Crypto Wallet Drainers: How to Stay Safe in Web3
Learn how crypto wallet drainers work, recognize attacks, and protect your digital assets. Comprehensive guide with case studies and best practices.

Cryptocurrency has unlocked a new frontier of financial freedom, but it has also spawned major new threats in its wake. Among the most pernicious are crypto wallet drainers, malicious tools and services designed to steal the contents of a user’s digital wallet without their knowledge.
As these attacks become more sophisticated and widespread, it’s vital to understand how they work, how to spot them, and what you can do to protect yourself.
At Kerberus, we pro-actively flag and take care of Web3 threats before it threatens our users. However, it is important to be informed.
This wallet drainer guide combines the latest research and expert insights to deliver a clear, actionable roadmap for safeguarding your digital assets.
What Is a Crypto Wallet Drainer?
Simply explained, a crypto wallet drainer is a malicious program, smart contract or fake decentralized application that empties a user’s wallet after obtaining the necessary permissions.
Unlike phishing scams that steal login credentials, drainer scams exploit blockchain mechanics, particularly token approvals, to siphon assets directly.
Chainalysis defines a crypto drainer as malware or a deceptive smart contract that tricks users into authorizing unauthorized transfers. Its investigations show that, loosely defined, wallet drainers have existed for more than a decade, with one scam stealing 25,000 Bitcoin in 2011 already. However, they have become a real problem since 2021.
Today’s crypto drainer attacks range from simple scripts to sophisticated kits sold as scam‑as‑a‑service, enabling even non‑technical criminals to pull off large‑scale heists.
A security report has revealed a single drain kit has been linked to over $70 million in stolen crypto. That amount of crypto funds falling into the hands of nefarious terrorist groups like North Korea’s Lazarus group not only hurts retail investors, but also brings unneeded regulatory scrutiny to the entire space
The Rise of Drainer‑as‑a‑Service Platforms
One of the most disturbing trends is the rise of drainer‑as‑a‑service platforms, who run on a revenue‑sharing basis. Group‑IB’s research highlights Inferno Drainer, a kit that enabled scammers to drain more than $70 million from unsuspecting users.
In these ecosystems, operators develop and maintain the malicious software while affiliates deploy phishing sites and social‑engineering campaigns. Profits are shared between operators and affiliates, creating an efficient criminal marketplace.
Traditional Crypto Scams vs Wallet Drainers

Traditional crypto theft requires stealing your private keys through device hacks, compromised storage, or phishing for seed phrases.
For example: social engineering and phishing techniques like address poisoning require user error such as not checking the final transaction details, whereas a wallet drainer is a more direct and automated method of theft, often activated by clicking a malicious link.
Wallet drainers manipulate you into authorizing transactions that appear legitimate but grant unlimited access to your funds.
You unknowingly sign away wallet control while thinking you’re claiming an airdrop or connecting to a DeFi platform.
Comparison Table: Traditional Theft vs. Wallet Drainers
| Aspect | Traditional Theft | Wallet Drainers |
|---|---|---|
| Attack Method | Steal private keys/credentials | Trick into malicious permissions |
| User Awareness | Often realize theft immediately | May not notice until much later |
| Technical Skill Required | Moderate to high | Low (with DaaS platforms) |
| Recovery Possibility | Sometimes possible | Nearly impossible |
| Legal Standing | Clear unauthorized access | Technically “authorized” by signature |
| Speed of Execution | Variable | Instant upon permission grant |
| Scale Potential | Limited by access methods | Unlimited with automated systems |
Why Drainers Are More Dangerous
Blockchain technology interprets your signature as legitimate consent. Once you approve a malicious transaction, that means it cannot be undone for these reasons:
- Irreversible - Cannot be undone once confirmed
- Legally ambiguous - You technically “authorized” it
- No recourse - Your signature validates the blockchain record
- Instant execution - Assets transfer within seconds
Modern crypto drainers request permissions that appear normal for DeFi interactions but actually grant unlimited withdrawal rights.
They do the following before you realized what happened:
- automatically scan your wallet,
- identify valuable assets,
- and execute rapid theft
Let’s look in more detail:
How Crypto Wallet Drainers Work
Drainware scams leverage several technical and psychological tricks to persuade victims into transferring control over their funds.
Types and Tactics of Wallet Drainers
Different drainers employ distinct tactics, and attackers often combine several methods to maximize success.
-
Phishing and spoofed websites
Attackers create websites that mimic legitimate and popular wallets, exchanges or NFT marketplaces. Phishing pages often copy the look and feel of popular services and may even use similar domain names or SSL certificates. Victims believe they are connecting to a legitimate site and sign malicious transactions. Once a user enters their seed phrase or signs a transaction, the attackers gain immediate access.
-
Social‑engineering campaigns
Never trust everything you see on social media. That’s especially true when you have crypto. In what is called pig butchering scams, a bad actor may use a variety of methods via social media platforms like X, Discord, Tinder, Instagram, LinkedIn or Facebook to establish a relationship, whether it’s social, romantic, or all business. Once connected, they then gain the victim’s confidence over time, often weeks or months, and set them up for a scam.
No one is safe on social media, not even cybersecurity firm followers!
Darktrace documented an elaborate social‑media scam in which fake job recruiters invited victims to install a compromised project management tool. The tool included code that exfiltrated seed phrases and triggered transfers.
Another popular variation is inviting X influencers to a podcast which is usually set up in a private Telegram group, where they get convinced into installing.
-
Malicious dApps and smart contract exploits
DeFi protocols and NFT marketplaces require users to approve smart contracts to move tokens. Attackers exploit this by embedding malicious code that requests unlimited spending permissions. Trust Wallet warns that some malicious dApps hide these approvals in complex transaction signatures.
For example, users are lured to a fake or compromised decentralized application such as a Solana dApp that requests an “approval” transaction. Approving the transaction grants the contract permission to spend tokens on the user’s behalf, allowing it to drain your assets later.
-
Malware in browser extensions and mobile apps
Some drainers are packaged as browser plug‑ins or mobile wallet apps. Once installed, they log keystrokes or inject malicious scripts to hijack transactions.
Darktrace’s analysis uncovered drainers masqueraded as productivity tools or trading bots. On Windows and macOS, the malware was delivered as an installer that executed PowerShell or AppleScript to extract private keys. Fake browser extensions can also intercept Web3 calls and rewrite transaction data.
PCRisk found that one trading bot was in fact a drainer.
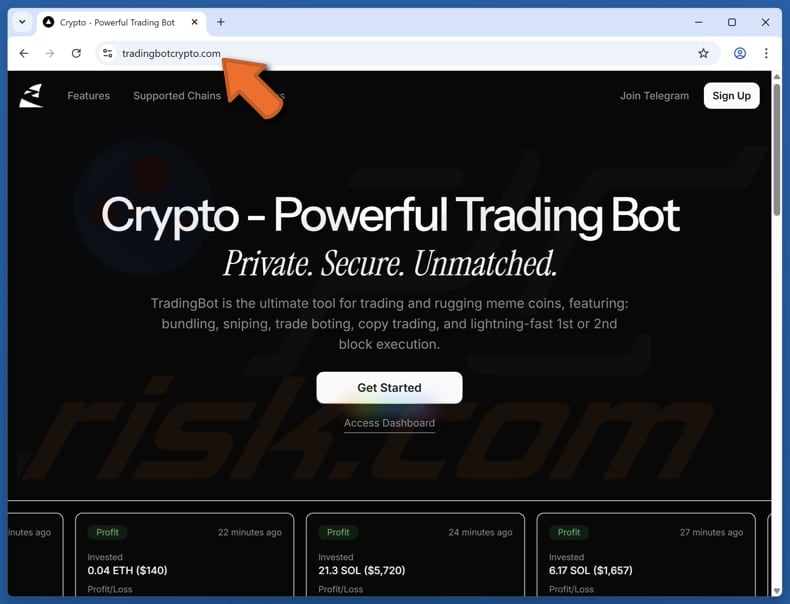
Source: PCRisk
-
Seed‑Phrase Theft and Keyloggers
Keyloggers and clipboard hijackers monitor user input to steal private keys. Other scams coerce victims into revealing seed phrases through fake customer‑support chats or “wallet recovery” forms. Once exposed, attackers import the wallet and drain funds immediately.
-
Drainer‑as‑a‑Service Programs
Drainer‑as‑a‑service platforms provide affiliates with customizable phishing templates and automated draining scripts.
Platforms like Inferno Drainer provide affiliates with pre‑built phishing pages, hosting infrastructure and payout dashboards.
Affiliates focus on driving traffic—through spam, hacked social‑media accounts or ads—while operators maintain the code. Revenue‑sharing models encourage rapid adoption, making drainer kits one of the fastest‑growing threats in Web3.
-
Address and Transaction Poisoning
Bad actors set up address poisoning and transaction poisoning scams by sending small “dust” transactions to a victim’s wallet, creating a history entry with a similar-looking address (which usually matches the first and last few characters). The victim, often in a rush or a little careless, might copy the malicious address from their history instead of the correct one for a future transaction.
-
AI and Deepfakes
With AI technology making exponential leaps in 2025, AI-generated deepfake videos and audio of well-known celebrities like Elon Musk to promote fake giveaways or investment schemes has surged, making scams more convincing. In rising cases, deepfakes now even mimic family members and friends to hook the victim.
5 Wallet Drainer Case Studies
Studying real attacks sheds light on how drainers evolve and how victims can respond.
-
Bitcoin’s First Drainer
According to Chainalysis, most drainers target Ethereum wallets. However, the advent of smart contract functionality on Bitcoin has made it a new target. Over 500,000 USD in 1000 transactions have been stolen by a Magic Eden impersonating drainer targeting Bitcoin Ordinals owners.
The first basic script automatically swept funds from users’ wallets once they unknowingly installed it. While rudimentary by today’s standards, it paved the way for more sophisticated drainers.
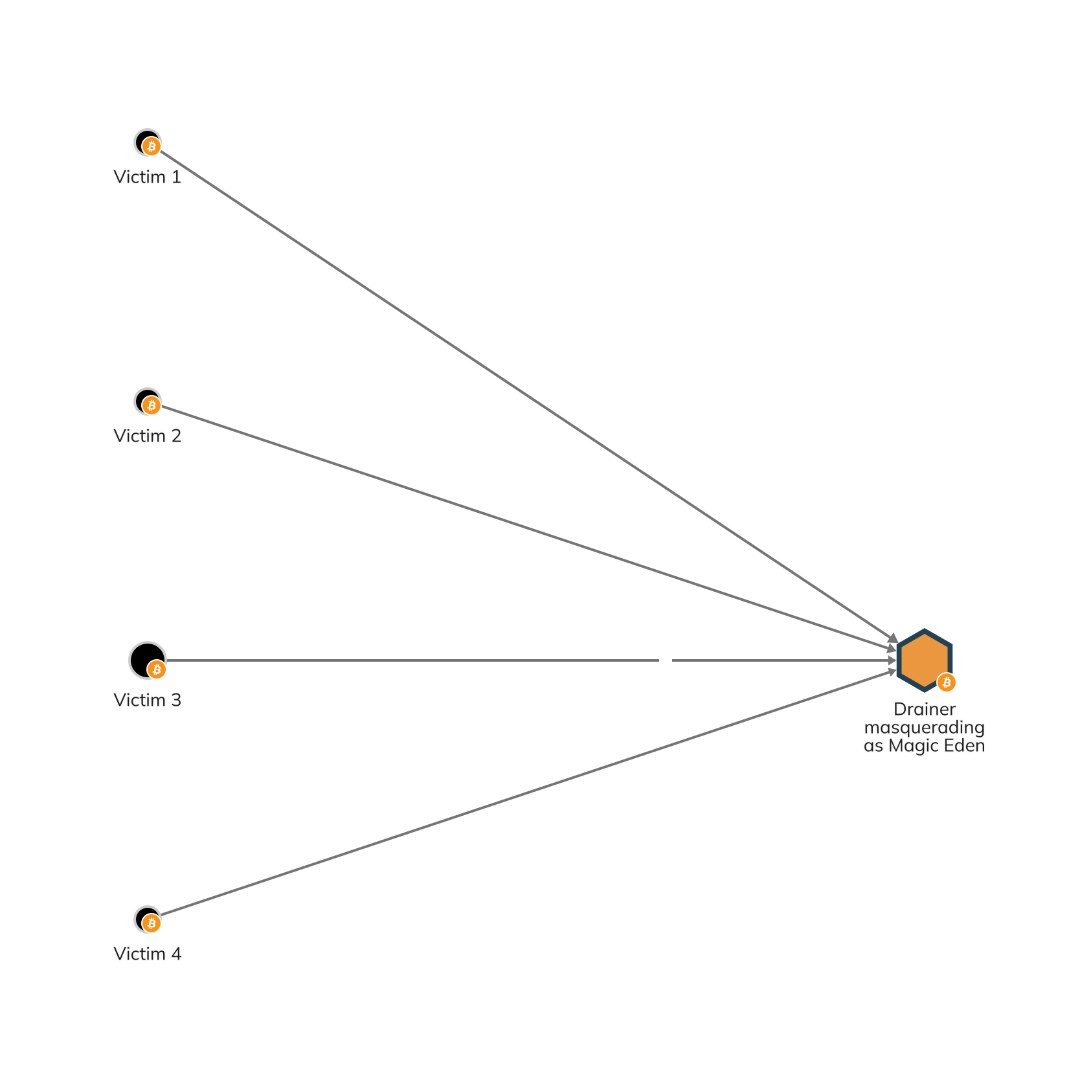
Source: Chainalysis
-
Inferno Drainer
Group‑IB’s research discovered that Inferno Drainer supported multiple blockchains and offered its affiliates customizable phishing. The service reportedly netted more than $70 million and illustrated the profitability of the scam‑as‑a‑service business model.
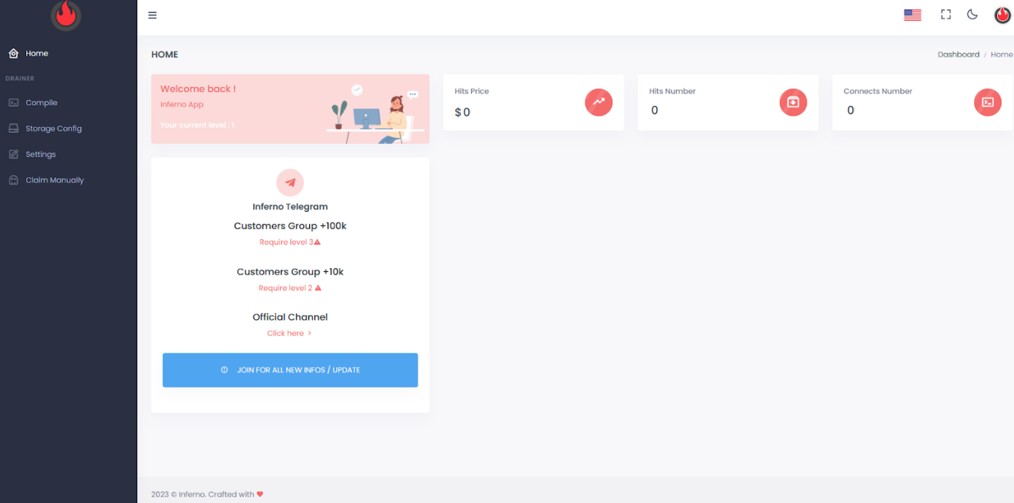
Source: Group-IB
Investigators noted that affiliates targeted DeFi investors and NFT collectors—groups known for holding valuable assets.
-
Social‑Media Scam Campaigns
- In January 2024, the SEC’s real X account was hacked, resulting in a link to a crypto drainer that tricked users into connecting their wallets to claim a fake airdrop.
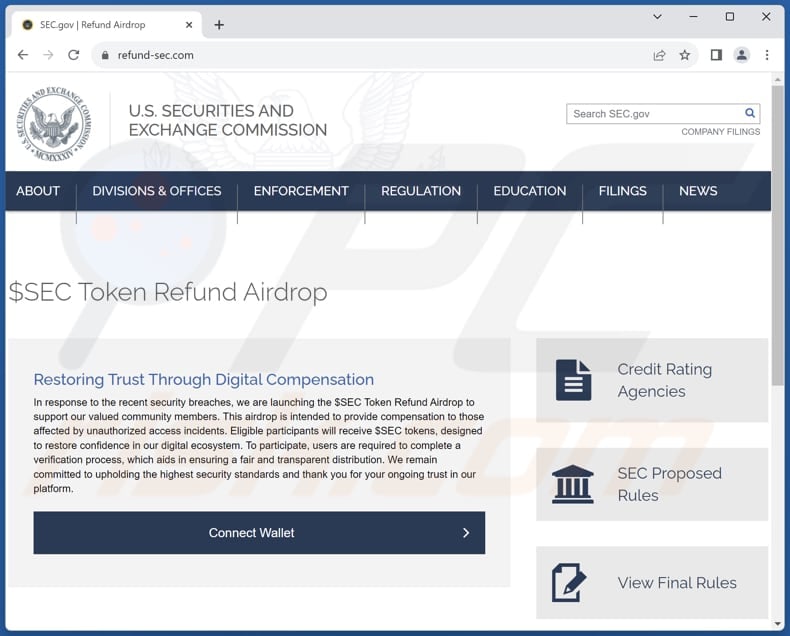
Source: Chainalysis.com
- In January 2024, CertiK’s official X (Twitter) account was hacked and used to promote a crypto wallet drainer. The attacker gained access through a social engineering phishing message sent from another already-compromised, high-profile journalist account who had over 1 million followers. After taking control, the hacker posted a fake security warning linking to a malicious RevokeCash phishing site.
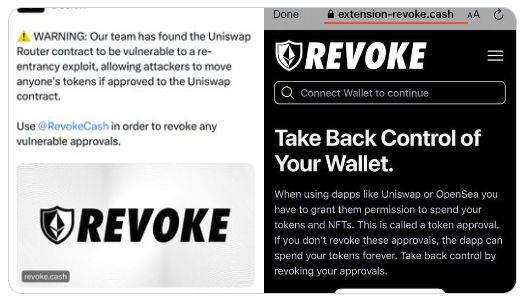
-
Darktrace analysed a scam that used fake LinkedIn job offers to distribute a Windows and macOS tool containing drainer malware. Victims were persuaded to run the installer under the pretext of taking a skills test. Once installed, the malware harvested private keys and connected to command‑and‑control servers to initiate unauthorized transactions. Darktrace provided indicators of compromise (IOCs), domain keys and YARA rules to help defenders detect the malware.
-
A Web3 full stack developer was duped by a Reddit user offering him work.
-
NFT Theft: The Bored Ape Yacht Club Attack
In a high‑profile incident reported by Kaspersky, attackers gained access to a celebrity’s crypto wallet and stole Bored Ape Yacht Club NFTs, highlighting how high‑value assets draw sophisticated attackers.
The Impact of Crypto Wallet Drainers and Phishing Scams
The financial impact of wallet drainer scams is enormous. Studies estimate that billions of dollars have been siphoned from users across multiple blockchains. And it’s getting worse, thanks to the criminal affiliate model.
Group‑IB’s research emphasizes that the phenomenon is accelerating, with more affiliates entering drainer‑as‑a‑service platforms every month. In the first two months of 2024, crypto drainers had already amassed $104 million in stolen funds.
Besides monetary loss, victims experience emotional distress and reputational damage—particularly when stolen assets include high‑value NFTs like Bored Ape Yacht Club collectibles or tokens tied to a real‑world identity.
How to Recognize a Crypto Drainer Attack
Detecting drainer scams early can prevent catastrophic losses.
Look out for these huge red flags:
-
Unusual approval requests: Transactions that request unlimited spending or unrelated permissions should raise suspicion.
-
Unfamiliar transaction signatures: Trust Wallet suggests carefully reading transaction details and ensuring the target address matches an official source
-
Suspicious URLs: Check web addresses for typos, extra characters or unusual domain endings. Always check the URL before entering your seed phrase or connecting your wallet. Phishing sites often use look‑alike domains to catch their victims.
Popular exchanges like Binance are especially targeted. Can you spot the difference between binance.com, bianance, and bînance for example?
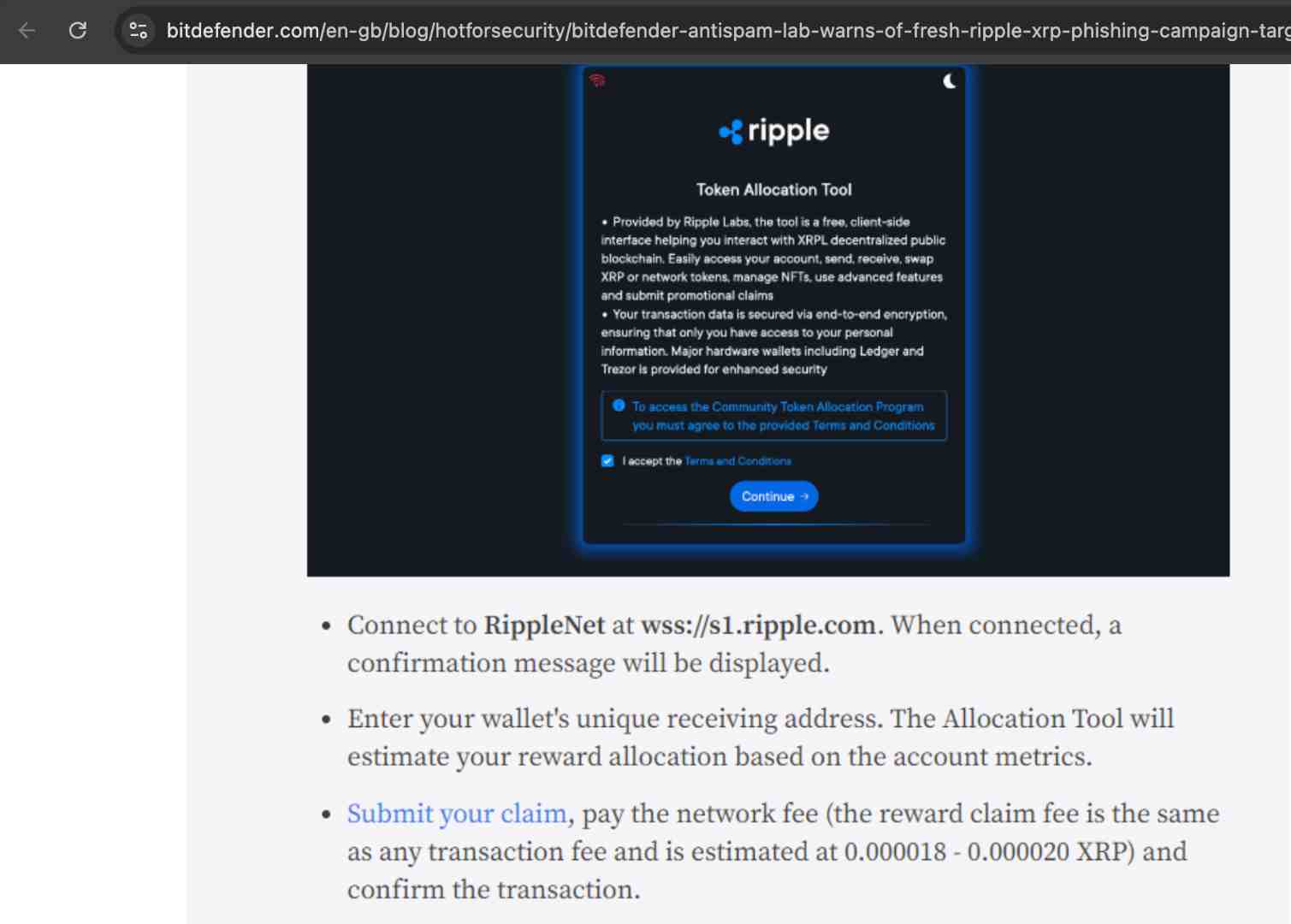
Source: SecureList
-
Unsolicited downloads or updates: Avoid installing software from links received via social media or email, especially if promised returns are high.
-
Security alerts: Take note of warnings from browsers, wallets or antivirus tools. Security software often uses shared threat indicators (e.g. Darktrace’s YARA rules) to detect drainer malware.
How To Protect Your Crypto Wallet: Best Practices
Defending your digital assets against drainer scams requires both technical safeguards and disciplined habits.
Rule 1: Use Hardware Wallets and Multi‑Wallet Strategies
-
Cold storage for long‑term holdings: Keep significant crypto assets in a hardware wallet that stays offline except when signing transactions. This isolates your private keys from malware. Despite this, cold storage is not 100% foolproof, as this Ledger user found out.
-
Separate hot and cold wallets: Keep small amounts in a “hot” wallet for everyday use and maintain a separate “cold” wallet for long‑term storage. If your hot wallet is drained, your cold wallet remains safe.
-
Create multiple wallets: Spread assets across different wallets and blockchains to minimize single points of failure.
Rule 2: Practice Secure Transaction Habits
-
Interact only with audited smart contracts: Verify that reputable security firms have audited the contract. Confirm that you are using the correct contract version.
-
Review transaction details before confirming: Wallet interfaces display the function being called and the destination address. Double‑check these details before approving.
-
Set spending limits: When approving a token for use in a dApp, set a reasonable spending cap instead of granting unlimited permissions.
Rule 3: Maintain Device and Browser Hygiene
-
Install trusted software: Download wallet apps and extensions only from verified sources. Read user reviews and watch copycat names.
-
Keep software up to date: Apply updates to your operating system, browser and wallet promptly to patch vulnerabilities.
-
Use endpoint security: Run antivirus and anti‑malware tools. Many incorporate threat‑intelligence feeds that include known drainer indicators.
-
Enable multi‑factor authentication: Adding an extra verification step on exchanges and services helps prevent unauthorized access.
Rule 4: Educate Yourself and Others
-
Follow security researchers and threat‑intel feeds: Keeping up with the latest discoveries helps you recognize new scam patterns.
-
Join reputable crypto communities: Online forums and social channels often surface new phishing sites and wallet drainer scams quickly.
-
Share knowledge: Educate your peers about secure wallet practices and the dangers of sharing seed phrases or blindly approving transactions.
What to Do After a Crypto Wallet Drainer Attack
If you suspect a drainer has compromised your wallet, act immediately:
-
Revoke token approvals: Use a permission‑management tool (such as Revoke.cash) to cancel open approvals.
-
Move remaining funds: Transfer any remaining assets to a new wallet with fresh private keys. Do not reuse compromised seed phrases.
-
Secure accounts: Change passwords and enable 2FA on exchanges and related services. Update your device’s security software.
-
Notify providers: Contact your wallet provider and report the incident. Some wallets maintain blacklists of malicious addresses and can help prevent further losses.
-
Report to authorities: File a report with relevant law‑enforcement agencies. Although crypto transactions are pseudonymous, blockchain analysis can sometimes identify attackers.
-
Consider forensic help: For high‑value thefts, engage a blockchain‑forensics firm or a cyber‑incident response team to trace stolen funds
Legal & Regulatory Considerations for Wallet Drainer Scams
Regulatory frameworks for crypto theft vary globally, and many jurisdictions are still developing comprehensive laws. Digital assets are often treated as property, giving victims a legal basis for pursuing recovery.
However, criminals move assets across decentralized exchanges and cross‑chain bridges to obscure their trail, making recovery difficult. Law‑enforcement cooperation with blockchain analytics firms is improving, and there have been successful prosecutions. Still, prevention remains far easier than recovery.
10 Notable Wallet Drainers Since 2023
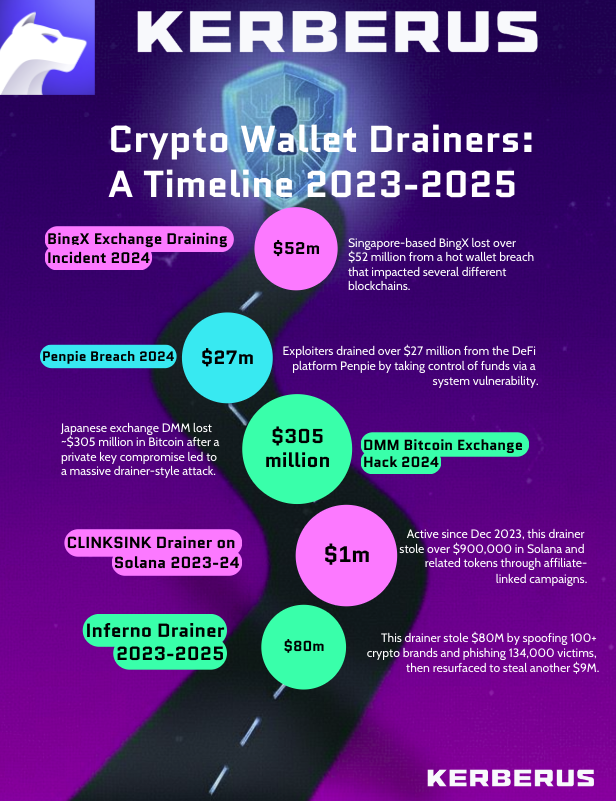
1. Inferno Drainer Campaign (2023-2025)
This infamous wallet drainer stole at least $80 million in digital assets by spoofing over 100 crypto brands and using phishing to steal from 134,000 victims before shutting down in November 2023.
However it was found this year that Inferno Drainer was still active, draining at least $9 million from over 30,000 wallets in just six months, illustrating the persistence and scale of these attacks.
2. CLINKSINK Drainer on Solana (2023-2024)
Active since December 2023, the infamous CLINKSINK drainer stole at least $900,000 in Solana and related tokens through affiliate-linked draining campaigns.
3. Orbit Chain Bridge Exploit (2023)
Hackers accessed Orbit Chain’s bridge, draining assets valued at about $82 million across USDT, USDC, DAI, WBTC, and ETH.
4. DMM Bitcoin Exchange Hack (2024)
The Japanese crypto exchange lost 4,502.9 BTC (approx. $305 million) in one of the largest-ever single-incident drainer-style attacks linked to private key compromise.
5. Penpie Protocol Breach (2024)
Exploiters drained over $27 million by taking control of funds via a vulnerability in the DeFi platform Penpie.
6. BingX Exchange Draining Incident (2024)
Singapore-based BingX lost over $52 million from a hot wallet breach that spanned several blockchains.
7. Generic Wallet Drainer Surge (2024)
In 2024, a surge in wallet drainer scams led to nearly $500 million in collective losses, with the largest incidents in August ($55.5m) and September ($32.5m).
8. CrazyEvil Traffer Group Operations (2025)
The CrazyEvil Traffer Group specialized in high-value phishing and draining attacks against influencers and DeFi professionals, leading to millions stolen through sophisticated drainer tools.
9. Monkey Drainer Activity (2023)
Linked to more than $3.5 million stolen, including high-value NFTs such as CryptoPunks and Azuki, via wallet drainer smart contracts and phishing.
10. Vanilla Drainer (2024)
Vanilla Drainer stole over $5 million since October 2024. It provides phishing software to fraudsters and takes a 15-20% commission from stolen funds. Vanilla drainware uses advanced tactics like frequently changing domains and creating new malicious contracts to bypass security systems such as Blockaid. This scam has become a major threat in crypto crime by rapidly rising after earlier drainers shut down.
The Future of Crypto Wallet Drainer Attacks
Threat actors continually adapt to new security measures. Trends to watch include:
-
AI‑driven social engineering: Attackers may use generative AI to craft more convincing phishing emails and chatbots.
-
Cross‑chain exploits: As cross‑chain bridges become more common, drainers will target them to bypass network‑specific protections.
-
Mobile‑first malware: With increasing mobile adoption, expect more malicious wallet apps on Android and iOS.
-
Improved defense tools: Industry players are developing real‑time transaction‑risk scoring, AI‑powered approval alerts and decentralized blacklist registries.
Conclusion
Crypto wallet drainers are one of the most damaging and fast-evolving threats in the digital asset ecosystem. However, with disciplined security habits, awareness of phishing risks, and proactive management of token approvals, users can significantly reduce exposure.
Secure storage, cautious transaction behavior, and informed vigilance remain the strongest defense.
Digital assets offer tremendous opportunities. Protecting them requires diligence, but with the right knowledge and industry-leading tools like Kerberus that offer real-time protection, you can navigate the Web3 ecosystem safely and confidently.
Checklist for Wallet Drainer Protection
- Educate yourself on how approvals and smart contracts work.
- Use hardware wallets and separate hot and cold wallets.
- Be vigilant against phishing attempts and unsolicited downloads.
- Limit token approvals and regularly revoke permissions.
- Keep your software up to date and use trusted security tools.
- Spread awareness—an informed community is the best defense.
FAQ
1. What is a crypto wallet drainer?
A wallet drainer is malicious code or a deceptive smart contract that tricks users into approving transactions that give attackers permission to withdraw their crypto.
2. How does a wallet drainer steal funds without my seed phrase?
Instead of stealing keys, it relies on token approval permissions you sign. Once approved, the attacker can spend your tokens directly.
3. Why are wallet drainer attacks hard to reverse?
Because the transaction is valid and authorized by your signature. Blockchains cannot undo confirmed transfers.
4. Can a hardware wallet protect me completely?
No. Hardware wallets protect private keys, but they cannot protect against malicious approvals you sign.
5. What is Drainer-as-a-Service?
It’s a service where scammers rent ready-made phishing sites and draining scripts. Affiliates promote scams, and profits are shared.
6. How do I check if I have unsafe token approvals?
Use a permission management tool such as: • revoke.cash
7. What are the most common wallet drainer tactics?
Fake airdrop sites, phishing URLs, malicious Discord/TG links, fake support chats, fake browser extensions, and social-engineering campaigns.
8. How can I recognize a malicious transaction request?
Look for “unlimited spending” approval requests or contract calls you didn’t initiate.
9. Should I ever enter my seed phrase on a website?
No. A seed phrase should only be entered directly into your wallet app on a secure device—never into websites, messages, or forms.
10. What should I do immediately if my wallet is compromised?
Revoke approvals, move remaining funds to a new wallet, secure your device, and report the incident. Do not reuse the compromised seed phrase.
Written by:
Werner Vermaak
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users. His Kerberus articles help readers understand modern Web3 threats, real-world attack patterns, and practical safety practices in an accessible, research-backed way.
Read more about the authorRelated Guides
See more guides
How to Use Phantom Wallet Safely: A Beginner’s Guide
Feb 12, 2026 • 4 minutes read

Wake Up! WEF 2026 Cybersecurity Report Sounds Alarm For Crypto Sector
Feb 11, 2026 • 4 minutes read

What is Self-Custody in Crypto? A Complete Beginner's Guide
Feb 9, 2026 • 4 minutes read

Pig Butchering Romance Scams: How to Protect Your Crypto
Feb 8, 2026 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
