Rugpull
Rugpulls happen when developers steal investor funds. Learn to spot exit scams and protect your investments with our guide.

What Is a Rugpull?
A rugpull is a fraudulent scheme where cryptocurrency project developers abandon their project and steal investor funds, typically by withdrawing all liquidity from decentralized exchanges or selling large amounts of tokens they control.
The term originates from the phrase “pulling the rug out from under someone” and represents one of the most devastating exit scam tactics in Web3 and DeFi. Rugpulls can be executed through technical exploits, economic manipulation, or simple abandonment, leaving investors with worthless tokens and no recourse for recovery.
Case Study: The Squid Game token rugpull in 2021, which crashed from $2,800 to near-zero in minutes after developers restricted selling while maintaining buying pressure, illustrates how psychological manipulation and technical restrictions can amplify rugpull effectiveness, stealing millions from investors who believed they were participating in a legitimate gaming project
How Rugpulls Work

Developers create legitimate-appearing projects with professional websites, whitepapers, and marketing campaigns to attract investors and build liquidity pools on decentralized exchanges. They typically retain large token allocations, control liquidity provider tokens, or embed backdoors in smart contracts that allow fund extraction.
When sufficient funds accumulate, they execute the rugpull by removing all liquidity, selling their token holdings, or exploiting contract vulnerabilities to drain the treasury. Soft rugpulls involve gradually selling tokens to avoid detection, while hard rugpulls involve immediate, complete fund extraction that crashes token prices to zero.
A top Web3 security tool like Kerberus can alert you in real-time through its browser extension or API.
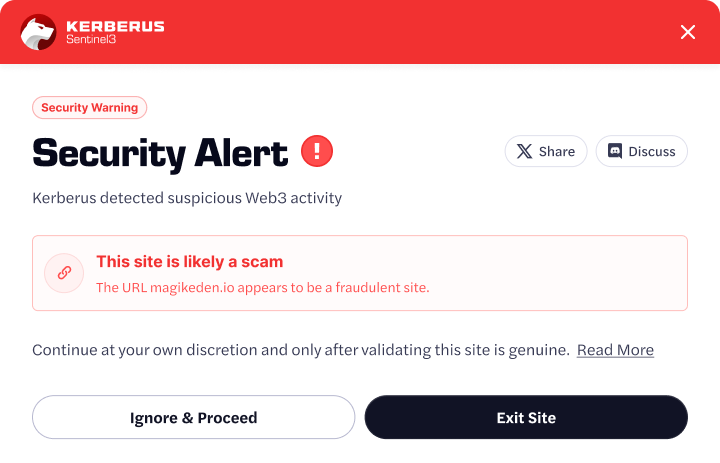
How to Reduce Risk
- Research team backgrounds, verify developer identities, and check for previous project involvement before investing
- Analyze smart contract code for suspicious functions, unlimited minting capabilities, or centralized control mechanisms
- Examine tokenomics for excessive team allocations, lack of vesting periods, or concentrated ownership structures
- Monitor liquidity pool ownership and ensure developers cannot unilaterally withdraw funds from exchanges
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.