Scaling Solana Safely: Automated Defense for Programs, Authorities, and Wallets
Solana lost $250M in H1 2025. Learn how automated transaction protection prevents phishing and social engineering attacks at scale.
Solana is no longer a “promising L1” but the space where millions of people already show up every day. And that reality has turned security from a nice-to-have into an ecosystem survival issue.
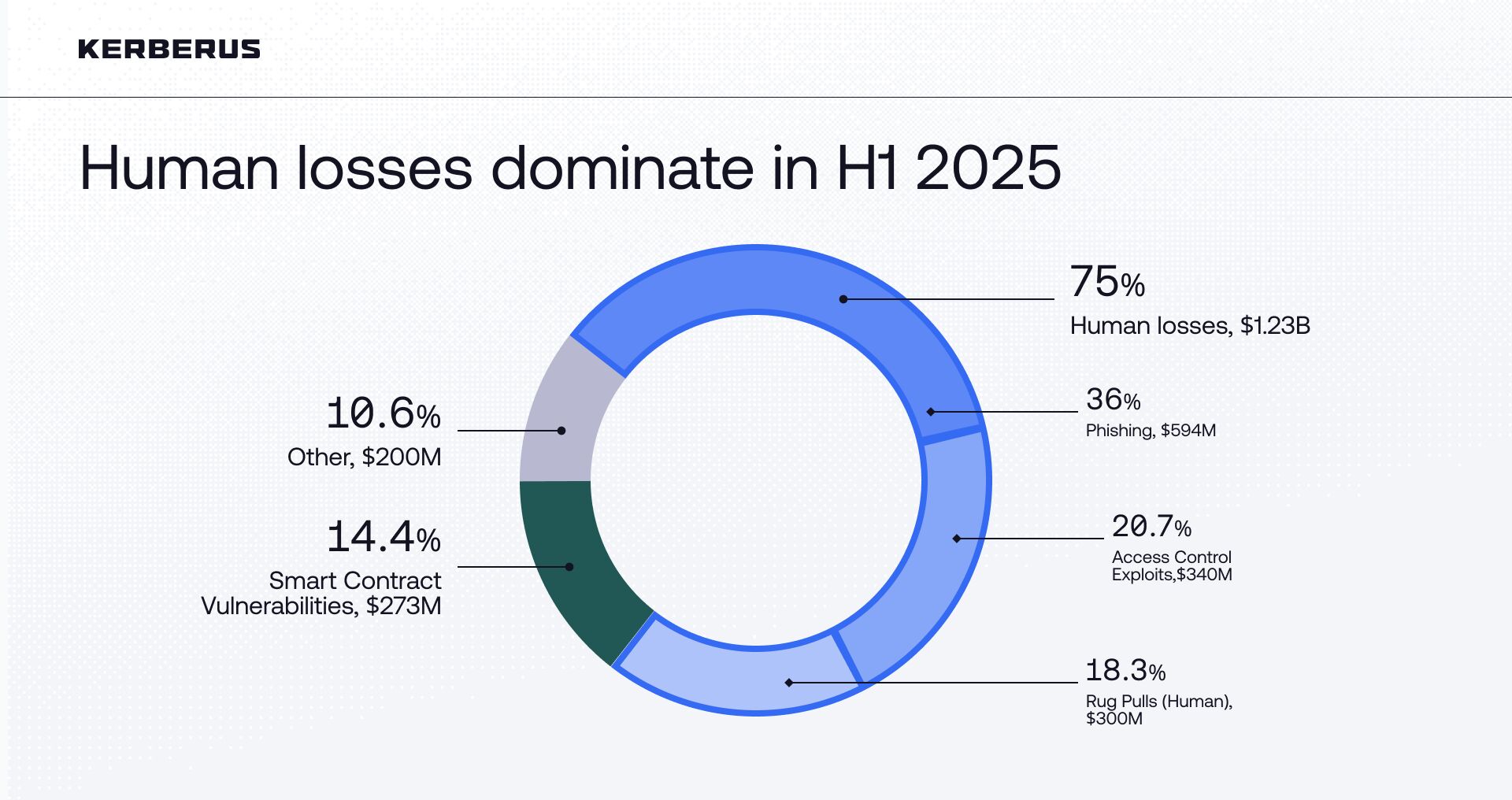
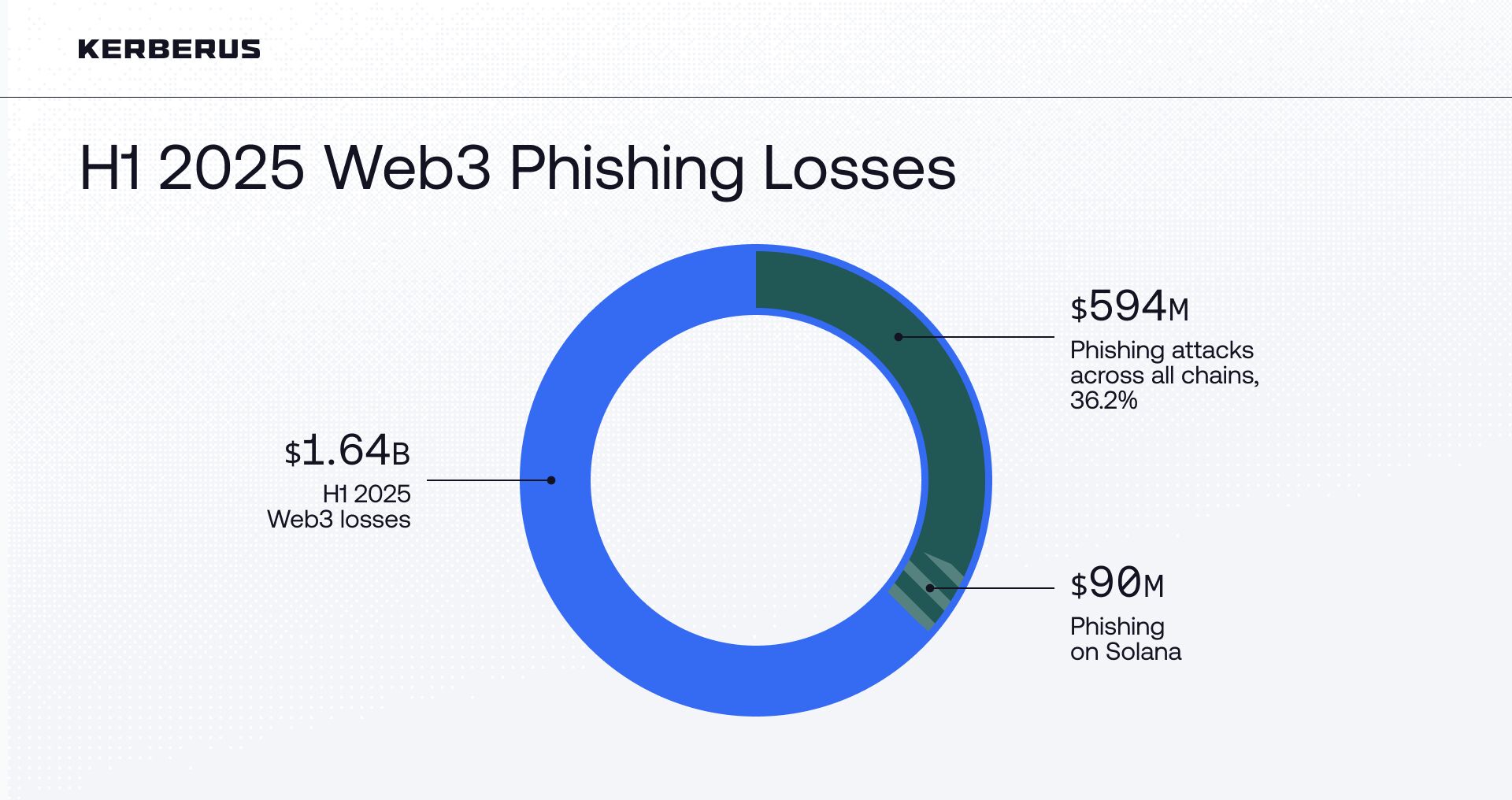
In the first half of 2025 alone, Web3 lost an estimated $1.64 billion to hacks and scams (excluding the Bybit incident). And $250 million of those losses, around 15%, were on Solana.
That’s the profile of a primary target, not a niche chain.
As Solana Breakpoint kicks off, the question isn’t whether Solana can handle throughput or DeFi anymore. It’s whether the ecosystem can keep users, programs, and capital safe at this scale without slowing everything down. For Solana, security automation is no longer optional.

What Solana’s Growth Means for Security on the Ground
Solana’s core story in 2024–2025 is sustained and mainstream-level activity.
It’s millions of daily active addresses, and Solana consistently ranks among the most active chains by transactions and users.
Developer data places Solana at or near the top for new builders entering the ecosystem in 2024, with thousands of developers choosing it as their primary chain.
Solana DeFi total value locked sits in the double-digit billions, driven by protocols like Jupiter, Kamino, Jito, and Raydium, with activity spanning lending, perps, and structured products.
DePIN projects such as Helium have migrated to Solana, routing real-world wireless traffic on-chain and bringing hundreds of thousands of devices into the network’s orbit.
This mix of billions in DeFi, live consumer applications, DePIN, RWAs, payments, and global retail flow creates a security environment that looks more like a high-traffic financial network than an experimental chain.
As the ecosystem scales, attackers don’t need to break Solana itself to cause damage. They just need to find the gaps between programs, authorities, and what users actually sign.
Where Users Really Lose Money
The numbers from H1 2025 show how quickly wallet-level risk has become Solana’s weakest link.
15.2% of H1 2025 Web3 losses were attributed to Solana, around $250 million in total. About 36% of all Web3 losses, roughly $594 million, came from phishing/social engineering scams. An estimated $90 million of this figure was drained directly from Solana wallets.
These aren’t mostly classic smart contract exploits. They are users approving transactions that look legitimate on-chain but are crafted to empty their wallets.
Other data underline the point:
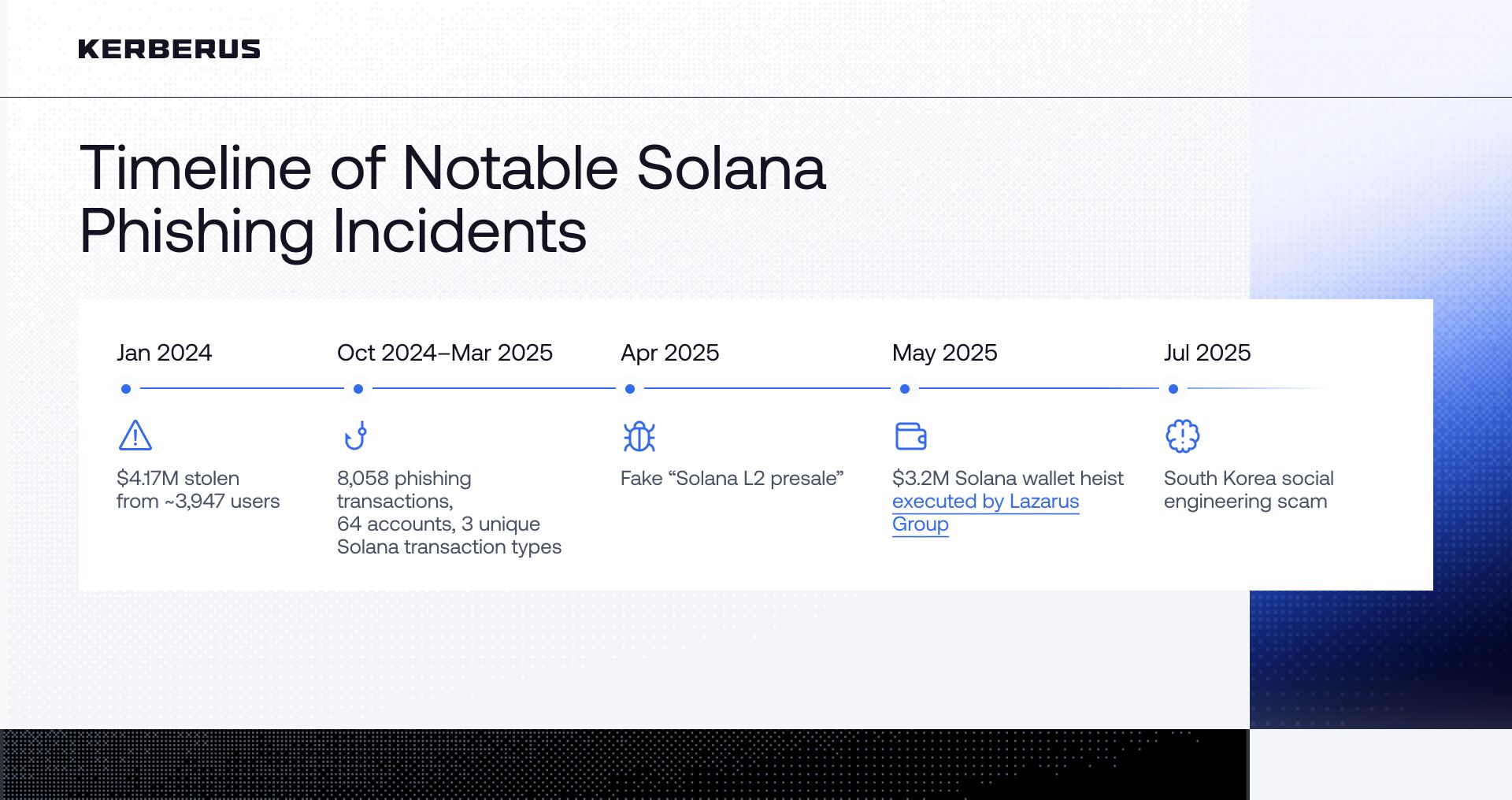
- Scam Sniffer tracked $4.17 million in losses across ~3,947 victims from just two wallet drainer tools.
- The SolPhishHunter report identified 8,058 phishing transactions on Solana, $1.1 million in confirmed losses, 64 malicious accounts, and 3 new Solana-native phishing patterns (multi-transfer drainers, authority-transfer traps, and system-account impersonation).
- Scammers hit Solana users between late 2024 and early 2025 using fake presale sites, Telegram impostor accounts, cloned wallets sold in regional app stores, and bogus “Solana L2” token launches.
- In May 2025, the Lazarus Group — a state-backed hacking operation — stole $3.2M from Solana wallets by getting users to approve malicious transactions. The lesson: social engineering works on everyone.
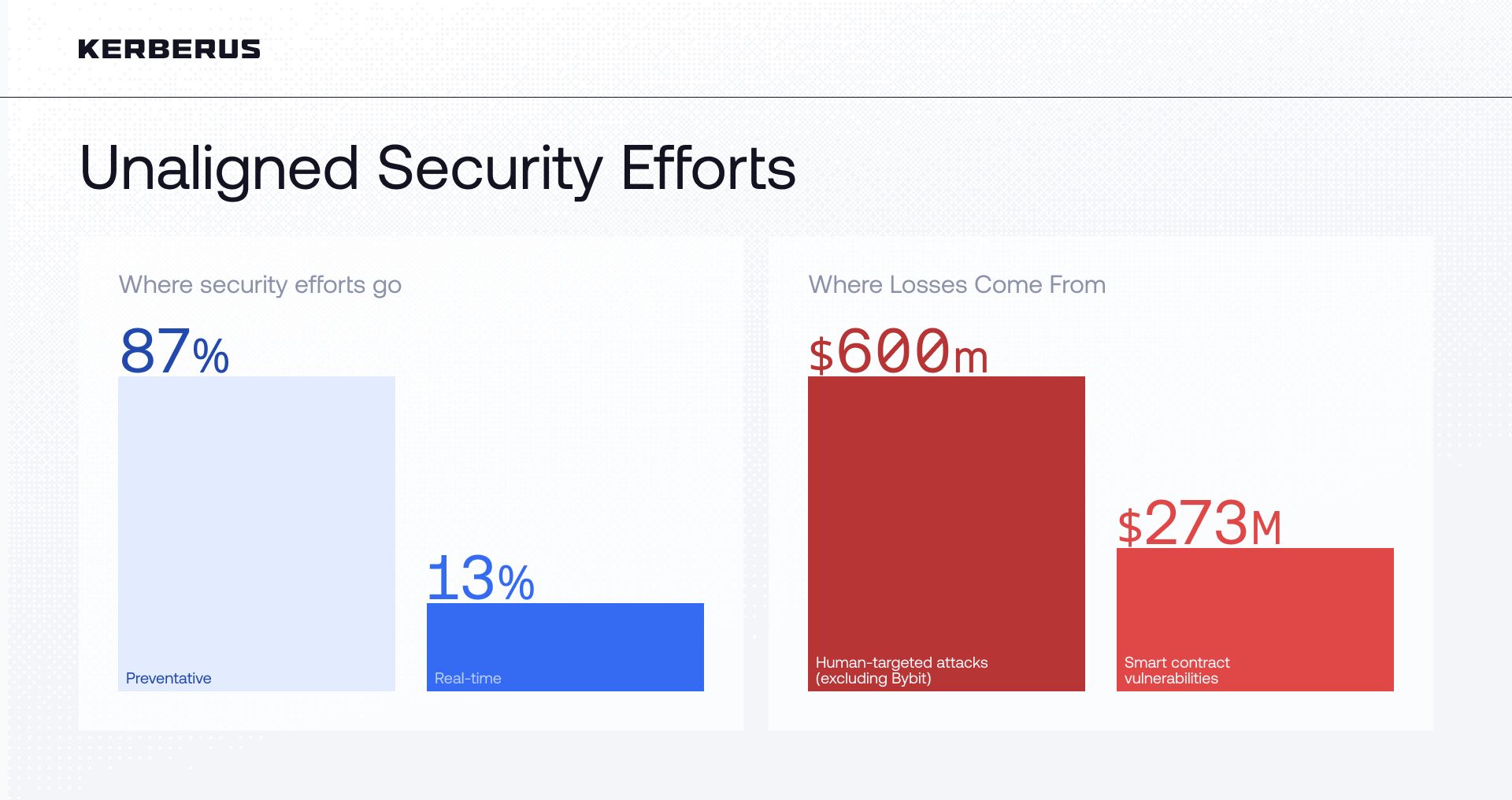
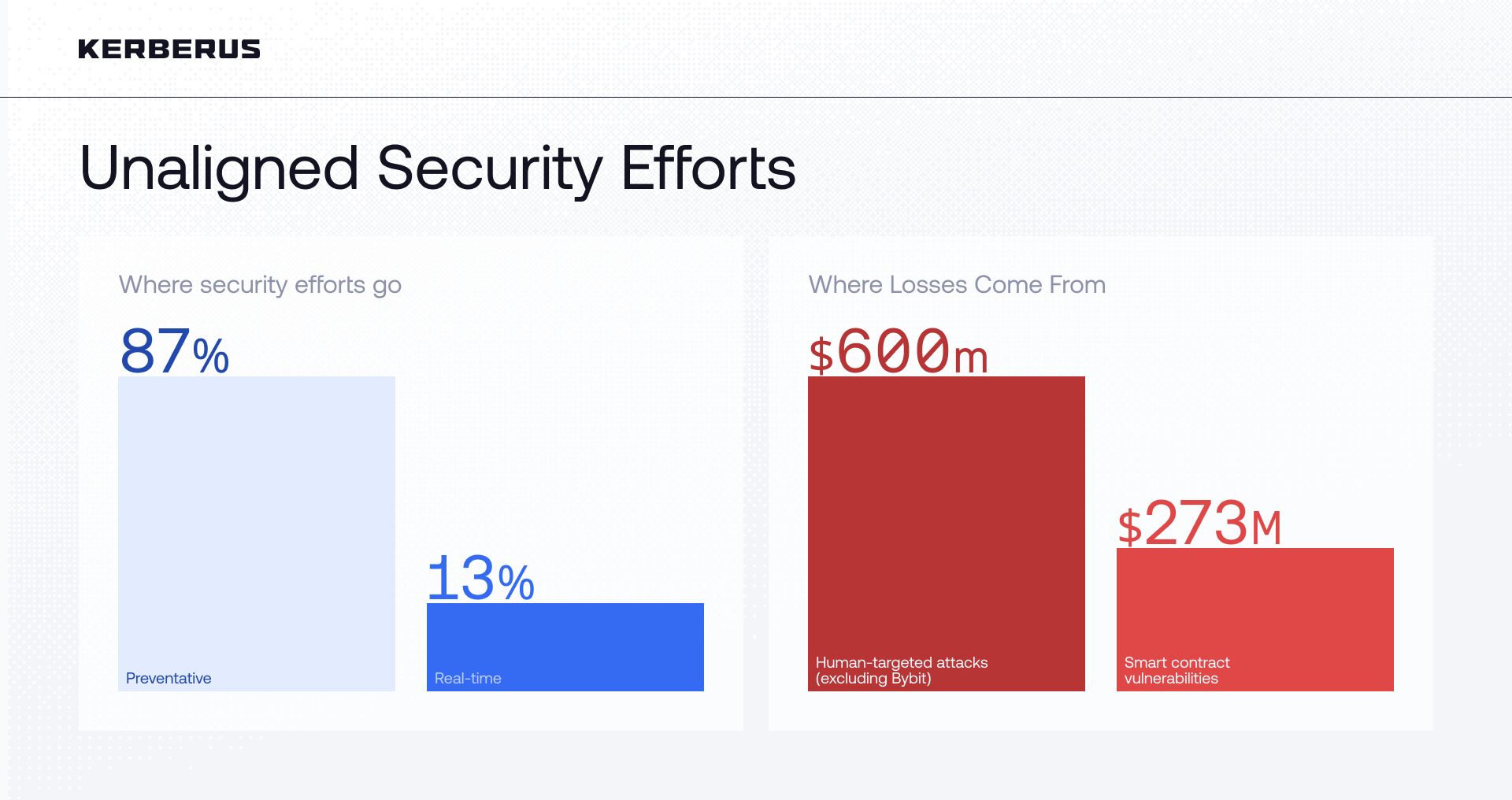
Real-time transaction protection exists in only 13% of Web3 security tools. The rest? Audits, dashboards, and cleanup after the breach
At the same time, broader cybersecurity data points to the human element as the primary failure mode: around 44% of crypto theft involves private-key mismanagement, and roughly 60% of breaches involve human error.
Put together, Solana’s security bottlenecks are:
- Program risk: bugs, upgrade mistakes, latent vulnerabilities.
- User-approved transaction risk: Any risk arising from transactions signed and executed by users’ wallets, including privileged accounts or authorities.
Audits, code reviews, and education remain essential, but they all operate outside the exact window where most Solana users are losing funds: the few seconds between a signature popup and a click on “Send”. That gap is where automation has to live.
Solana × Pocket Universe: Protection at the Point of Signature
In February 2025, Kerberus expanded Sentinel3’s real-time protection to Solana users. After acquiring its competitor Pocket Universe in August, the company rolled out the same Solana protections to Pocket Universe users in November. Pocket Universe was originally built to simulate transactions before signature, presenting outcomes in human-readable terms. Under Kerberus, simulations now run through Sentinel3’s scam intelligence and real-time risk models. The system checks transactions before you sign and blocks malicious ones.
Since January 2023, Sentinel3 has logged zero losses for its users and backs each transaction with up to $30,000 in third-party coverage.
As CTO & founder Danor Cohen notes, people get scammed “when they are rushed, distracted, or excited.” In those moments — during a mint, a drop, or a rushed swap — security has to work automatically, without expecting users to reverse-engineer every instruction.
A Turning BREAKpoint for Automated Security on Solana
Breakpoint is when the Solana community takes stock of what’s really running in production. In 2025, wallet safety is one of the central threads.
Kerberus is at Breakpoint to:
- Publish its Solana wallet-safety micro-brief, highlighting observed patterns in approximately $250M in H1 2025 Solana losses.
- Highlight how real-time, automated protection can reduce reliance on “user guesswork” during mints, drops, and hype-driven events.
- Showcase their Solana integration as a live example of transaction-level protection for millions of users.
The direction is that, for Solana to keep scaling, continuous security has to be treated like any other core piece of infrastructure.
Kerberus’ work with Sentinel3 and Pocket Universe is one concrete step in that direction. It’s production-grade and user-level protection running quietly in the background while Solana continues to grow.
The takeaway for the ecosystem:
- Growth will keep drawing adversaries.
- Wallet-level attacks will evolve as fast as on-chain innovation.
- Manual security alone will not close the gap.
Continuous, automated security has to become the default. The goal is to make it as hard as possible for users to approve unsafe transactions in the first place. That way, builders and users can focus on what they actually came to Solana for.
Ready to protect your Solana transactions? Get Sentinel3 and join 250k+ users who have experienced zero losses with real-time transaction protection. Learn more about Solana scam protection and how to protect yourself from wallet drainers.
Written by:
Alex Katz
Kerberus is a Web3 cybersecurity company protecting users across 1000+ chains with real‑time scam detection and MEV defense. Our team has led and advised security work across top crypto ecosystems since 2023.
Read more about the authorRelated Articles
See more articles
Kerberus 2025 Review: Taking Real-Time Web3 Security Mainstream
Dec 31, 2025 • 4 minutes read
Human Errors Drive Most Web3 Losses Despite Billions Spent on Security, Kerberus Finds
Nov 17, 2025 • 4 minutes read
Report: The Human Factor – Real-Time Protection Is the Unsung Layer of Web3 Cybersecurity (2025)
Nov 17, 2025 • 4 minutes read

Kerberus Acquires Pocket Universe: Uniting 200k Users in Web3 Security
Aug 21, 2025 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
