Smart Contract Vulnerability
Smart contract bugs can cause massive crypto losses. Learn about common vulnerabilities and how to check contracts before investing.

What Is a Smart Contract Vulnerability?
A smart contract vulnerability is a flaw in blockchain code that allows attackers to manipulate protocols, drain funds, or disrupt expected behavior. Because smart contracts are immutable once deployed and handle significant financial value, vulnerabilities can lead to immediate, catastrophic losses measured in millions of dollars with no possibility of reversal. These flaws range from simple coding errors to complex economic design issues that emerge only under specific market conditions.
How Smart Contract Vulnerabilities Work
Common vulnerability types include reentrancy attacks where malicious contracts repeatedly call vulnerable functions before state updates complete, oracle manipulation that distorts price feeds to enable arbitrage exploitation, wallet drainer code, access control failures that expose admin functions to unauthorized users, and economic design flaws that enable flash loan attacks or governance manipulation.
These vulnerabilities often arise from complex interactions between multiple contracts, integration risks with external protocols, or unforeseen edge cases in protocol logic that auditors miss.
A top Web3 security tool like Kerberus catches these attacks and alerts you in real-time:
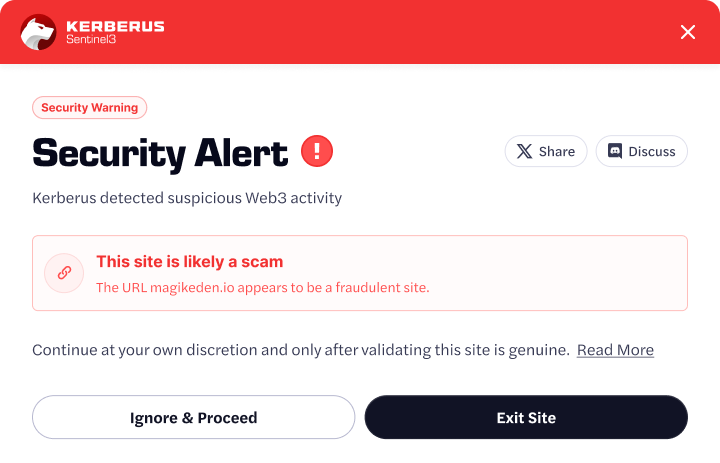
How to Reduce Risk
- Use Kerberus to secure yourself pro-actively and get alerted before it’s too late.
- Protocols should undergo multiple independent security audits, formal verification processes, and gradual deployment strategies with limited initial caps
- Implement defensive coding patterns like checks-effects-interactions, comprehensive testing including fuzzing and integration tests, and runtime monitoring for unusual activity
- Users should research protocol security track records, avoid newly deployed unaudited contracts, and monitor official channels for security disclosures
- The DAO hack in 2016, which drained $50 million through a reentrancy vulnerability and led to Ethereum’s contentious hard fork, remains the most famous example of how a single smart contract flaw can threaten an entire ecosystem
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.