Report: The Human Factor – Real-Time Protection Is the Unsung Layer of Web3 Cybersecurity (2025)
Only 13% of Web3 security providers offer real-time protection. Learn why human-targeted attacks cause $600M losses and how real-time solutions prevent them.
Executive Summary
Key Takeaways:
-
Human behaviour is the primary Web3 risk: 44% of crypto thefts involve private key mismanagement, and broader cybersecurity data shows 60% of breaches are caused by human error.
-
Real-time protection is limited: The majority of providers offer preventative security, while real-time solutions only account for 13% of the market.
-
Audits safeguard protocols, but not user-level risks: 90% of hacked smart contracts passed security audits, with over $17 billion drained from audited protocols to date.
-
Training alone is insufficient: Phishing click rates remain at 7–15% even after rigorous security training. Rates among everyday users are likely much higher, with non-trained people much more prone to being scammed at least once in their lifetime.
-
Real-time protection complements audits: While audits validate legitimate contracts, real-time solutions such as Kerberus Sentinel3 actively safeguard users against illegitimate contracts and malicious websites at the moment transactions are attempted in real time.
-
Effectiveness of real-time tools: While only 13% of providers offer real-time protection, high-quality solutions like Kerberus Sentinel3 show 99.9% detection and zero losses for users since 2023. Effectiveness varies widely, and poorly performing tools can erode trust. With phishing and social engineering causing $600M losses in H1 2025 (37% of the adjusted total), high-quality real-time protection is critical to reduce ongoing Web3 losses.
Introduction: The Paradox of Progress
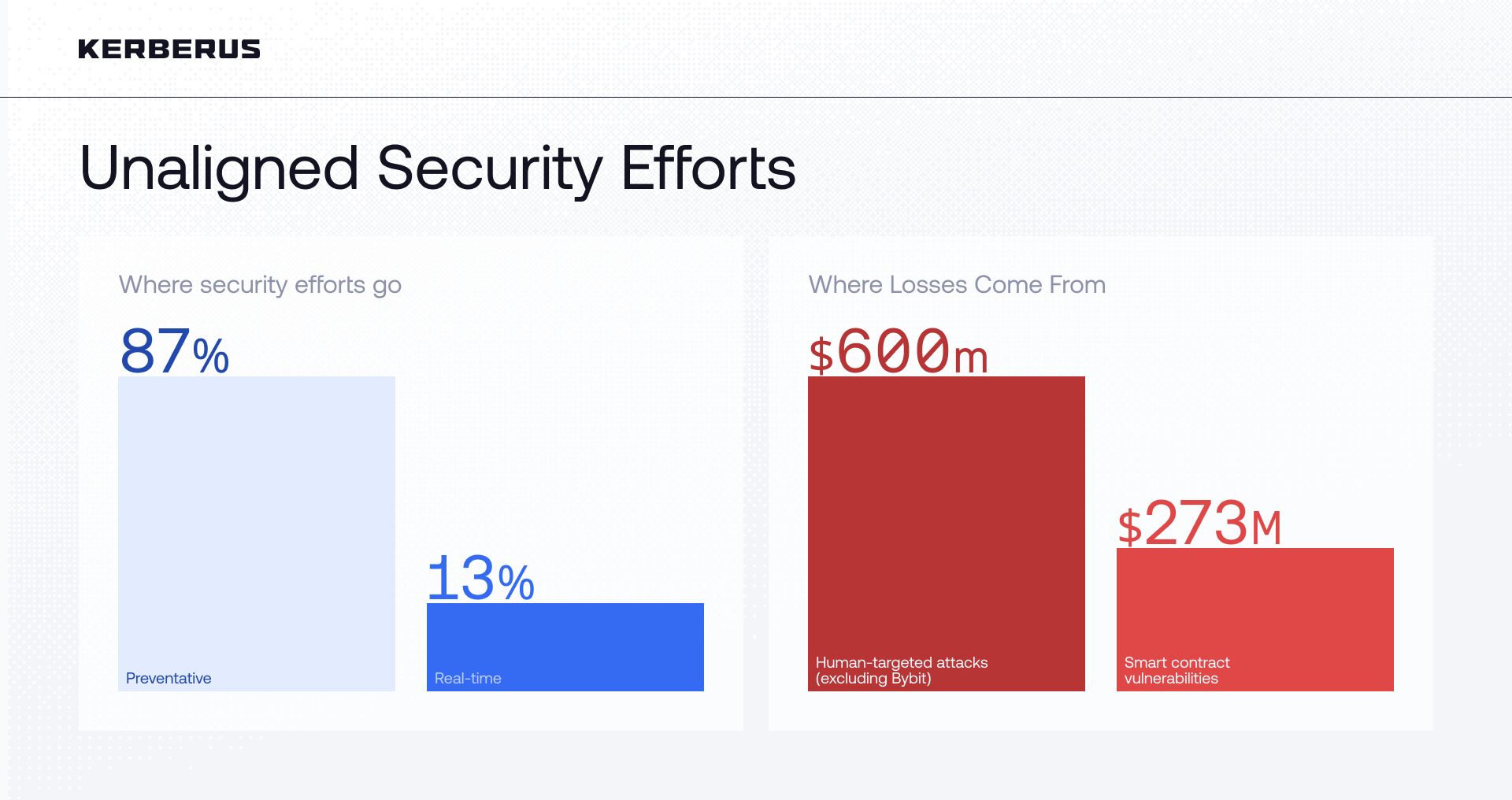
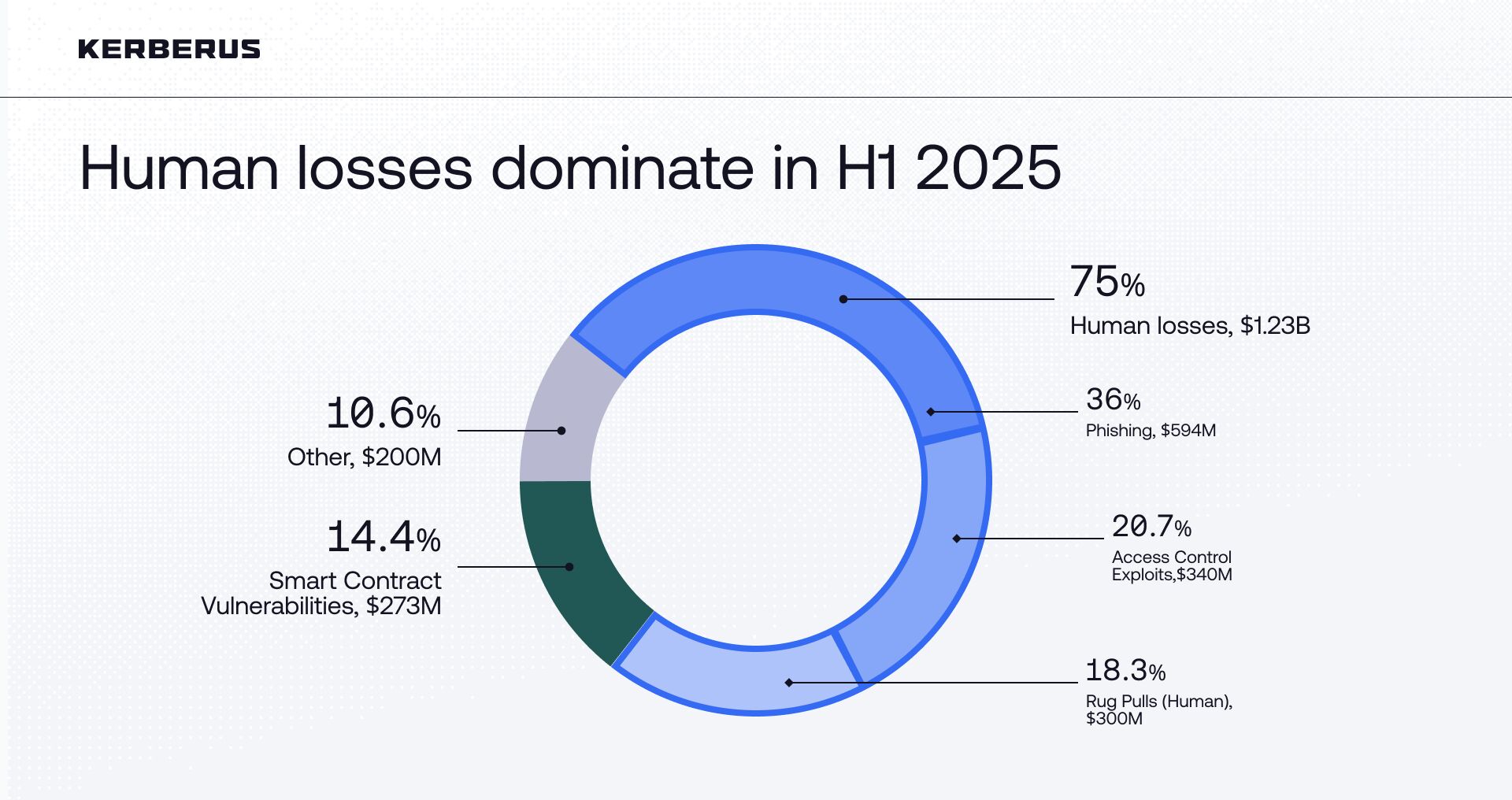
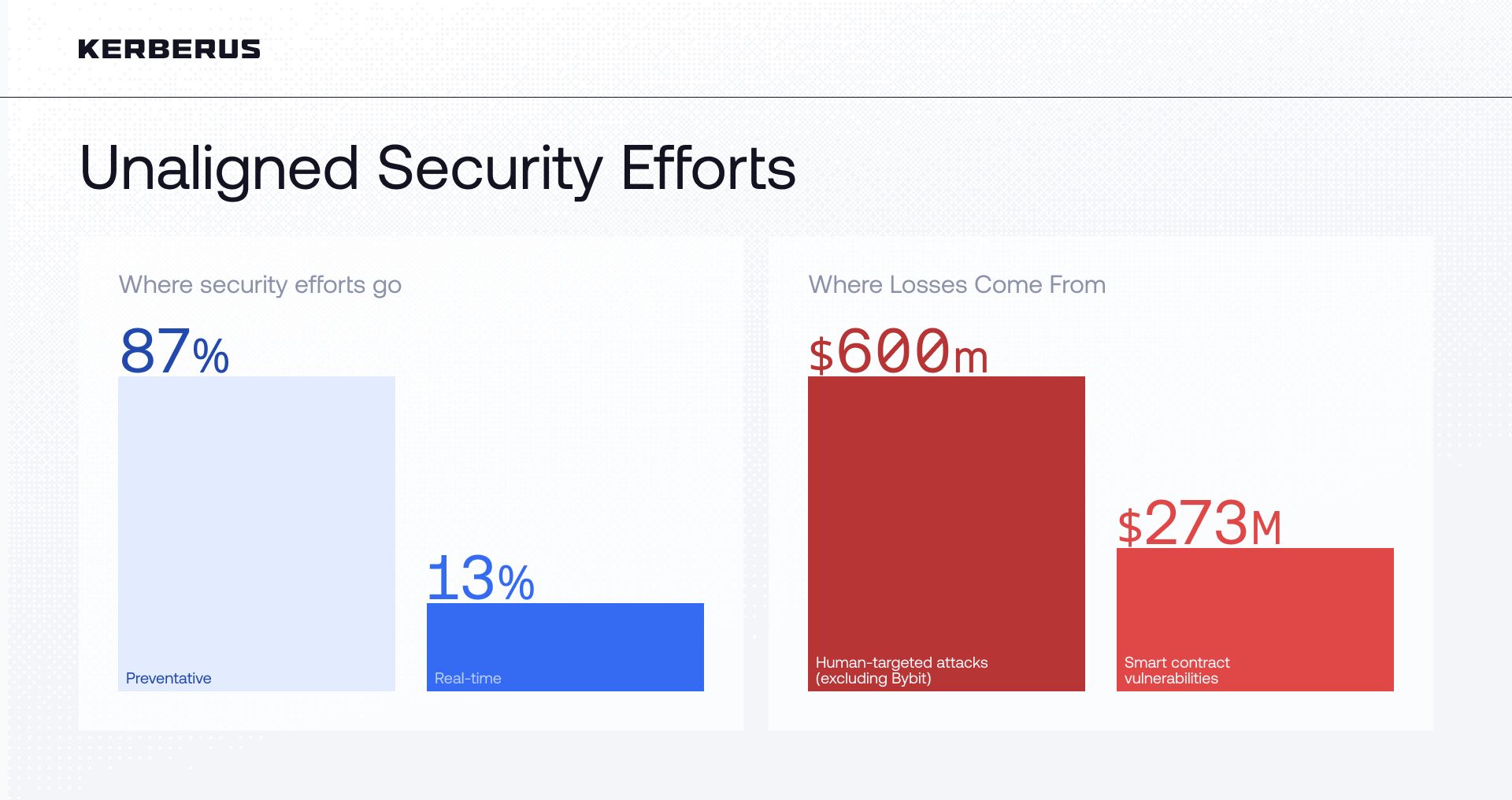
Web3 companies spent record-high amounts on improving their security in 2025, yet investors lost more than $3.1 billion1 to hacks and scams in the first half of the year - a total exceeding all of 2024 combined. This total includes the single largest crypto heist in history: the Bybit exchange compromise2 (worth $1.46B). Excluding this outlier, human-targeted attacks such as phishing and social engineering accounted for $600M, or 37% of the remaining $1.64B in losses.
These human-targeted attacks remain the most structurally dangerous vector in Web3: they scale with user growth, bypass technical controls entirely, and consistently cause losses that preventative security models cannot prevent.
The disparity highlights a fundamental challenge: while billions in funding flow into smart contract audits, bug bounties, monitoring systems, and code reviews, attackers increasingly exploit users directly at the transaction level in real-time. Audits and monitoring improve protocol-level safety, but current market solutions that deal with human-targeted attacks in real-time are not only disproportionate in number but also vary widely in quality - some tools generate false positives or miss threats, which can reduce user trust and limit their effectiveness.

For example, in April 2025, an elderly US investor lost $330 million3 in Bitcoin through social engineering alone. The attacker gained access to the victim’s wallet through direct manipulation, without exploiting any technical vulnerabilities. This illustrates the devastating impact that behavioural exploits can have on high-value holdings.
As adoption grows (Web3 reached 820 million active wallets4 in 2025, with 59% now in self-custody5), security models must address both technical and human risk vectors. Current systems protect protocol integrity but place undue burden on users to navigate complex threats in real time, leaving gaps that can be mitigated with complementary real-time protection.
Most losses don’t happen because users are careless. They assume people can evaluate complex threats instantly and accurately under pressure. In reality, even experienced users face moments of distraction or cognitive overload. The problem isn’t human weakness; it’s that our systems fail to adapt to how people actually think and act. The current model treats these failures as user errors - the classic “DYOR” (Do Your Own Research) ethos - even though they’re predictable outcomes of how attacks work.
The Human Weak Link
The data on crypto losses point to human behavior as the primary attack vector. Around 44% of crypto thefts6 in 2024 were caused by private key mismanagement, and another study found that 60% of breaches7 involve human error.
Attackers use several methods that bypass code security entirely:
-
Phishing attacks: Fake websites or compromised platforms trick users into entering seed phrases or approving malicious transactions. Attackers also exploit hacked social accounts from platforms such as X, Discord, Telegram, and others to impersonate projects, airdrops, founders, project representatives, or support teams. These tactics leave everyday users with very limited ability to defend themselves. Learn more about crypto wallet drainers and how they work.
-
Clipboard attacks: Malware silently replaces copied wallet addresses with attacker-controlled ones during the paste operation.
-
Misdirected transactions: Users send funds to wrong addresses or incompatible networks due to complex formatting and multiple chain options.
-
Malicious dApps: Wallet drainers disguise themselves as legitimate applications, airdrops, or reward claims to gain approval for fund transfers.
All of these attacks target specific moments where users can’t evaluate threats properly. Someone checks their wallet while distracted by work, or sees an urgent message claiming their account will be frozen; someone else approves a transaction at the end of a long day when they’re tired.
The industry’s response has been to pile on warnings and verification steps, but this often backfires due to a phenomenon known as “Security Fatigue”. People get used to approving alerts and measures, but because so many of them are false alarms that just slow them down, their decision-making capacity declines under the constant cognitive load.
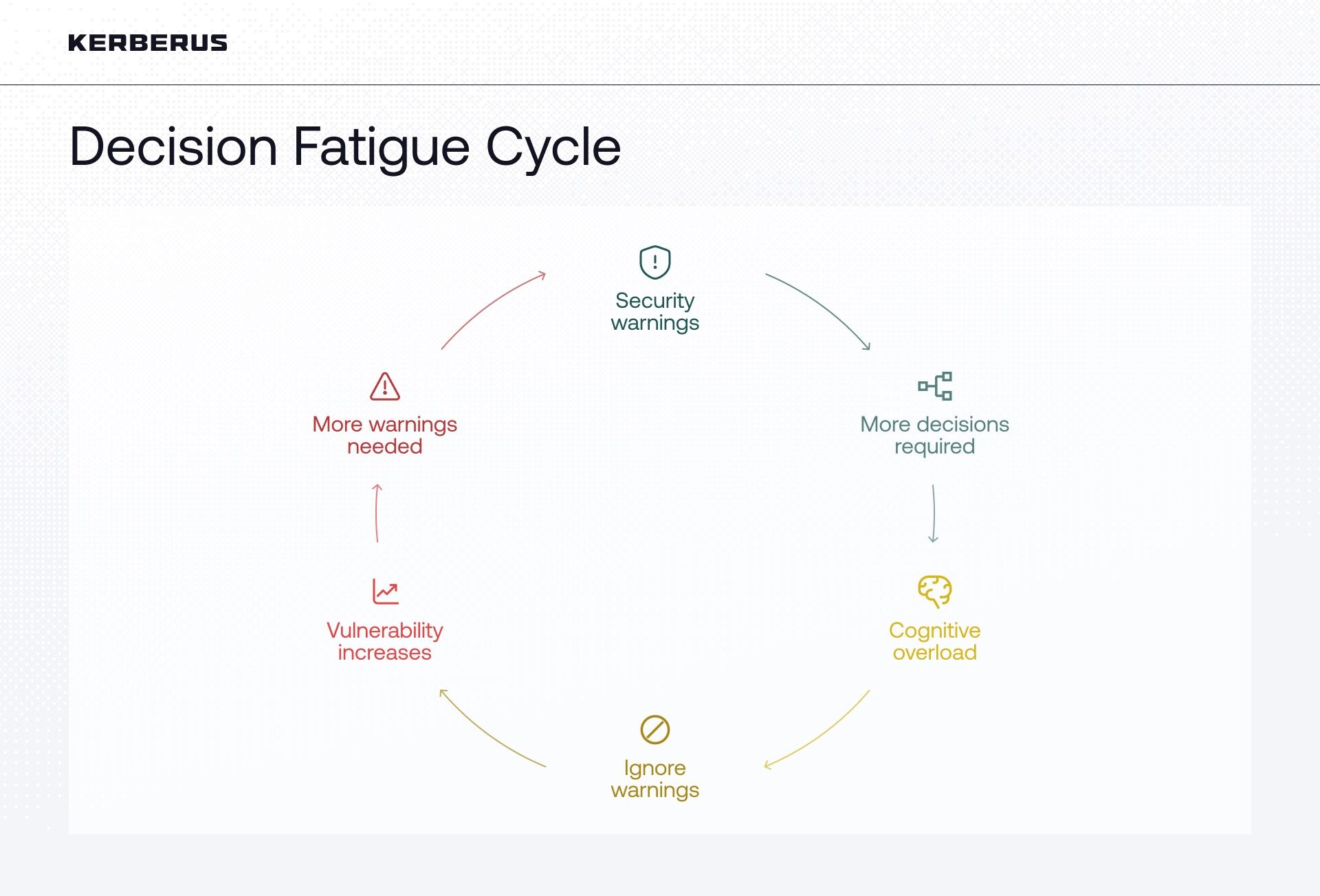
This makes protection harder over time. Users must decide about every interaction, verifying URLs, checking contract addresses, confirming transaction details, reviewing token approvals, updating passwords, and enabling authentication. In turn, the brain conserves energy by defaulting to the easiest option, which in security contexts means clicking “approve” or ignoring warnings.
The obvious solution would be to train users better. If people fall for phishing attacks, teach them to recognize fake websites. If they approve malicious transactions, show them what red flags to watch for.
The industry has invested in this approach through training programs, security guides, and awareness campaigns. Despite the effort, studies have shown that phishing click rates stayed between 7% and 15%8 even after rigorous training. The investor who lost $330 million protected Bitcoin successfully for seven years before a single phone conversation exploited a moment of trust.
Another study9 of 19,500 healthcare employees found that annual phishing-awareness training had no meaningful impact on click-through rates, and post-failure training produced only small, short-lived improvements. If training is this inefficient in a well-structured workplace, Web3 users - who face faster-moving scams, have no institutional support, and make high-stakes approvals on their own - clearly require more than just education.
Preventative Security: Important But Incomplete
The Web3 security market largely focuses on protocol-level integrity. Companies invest billions in smart contract audits, bug bounty programs, and monitoring systems that verify code quality and track blockchain activity. These measures can prevent technical exploits, but still leave users exposed to their own fallibility.
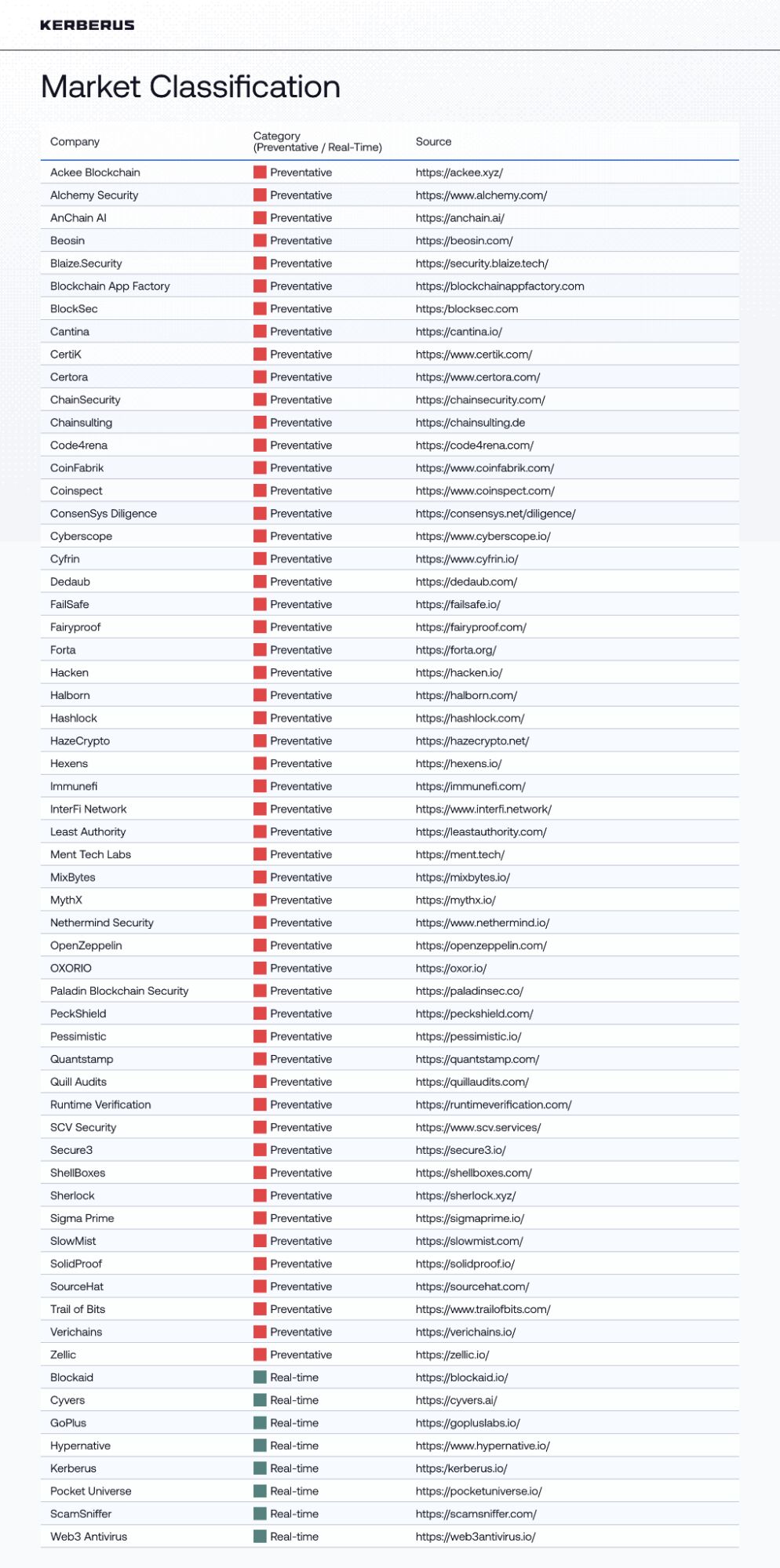
To understand how Web3 security solutions protect users, we reviewed 61 active Web3 security providers (see Appendix Item A), analyzing publicly available information on their products, services, and deployment methods. Each company was classified as Preventative, or Real-Time, based on when and how their solutions intervene:
-
Preventative: Pre-deployment and ongoing audits, post-incident analysis, bug bounties, and reporting, real-time monitoring, and alerts.
-
Real-Time: Direct intervention at the wallet or transaction level to prevent losses before transactions are approved, including phishing detection, malicious dApp blocking, and transaction scanning.
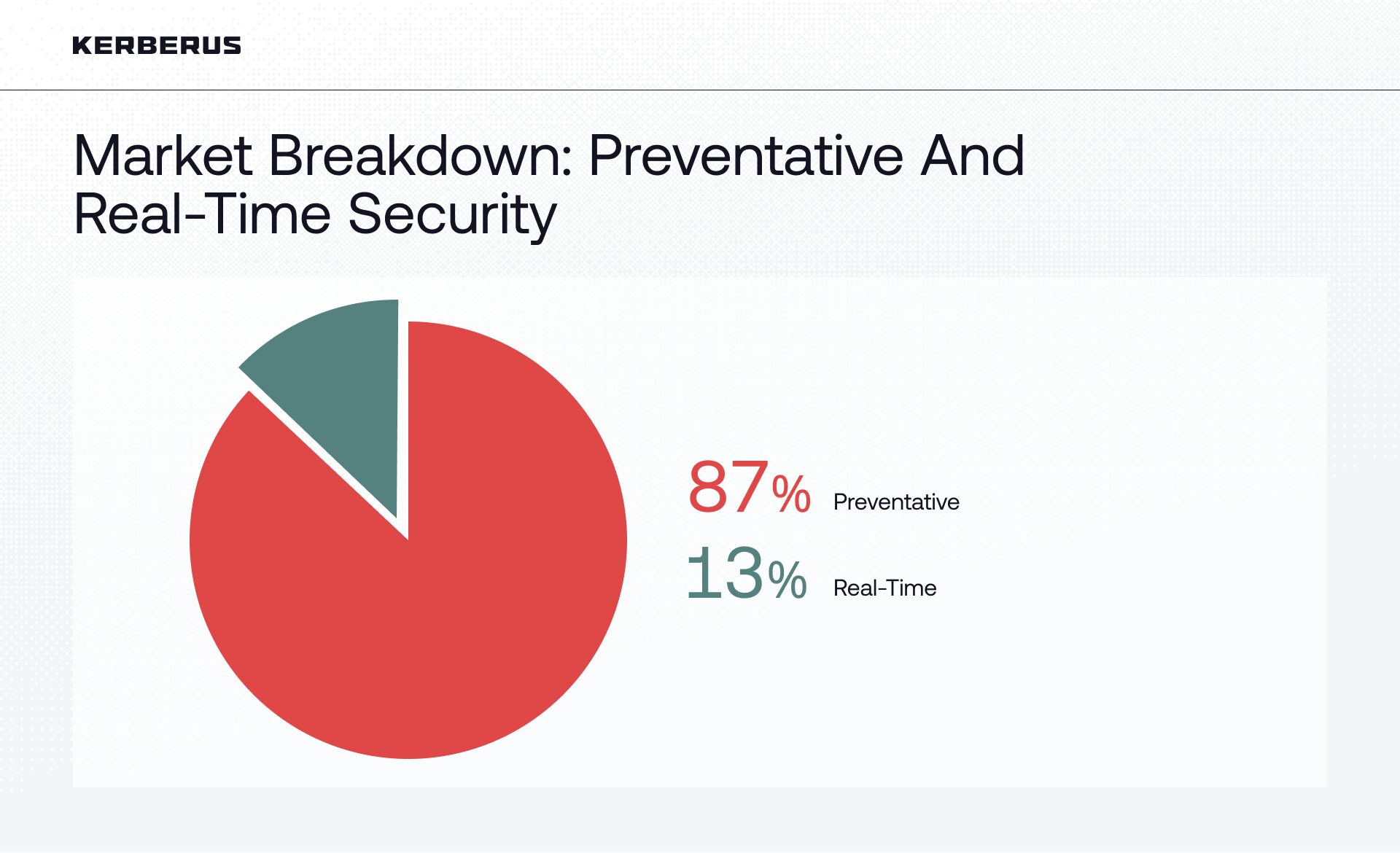
The research found that only 13% of Web3 security companies provide real-time protection to users, while the majority (87%) offer preventive protection.
Notably, 90% of exploited smart contracts10 had already passed security audits. This statistic reflects the reality that audits focus on validating legitimate codebases, whereas many real-world losses stem from illegitimate contracts, fraudulent websites, and social-engineering vectors - areas where audits are not designed to provide protection.
This imbalanced distribution is one of the main reasons for the record number of user fund losses this year. For more insights on how human behavior drives Web3 losses, see our analysis on human behavior and Web3 losses.
Case Example: Kerberus Sentinel3
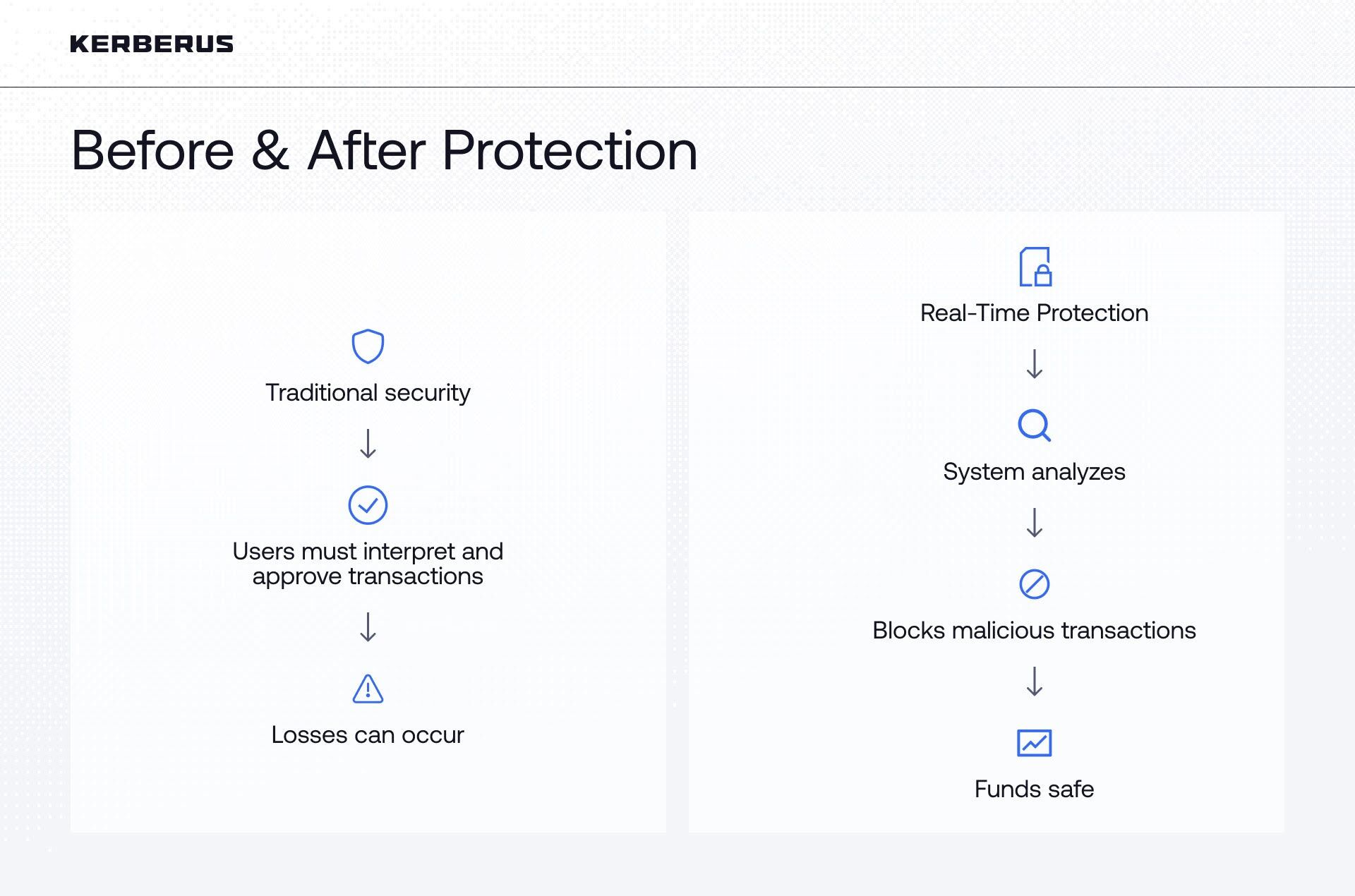
To illustrate how real-time protection works in practice, Kerberus Sentinel3 offers one example of transaction-level defense. The solution is a browser extension that scans Web3 sites and analyzes transactions before users approve them - performing scans in less than 1 second for legitimate sites and up to 10 seconds for scam sites.
The protection works in two stages based on user actions. When someone connects their wallet, the system runs a quick scan to flag obvious threats. The more comprehensive evaluation happens when users attempt to approve transactions or sign requests. At this point, the extension examines transaction data for malicious patterns or suspicious behavior. Detected threats trigger an automatic block with an alert. Legitimate transactions proceed without interruption.
Performance metrics recorded over the last two years show a 99.9% detection rate with no losses for users. This contrasts with other real-time tools in the market, which often deliver inconsistent results and can produce false positives that reduce user trust. The platform includes third-party coverage up to $30,000 per transaction and supports all EVM-compatible chains, and Solana. Learn more about Sentinel3’s transaction coverage.
Kerberus provides protection at the transaction level, a layer focused specifically on identifying and blocking illegitimate or malicious contracts and phishing-driven interactions—threats that sit outside the remit of audits or protocol-level monitoring. Rather than relying on users to identify threats during high-pressure moments, automated systems perform threat assessment during the approval window.
Why Focus Needs To Shift Toward Real-Time Security
The security model needs to match how people use Web3. Users don’t carefully research every protocol before interaction. They discover projects through social media, follow links from Discord servers, mint NFTs during drops, and claim airdrops from announcements. These activities happen fast, often on mobile devices, frequently during moments stolen from work or daily life.
With high-quality real-time protection, users don’t need to slow down, verify URLs manually, or interpret technical warnings. Someone clicks a phishing link, attempts to connect their wallet, and automated systems intervene before any approval happens. The system only interrupts users when real threats exist, leaving legitimate transactions alone. Lower-quality tools, however, may trigger unnecessary alerts or miss phishing attempts, highlighting the importance of deploying solutions that are both accurate and trusted.
Beyond preventing individual losses, real-time protection affects Web3 adoption at scale. Every user who loses funds to a scam tells others to avoid crypto. Every successful phishing attack generates social media warnings that reach hundreds or thousands of potential users. Each loss creates ripples that keep multiple people out of the ecosystem. When protection stops these losses, it preserves the trust that brings new users and keeps existing ones active.
Compare this to traditional finance, and the gap becomes obvious. Credit card companies don’t educate consumers about how to spot fraudulent charges. They monitor transactions automatically and block suspicious activity in real time. Users trust the system because protection works. By contrast, Web3 asks users to take on security responsibilities that don’t exist anywhere else in finance.
To close that gap, we need protection that works the way users expect it to — quiet when everything’s fine, immediate when threats appear, and effective without any additional training.
Conclusion: The Road Ahead for Web3 Security
Web3 built an impressive security infrastructure around only one of the problems. Billions went into auditing code and monitoring blockchains while users kept losing money to phishing links that led them to fake websites. Moving from traditional banking didn’t just shift control from banks to users — it also threw out decades of anti-fraud systems, processes, and expertise, leaving end users to handle threats on their own. The pattern repeated because the industry treated security as a technical challenge when it’s actually a human one.
Of the $3.1 billion lost in H1 2025, smart contract bugs accounted for around $275 million (as per the same report1). By contrast, human-targeted and operational attacks (including wallet compromise, private-key leaks, phishing, and social engineering), accounted for the largest shares of losses - but the headline view is materially influenced by the Bybit compromise ($1.46B). Including the Bybit event, human-targeted incidents represented roughly 59% of H1 losses; excluding it, those incidents total about $600M - or roughly 37% of the adjusted H1 total ($1.64B). We include both figures to be transparent about outlier effects while still demonstrating that user-targeted attacks remain a critical risk.
This presents a clear disparity when we find that 13% of security providers provide real-time transaction-level solutions. This imbalance shows why real-time, transaction-level protection is essential: the most damaging attacks occur at the moment users approve transactions, and effective solutions intervene directly at this critical moment to safeguard users in real time.
Web3 won’t reach mainstream adoption until security works like people expect it to. Nobody’s going to manually verify every URL or learn what “setApprovalForAll” means. They want protection that’s invisible when everything’s fine and automatic when something’s wrong.
Turning Insights into Action
To address the gaps highlighted in this report, organizations should consider the following actions:
-
Prioritise real-time protection: Organisations should expand transaction-level defenses that automatically detect and block threats, reducing reliance on individuals to identify scams themselves.
-
Establish industry benchmarks: Define standards for detection rates, response times, and coverage guarantees, and clarify the difference between transaction simulation (user decides) and active threat blocking (system decides).
-
Integrate protection into user workflows: Build threat detection directly into wallet applications or form partnerships with security providers to ensure real-time defense at the point of transaction.
Appendix: Market Classification Table
Note on outliers: H1 2025 totals include the Bybit exchange breach ($1.46B), which substantially affects headline shares between human-targeted and code-based losses. Excluding Bybit clarifies the impact of extreme events on aggregate proportions.
Ready to protect your Web3 transactions with real-time security? Get Sentinel3 and join 250k+ users who have experienced zero losses with 99.9% detection rate and $30,000 coverage per transaction.
Footnotes
-
Hacken. The Hacken 2025 Half-Year Web3 Security Report. https://hacken.io/insights/h1-2025-security-report/ ↩ ↩2
-
Coindesk. Bybit Loses $1.5B in Hack but Can Cover Loss, CEO Confirms. https://www.coindesk.com/business/2025/02/21/bybit-experiences-usd1-46b-in-suspicious-outflows-zachxbt ↩
-
Cointelegraph. $330M Bitcoin social engineering theft victim is elderly US citizen. https://cointelegraph.com/news/elderly-us-victim-loses-330m-bitcoin-in-social-engineering-theft ↩
-
Coinlaw. Cryptocurrency Wallet Adoption Statistics 2025. https://coinlaw.io/cryptocurrency-wallet-adoption-statistics ↩
-
Ibid. ↩
-
Chainalysis. Crypto Crime Report 2024. https://go.chainalysis.com/crypto-crime-2024.html ↩
-
Verizon. 2025 Data Breach Investigations Report. https://www.verizon.com/business/resources/reports/dbir/2025 ↩
-
arXiv. Anti-Phishing Training Still Does Not Work. https://arxiv.org/abs/2506.19899 ↩
-
The University of Chicago. Understanding the efficacy of phishing training in practice. https://people.cs.uchicago.edu/~grantho/papers/oakland2025_phishing-training.pdf ↩
-
Olympix. Web3 Security Crisis: Why 90% of Exploited Smart Contracts Were Audited And What You Can Do About It. https://olympix.security/blog/web3-security-crisis-why-90-of-exploited-smart-contracts-were-audited-and-what-you-can-do-about-it ↩
Written by:
Alex Katz
Kerberus is a Web3 cybersecurity company protecting users across 1000+ chains with real‑time scam detection and MEV defense. Our team has led and advised security work across top crypto ecosystems since 2023.
Read more about the authorRelated Articles
See more articles
Kerberus 2025 Review: Taking Real-Time Web3 Security Mainstream
Dec 31, 2025 • 4 minutes read
Scaling Solana Safely: Automated Defense for Programs, Authorities, and Wallets
Dec 10, 2025 • 4 minutes read
Human Errors Drive Most Web3 Losses Despite Billions Spent on Security, Kerberus Finds
Nov 17, 2025 • 4 minutes read

Kerberus Acquires Pocket Universe: Uniting 200k Users in Web3 Security
Aug 21, 2025 • 4 minutes read
Install once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.
