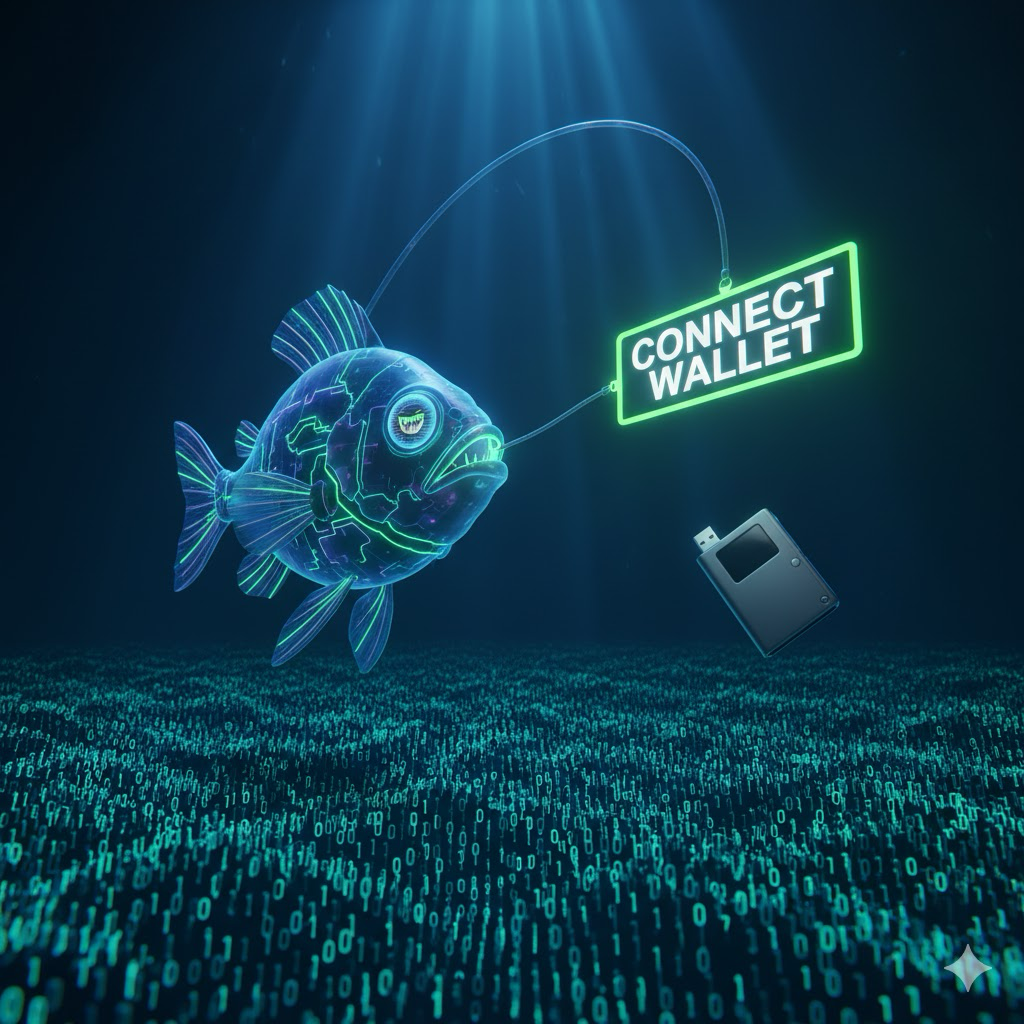
Attackers create convincing replicas of popular cryptocurrency websites, wallet interfaces, or trading platforms, often using similar domain names with slight misspellings or different extensions. They distribute links through fake social media posts, fraudulent emails claiming urgent security updates, or compromised Discord and Telegram channels. When users enter their credentials or connect their wallets to these fake sites, attackers capture the information and use it to drain funds or gain unauthorized access to accounts.
A top Web3 security tool like Kerberus can alert you in real-time through its browser extension or API.
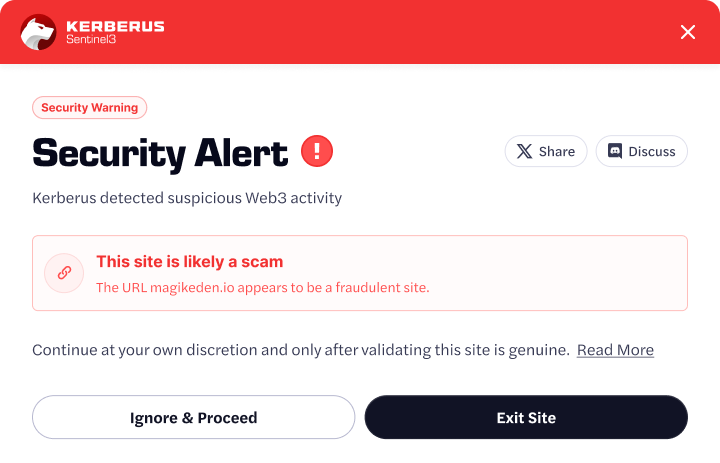
How to Reduce Risk
- Always verify website URLs by typing them directly into your browser rather than clicking links from emails or messages
- Bookmark legitimate cryptocurrency platforms and use these saved links for accessing your accounts
- Enable two-factor authentication on all cryptocurrency-related accounts and use hardware security keys when possible
- Be suspicious of urgent messages claiming account compromise or limited-time offers requiring immediate action
- Use transaction analysis tools like Kerberus to verify website legitimacy before connecting wallets or entering sensitive information
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.